With hacking attacks becoming more complex and creative, standard cybersecurity tools might not be enough to mitigate them. That’s why developers of cybersecurity solutions are implementing progressive technologies like artificial intelligence (AI) and machine learning (ML) to enhance their existing cybersecurity products.
Leveraging AI and ML algorithms for cybersecurity purposes is an ongoing trend because it helps to quickly detect attacks, distinguish phishing emails, and predict threats. However, proper adoption of these technologies is still tricky.
In this article, we overview ways in which AI and ML can enhance cybersecurity solutions and explore the key benefits, use cases, and challenges of AI adoption. We also discuss the nuances you should know before developing your own AI-powered cybersecurity product.
Contents:
Why cybersecurity solutions need AI and ML
To detect attacks in real time and reduce the time for remediation, developers continuously augment cybersecurity tools with new technologies. In particular, they often turn to artificial intelligence and machine learning to:
- Automate threat hunting
- Improve the detection of new types of threats
- Handle the ever-growing number of attack vectors
- Find vulnerabilities in code
- Manage a growing digital infrastructure
But before we explore how AI and ML can help overcome those cybersecurity challenges, let’s briefly define these terms to understand the differences between these technologies.
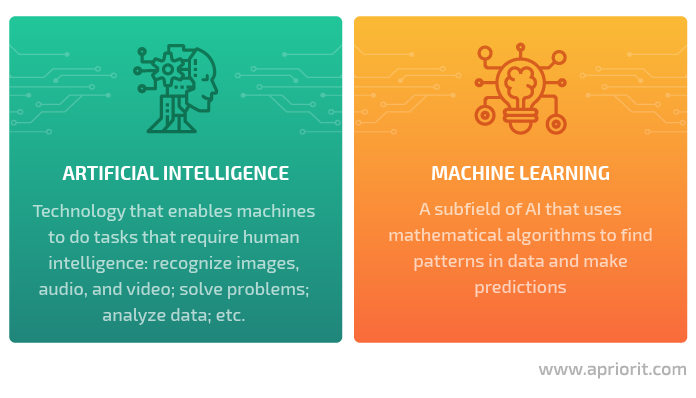
Artificial intelligence (AI) is often defined as the science of making machines replicate human intelligence. This technology enables machines to perform functions like learning, planning, and problem-solving, as well as to recognize images, audio, and video. In cybersecurity, AI is often applied for detecting threats and automating repetitive tasks to save analysts’ time. Examples of products that use AI for cybersecurity purposes are IBM Security QRadar XDR, Vectra, and MicroAI.
Machine learning (ML) is a subfield of AI that uses mathematical algorithms to find patterns in data and learn from those patterns just like people do. Machine learning in cybersecurity is often used to detect anomalous behavior of users and systems as well as to analyze security logs and predict unknown threats. Most ML algorithms used in cybersecurity solutions are based on supervised and unsupervised learning.
What benefits do AI and ML bring to cybersecurity solutions?
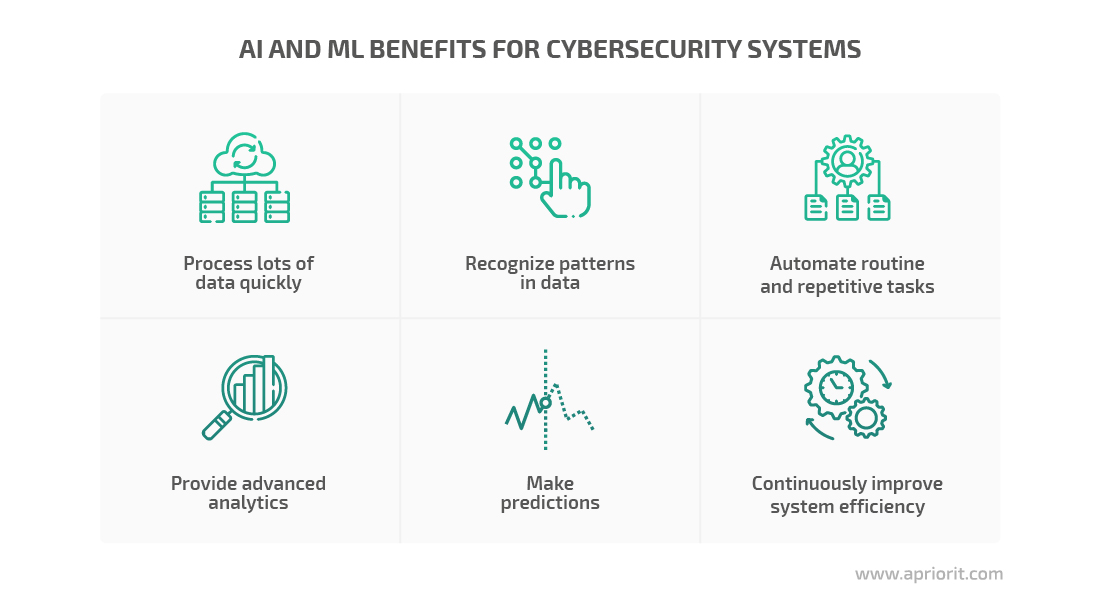
AI-driven security applications can react to suspicious activity in real time and prevent attacks before they happen. Such solutions can quickly process huge unstructured and hybrid datasets, analyze data, find patterns, and even make forecasts.
