Many corporations, companies, firms, and other institutions of different kinds of activity need to control access to their computer networks, devices that store information, and to the information itself. In future this problem can be solved by means of inventing new devices. These devices will let working only those people, whose voice, fingerprints or the retina picture match those in the database. However, because of comparatively high prices of these devices, applications, which limit the user access to devices and I/O ports, are used to protect the information. Such applications also let you protect the corporate computer networks from the influence of harmful viruses.
Applications limiting the user access to devices and ports are not only complicated in development but also require special treatment while testing.
Contents
- 1. Application controlling user access to devices and I/O ports.
- 2. Specific of testing applications controlling user access to devices and I/O ports
- 3. The common check-list for test performing
- 4. Conclusion
1. Application controlling user access to devices and I/O ports: What is the difficulty in testing?
Difficulty in testing follows directly from the application specificity and contains several aspects:
- The title of the article includes the information about the first problem – the variety of devices and I/O ports. The difficulty is caused by variety of devices on the world market. It is too hard to check the interaction with all of them. But each device has its own driver that can be not compatible with ours.
- The application must contain a driver. The driver needs to be tested on real computers. This can be accompanied by system failures and dump gathering. On different operating systems, the driver can act differently. It follows that it is necessary to check the work of the application on different systems thoroughly.
- There is a high probability of error appearing during the interaction with various applications: with applications that also work with devices; with analog products or different device managers; with antiviruses.
2. Specific of testing applications controlling user access to devices and I/O ports
2.1. List of supported devices and ports
Let’s take a look at the list of supported devices and ports and also discuss how to check their accessibility or inaccessibility for users. The list can be extended by non-essential devices such as camera, video camera, mobile phone, etc.
The list of devices:
| Device Class | Device |
| Disk drive device class | Usb – flash |
| External hard drive | |
| CDROM device class | DVD-ROM |
| Image device class | Scanner |
| Web-camera | |
| USB device class | Printer |
| Usb-hub | |
| Mouse device class | Usb-mouse |
| Keyboard device class | Usb-keyboard |
| Bluetooth device class | Usb-bluetooth |
The list of ports:
- COM port
- LPT port
- USB port
It should be mentioned that testing cannot come to anything more than checking the denying of access to one scanner or printer or other device. Testing can be considered full-fledged if the interaction with the devices of the same type but different manufacturers is checked.
2.2. Check for disabling/enabling of the device/port
To check the disabling of the specific device, it is necessary to connect it to the computer, wait till the system informs about the end of installation and check the device availability in the Device Manager.
The application under consideration can be the cause of Explorer.exe failure. After that it is impossible to check the device availability in the Device Manager. The Driver Install Tool utility can help in this situation. This utility is similar to Device Manager and displays all devices and ports of the system.
After you made sure that the disabled device is absent in the list of devices in the Device Manager, you can start checking the access. The procedure of access limitation is individual for each project and depends on its specification. One of the well-known ways is to use the rule for access limitation to the specific device or the class of devices.
The class can be defined with the help of Device Manager in the following way:
- Select the necessary device in the device tree-view:
- Right click on it. In the right click menu, select Properties.
- On the Detail tab, choose Device Class in the drop-out list.
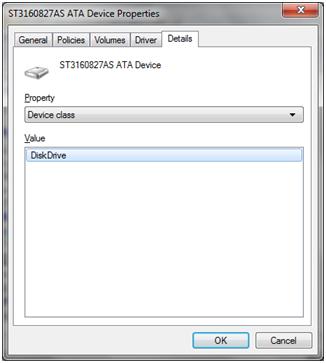
In this case, the access can be limited for local and domain users or for the whole computer. While checking this functionality, it is necessary to check if local and domain users with different rights have the access to disabled devices.
Checking if the access to the device is limited can be performed in two stages:
- Check the device availability in the list of devices with the help of the Device Manager system utility (or with the help of the analog – Driver Install Tool).
- Check the access to device with the help of Explorer and Total Commander (for Disk drive class).
If the application works correctly, the access to devices will be denied. A special message will inform the user. Special attention should be paid to the check of access to Disk drive class devices with the help of Total Commander. While using this application the access to such devices also must be denied.
The disabled device will not be displayed in the Device Manager, but after its allowance it will be surely displayed.
Difficulties and specific to which you should pay attention during the testing will be presented below.
In this article, the list of devices, with which the application should be tested, is proposed. But this list can be supplemented by other devices and ports depending on the project specificity.
The list of devices:
1. Disk drive device class
USB – flash
The USB – flash is a device used in the everyday life. The biggest threat of virus infection for the computer network is usually connected with USB flash drive. It is necessary to check the denying and then to check the allowing of the access to the device.
Do not forget about the check of USB-flash or system behavior if it contains something that is auto run. Also, the special attention should be paid to the situation of USB – flash redirection to another real or virtual computer, especially if the application under testing is installed on both of them.
External hard drive
The External hard drive is the next device to which we want to limit the access. This data storage also can be the mean of data stealing and the source of virus infection of the network. Its redirection to other computers also must be checked.
2. CDROM device class
DVD-ROM
It is better to check its work with the help of the disk with OS or a DVD film on it. Both of them are launched automatically.
Additional attention should be paid to the check of the boot of the disk which is inserted in the disabled device. Nothing must load, open or hang.
