In this article, I will tell you about the process of my research and the results I’ve obtained. I will describe PackageAnalyzer program created as a supplemental tool that displays various data on applications installed in the system. The following is a short summary of its functionality and basic elements implementation.
Contents:
Research Process. Results

First of all we need to obtain the Android OS source code. The official web-site provides the detailed instruction on downloading the source code from the repository. Following this instruction, I set up the program environment and began the download. At that moment 4.1 was the latest version of the source code available for download. That process took a while, as the overall size of the data received was nearly 15Gb.
What should we begin with? How to find a way to analyze such a volume of data under tight schedule…
It is a well known fact that programmers are rather lazy, which prompts them to optimize their work process in various ways, and I wasn’t an exception to the rule. I came up with an idea how to ease this process a little bit by creating a program that would scan all installed packages and display the information I need, namely activities, services, broadcastservices. What’s the point in it? Firstly, it provides arranged information on packages, which allows to outline those that are of a particular interest to me. But you cannot always define the activity purpose by its name. That’s why I modified the program by adding a function that allows you to run a separate activity from the acquired list.
As the result I outlined the list of Android system applications that might be of a special interest:
- com.android.browser
- com.android.contacts
- com.android.development
- com.android.email
- com.android.mms
- com.android.phone
- com.android.settings
- com.android.packageinstaller
The next step was the research itself.
What should I look for and pay special attention to? As we know, activity is launched with the help of Intent. To do this, we need to call the startActivity(Intent) or startActivityForResult(Intent,int) method, if we expect to obtain certain result, and pass to it the Intent we’ve already created. Intent is a kind of a package, which a sender fills with various data and sends to the recipient (activity) for analysis. Therefore I was tasked with identifying the activities capable of executing the instructions set in Intent, which are not described in the Android manual.
Activity life cycle (Pic. 1) begins with onCreate() method. In most cases, exactly this method extracts the data included into Intent. The getIntent() method is used for this purpose. Hence, equipped with Far, I started searching for classes with included getIntent() with further research of what happens inside of each class, what data is extracted from Intent, and for what purpose it is used. Using this algorithm, I went through each system package, which was planned to be researched.
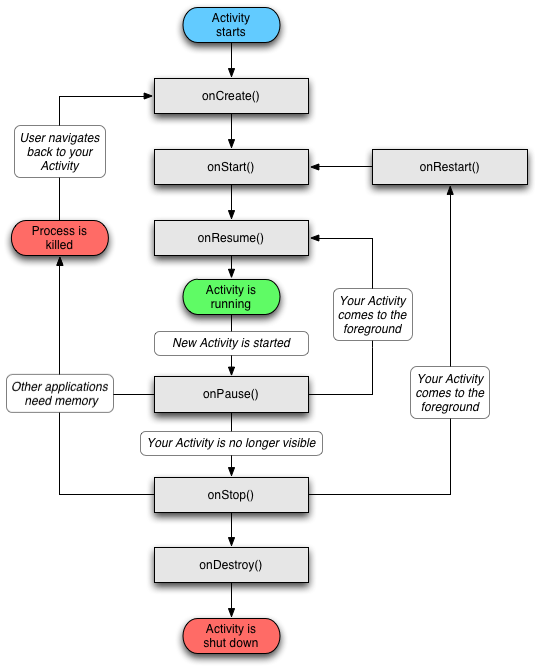
Pic. 1. Activity life cycle
Unfortunately, I couldn’t find any hidden possibilities in the system packages of Android OS. Perhaps, it happened due to shallow application research, for which I didn’t have much time, that didn’t allow me to go deep into the features of each application. But negative result is a result after all. I am sure that Google programmers did a great work to eliminate system vulnerabilities by the release of new Android OS – all loopholes, which I was trying to find, were covered.
Program Part. Package Analyzer