AI can automate routine and repetitive tasks, reduce the time for investigating attacks, and produce fewer false positives compared to traditional cybersecurity systems. In addition, self-learning ML algorithms are designed to refine their performance with time, improving overall system efficiency.
Implementing AI and ML in cybersecurity solutions can improve their efficiency, enabling such software to better protect companies against existing and unknown threats. Furthermore, these innovative technologies have the potential for enhancing traditional cybersecurity solutions and processes. Let’s explore what cybersecurity challenges you can overcome with AI and ML.
Level up your data protection systems!
Partner up with Apriorit to adopt cutting-edge algorithms and ensure the security of your sensitive data.
When to apply AI and ML in cybersecurity solutions: 6 use cases
Thanks to the ability of AI and ML to process large amounts of both structured and unstructured data, detect patterns, and learn, the application of artificial intelligence and machine learning in cybersecurity tools can crucially enhance them. Here are a few key cybersecurity-related tasks which these technologies can help you accomplish:
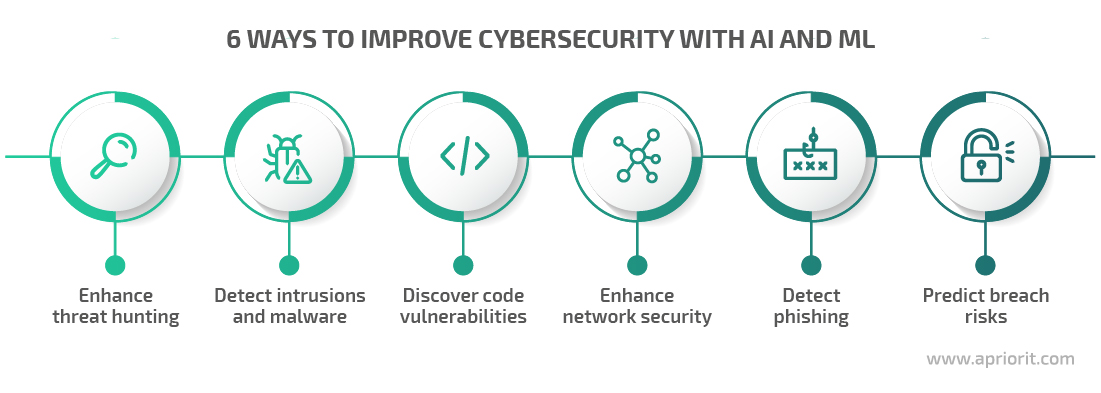
1. Enhance threat hunting. Threat hunting — proactively searching for cyber threats that are lurking undetected in an organization’s network — used to be a manual and time-consuming process. However, with the adoption of machine learning, advanced analytics, and user behavior analytics (UBA), you can partially automate threat hunting, thus increasing its efficiency.
2. Detect intrusions and malware. You can also use ML techniques to enhance signature-based systems of malware detection. For instance, attackers often create variants of malware to evade detection when using the same malware repeatedly. Since traditional signature-based methods fail to detect unknown malware variants, security analysts propose behavior-based detection: a technique that analyzes a file’s characteristics and behavior to determine if it is indeed malware.
However, traditional data scanning and analysis take too much time, making such an approach inefficient. When enhanced with ML capabilities, your cybersecurity tool will be able to process large volumes of data, therefore speeding up analysis and efficiently distinguishing malware.