3. Image device class
Scanner
Scanner also requires special attention. Its work should be checked together with the applications for scanning launched before and after its disabling. In both cases, the scanner should not scan or get the image.
Also it is not out of place to check the scanner and the system behavior by means of denying during the scanning.
VMware Workstation mounts the scanner and it is important that the system state is stable.
Web-camera
Web-camera also can have the limited accessibility. The disabled web-camera should not reproduce video.
4. USB device class
Printer
Printer is also used frequently. It is not necessary to mention its importance in the office, but it’s worth mentioning that it can print information which could not be copied to the USB-flash. So, the access to it also should be limited. It is possible to limit the access before the opening of the application, with the help of which printing is performed, and after it is already opened. Do not forget about the check of the denying functioning while the document is being printed.
Multifunctional device which combines both a scanner and a printer also should be paid attention to during the check of the application functionality.
USB-hub
The USB-hub has a lot of surprises for you. The device acts more or less stable after the denying of access to it, but if you connect some other devices to it, a problem of their interaction appears. The USB-hub must limit the access to all devices that are connected to it despite the fact that the access to them may be allowed.
5. Mouse device class
USB-mouse
USB-mouse is very useful during the work. It’s very easy to check its disabling – if the cursor is stationary even if it is being moved and the buttons don’t help – it means that the access to the mouse is limited.
6. Keyboard device class
USB-keyboard
The same can be said about the keyboard. The access to it can be considered limited if pressing any key combinations causes no reaction.
Concerning all USB_ devices, it is necessary to mention the importance of stress testing. Unplugging the cable after the use of the limitation rule for the device can be a small stress test. There is a high probability of system failure with the “blue screen”.
7. Bluetooth device class
USB-bluetooth
USB-bluetooth also must have limited access. For example for the purpose of traffic economy by means of limiting the access to your Internet. After limiting the access to this device the user will not be able to connect to the computer.
The list of ports:
COM port
You can check the work of the COM port with the help of modem, which is connected via COM port. Of course, modem connected to the port should not be displayed in the list of computer devices and it should not work too.
LPT port
Old printer models may require LPT port. The printer, which is connected to the port with limited access, must not print at any circumstances.
USB-port
You can check if the access to the USB port is limited by connecting one of the USB devices listed above.
2.3. Specific of application work on different OS
A driver, which is a part of the application limiting access to devices and I/O ports, can behave differently on various OS. Special attention should be paid to its check by the Windows Driver Verifier system utility. It will help to discover the problems in the work of the driver.
The application should be checked on all kinds of OS, beginning from Windows XP with different Service Packs to Windows 7. Do not forget about OS with the User Account Control. Despite the high security level, a driver should handle all denying rules of the access correctly.
Do not also forget about Server OS (Windows Server 2003, 2008) during the testing.
2.4. Compatibility with different applications
Several classes of applications that can cause difficulties during the interaction are described in this part of the article:
- Applications for virtualization ( VMware Workstation, Virtual Box, Virtual PC)
- Applications that redirect devices (for example mstsc – Device Redirection feature of remote session, Сitrix (ICA) )
- Antiviruses
Problems that occur during the interaction with each of the application are examined below.
Applications for virtualization
Applications for virtualization connect devices to the virtual computer and that can particularly cause the system failure with the “blue screen”. How can you check it? It is very easy: install the application for virtualization (for example, VMware Workstation) on the computer with the installed client and the connected disabled USB flash. Start the virtual computer (allow it to mount USB devices beforehand). Unplug and connect the USB flash again. The virtual computer intercepts the USB flash. The system can become unstable . This is not good.
Applications that redirect devices
During the redirection of the device from the computer with the installed client, there can be a system failure with the “blue screen” like it was described above.
Antivirus
Antivirus can interpret the application driver as a virus. That can cause the driver operation failure.
3. The common check-list for test performing
Taking into account the specific of testing of the application, which limits user access to devices and I/O ports, a check-list was compiled. It contains a list of basic tests for checking the user access limitation to the most necessary devices. This check-list can be used for testing of application on all OS.
| System: Device/Port | XP SP3 Application | Allow | Deny |
| USB – flash | |||
| Device Manager Explorer Total Commander | |||
| External Hard Disk | |||
| Device Manager Explorer Total Commander | |||
| DVD-ROM | |||
| Device Manager Explorer Total Commander | |||
| Scanner | |||
| Device Manager Explorer | |||
| Web-camera | |||
| Device Manager Explorer | |||
| Printer | |||
| Device Manager Explorer | |||
| USB-hub | |||
| Device Manager Explorer | |||
| USB-mouse | |||
| Device Manager Explorer | |||
| USB-keyboard | |||
| Device Manager Explorer | |||
| USB-bluetooth |
4. Conclusion
Application controlling user access to devices and I/O ports is a program product that aims at prevention of access to important information, its integrity violation, and also confidential data leak; at protection of computer networks from viruses.
Specific of testing of such application consists in the necessity of examination of the work with different device classes and models, which are in abundance on the world market nowadays.
A driver, which is a part of the application limiting access to devices and I/O ports, behaves differently on various OS. That involves the necessity in the examination of its work on all supported OS.
Problems are inevitable during the interaction with applications for virtualization (VMware Workstation), applications that redirect devices and with antiviruses.
Testing of the application controlling user access is a very laborious and continuous process that requires patience and attention.