As I mentioned earlier, I created the PackageAnalyzer Android application that was mainly tasked with collecting and displaying various information on installed applications. Besides, additional service that checks the requested permissions in newly installed applications and warns about the potential danger was added to the program functionality.
Functionality
- Acquiring the list of installed applications;
- Acquiring the list of Activities, Services, Broadcast Receivers, Permissions;
- Launching a separate activity from the list;
- Notifying about potentially dangerous permissions used by the application;
- Service. Tracking the applications being installed and checking the permissions they request.
Appearance
The user interface consists of two activities.
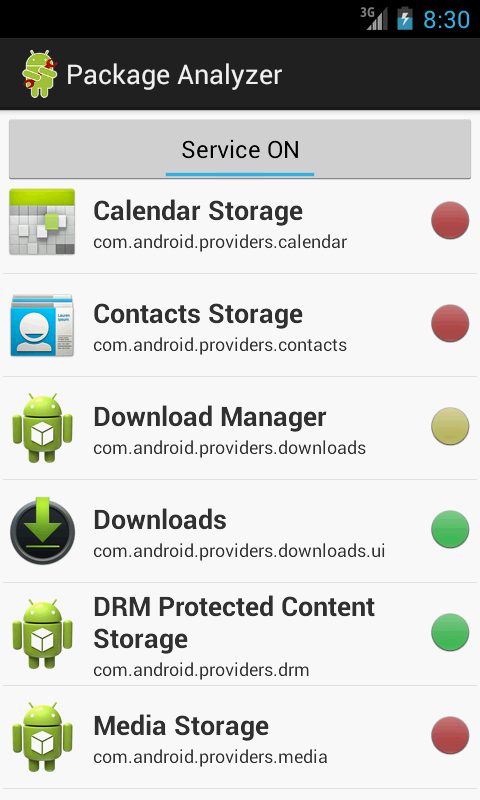
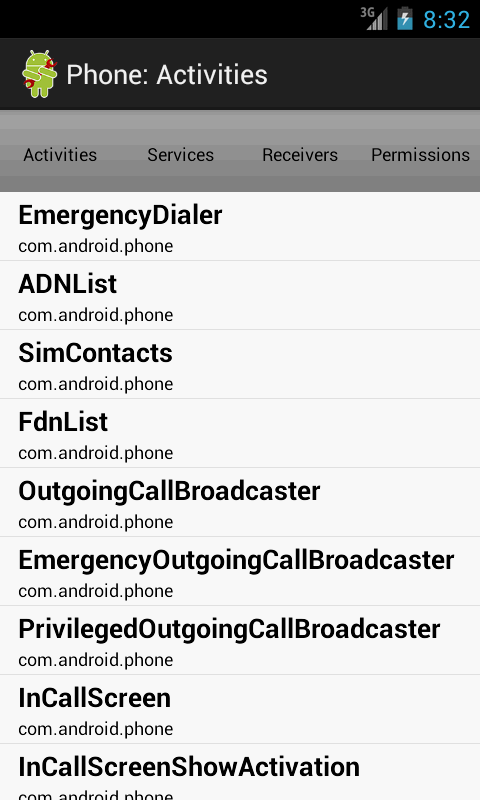
When launched, the program acquires the list of all installed packages and displays it in the main activity. After a package from the list is selected, the second activity is launched. It displays the detailed information on the internal package components (activities, services, receivers, permissions).
In the “Activities” section, you can initiate the launch of any component from the list by clicking it. In this case, an attempt to launch it with the help of Intent will be made. If everything goes smoothly, the selected activity is displayed on the screen. But not all activities can be launched this way, as an attempt to acquire certain data from Intent that initiated the launched is made in many of them, in onCreate() method, and if some data is not actual or wasn’t found, the activity cannot be launched.
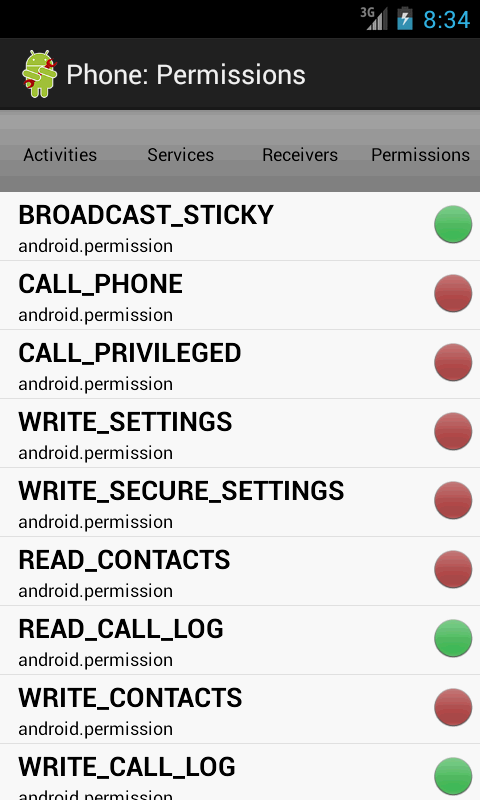
Any Android application requires a permission to perform an action. The list of requested permissions is displayed to a user before each installation. That means that in theory it allows a user to make himself secure against malicious software getting into a phone. But practice shows different results: most users simply do not pay attention to this list. This gives malicious software the opportunity to get into the phone and use the user means as it wants.
That is why the ScannService service was added to PackageAnalyzer program. Its main task is to check the permissions requested by new applications and to inform a user in case any potentially dangerous permissions are detected. Such permissions would include: sending and receiving SMS, making paid phone calls, access to your location, access to personal data (contacts, emails), and so on. To learn more about working with text messages, check out our article on receiving SMS in Android.
The permissions are checked for new applications, as well as for already installed ones. This check is performed at the PackageAnalyzer launch. Depending on the permissions requested, the indicators in are displayed in the main activity and in the Permissions section in one of three states.
Risk level:

– high;

– middle;

– low.
If a user allowed malicious software to be installed, ScannService shows the corresponding notifications and plays a sound signal.
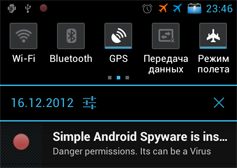
By clicking the notification, you launch the activity with detailed information on the package. You can start/stop this service by clicking the button on the main activity.
The ScannService registers two BroadcastReceivers at launch. The first one gets the notifications on newly installed applications and initiates the check, and the second one starts the service in case of a mobile device restart.
Implementation
Information on installed applications is located in PackageManager, which can be acquired from the context:
PackageManagerpackageManager = context.getPackageManager();
We acquire the list of installed packages:
public List<String> getInstalledPackagesList()
{
List<String> list = new ArrayList<String>();
List<PackageInfo> packageInfoList = packageManager.getInstalledPackages(
PackageManager.GET_ACTIVITIES );
for( PackageInfo packageInfo : packageInfoList )
{
list.add( packageInfo.packageName );
}
return list;
}We acquire the list of activities located in the indicated package:
public List<String> getActivities( String packageName )
{
List<String> list = new ArrayList<String>();
try
{
PackageInfo info = packageManager.getPackageInfo( packageName,
PackageManager.GET_ACTIVITIES );
for( ActivityInfo activityInfo : info.activities )
{
list.add( activityInfo.name );
}
}
catch( Exception ex )
{
ex.printStackTrace();
}
return list;
}We acquire the list of services, receivers, and permissions the same way by passing the corresponding parameter to getPackageInfo(): GET_SERVICES, GET_RECEIVERS, GET_PERMISSIONS.
BroadcastReceivers are declared with android: enabled="false" parameter in AndroidManifest.xml file, as by default the service is stopped. The receivers are inactive until a user launches the service. The components activity state is changed in the following way:
public int onStartCommand( Intentintent, intflags, intstartId )
{
setComponentEnabled(true, PackageInstalledReceiver.class );
setComponentEnabled(true, OnBootDeviceReceiver.class );
...
}
public void onDestroy()
{
setComponentEnabled(false, PackageInstalledReceiver.class );
setComponentEnabled(false, OnBootDeviceReceiver.class );
...
}
private void setComponentEnabled(boolean enabled, Class<?> clazz)
{
int state = enabled ? PackageManager.COMPONENT_ENABLED_STATE_ENABLED
: PackageManager.COMPONENT_ENABLED_STATE_DISABLED;
getApplicationContext().getPackageManager().setComponentEnabledSetting(
new ComponentName( getApplicationContext(), clazz ), state,
PackageManager.DONT_KILL_APP );
}It is necessary to check the activity of the service at program launch. To do this, you need to acquire the list of all started services and perform a search in it:
public static boolean isServiceRunning( Context context, String serviceClassName )
{
ActivityManager activityManager = (ActivityManager) context.getSystemService(
Context.ACTIVITY_SERVICE );
List<RunningServiceInfo> services = activityManager.getRunningServices(
Integer.MAX_VALUE );
for( RunningServiceInfo runningServiceInfo : services )
{
if ( runningServiceInfo.service.getClassName().equals( serviceClassName ) )
{
return true;
}
}
return false;
}Summary
In conclusion, I would like to note that although I didn’t obtain any results after searching for hidden possibilities of Android system applications, I created an application for analysis of programs installed on a mobile device, which can be used in the future. The functionality of the program can be extended to obtain more detailed information on applications, as well as to provide security (detection of malicious software and so on).
References
- http://developer.android.com/guide
- http://developer.android.com/guide/topics/security/permissions.html
- http://developer.android.com/guide/components/services.html
- http://developer.android.com/guide/topics/ui/notifiers/notifications.html
Downloads:
Continue reading with another Android-related artcile: Build Android app from command line.