3. Discover code vulnerabilities. Both attackers and application developers hunt for code vulnerabilities. The first one to detect a vulnerability wins. One of the modern ways to search for dangerous flaws in code is using AI and ML algorithms that can quickly scan vast amounts of code and detect known vulnerabilities before hackers notice and exploit them.
The idea of identifying flaws in code with AI is not new, but it is still the subject of research. Some researchers automate software vulnerability detection using hybrid neural networks. Although this approach has proven to be valid, there are still some limitations related to the language software is written in and the lack of labeled vulnerability datasets.
4. Enhance network security. Outdated software, firmware, and security policies are common security risks that enlarge an attack surface. To overcome these issues, you can leverage AI capabilities to enhance your cybersecurity solution and enable it to:
- Manage all connected devices within the growing environment
- Learn network traffic patterns to spot abnormalities
- Recommend functional groupings of workloads and security policies based on specific needs
5. Detect phishing. ML-powered email analysis solutions tend to work faster and more efficiently than traditional ones. You can train ML algorithms using a vast collection of both phishing emails and safe emails so the algorithms can learn to analyze the message context, understand how users communicate, and find deviations and specific patterns.
For example, you can use this approach to build a system that can notice forged senders by identifying email addresses that are similar to those a person has already received emails from (such as the address of a CEO or chief accountant). Or you can train ML algorithms to react to words that show urgency, which is a common sign of phishing emails.
6. Predict data breach risks. You can enhance your cybersecurity solution with advanced analytics (AA). AA is the autonomous processing of data that uses AI techniques and ML algorithms to find deep correlations, make predictions, and provide recommendations.
There are two categories of advanced analytics — predictive and prescriptive — each providing different outputs after processing big data and requiring different levels of human involvement.
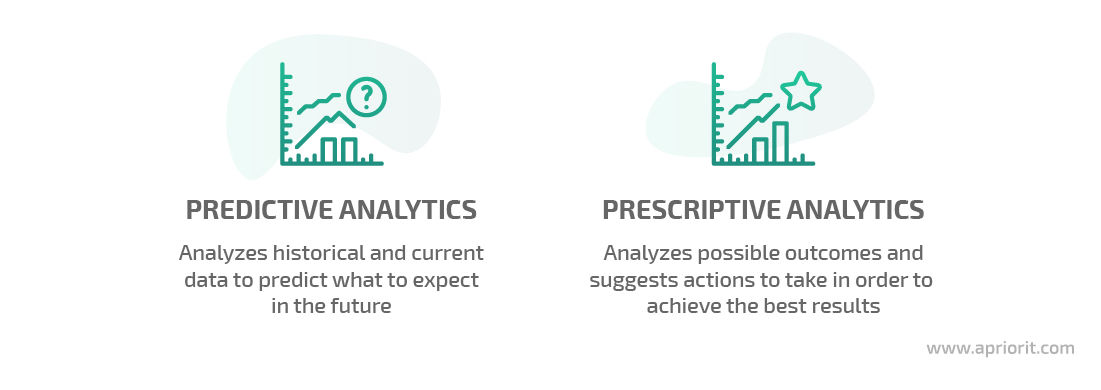
Predictive analytics analyzes historical and current data to predict what events to expect. However, the choice of responsive actions to possible threats is up to an organization. You can apply predictive analytics to make your security solution more effective at detecting security risks and preventing attacks.
Prescriptive analytics answers what to do given particular expected outcomes. When implemented in a cybersecurity solution, prescriptive analytics not only predicts future events but also analyzes possible outcomes and suggests what actions an organization should take in order to achieve the best results. For instance, if a user tries to send sensitive data to an external server, the system could advise executing a firewall rule in order to break the connection.
Now that you know what tasks you can solve with the help of AI and ML while working on your cybersecurity project, let’s look closer at some of the key challenges you might face along the way.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Examine how Apriorit’s experts helped the client enrich stability and competitiveness of their SaaS cybersecurity platform. Unveil the details of how our development efforts helped the client enhance the software and improve user experience.

Challenges of implementing AI in cybersecurity projects
Despite all the benefits AI and ML can bring to cybersecurity solutions, applying these technologies isn’t straightforward. Let’s explore the key challenges that may arise when enhancing cybersecurity solutions with AI and ML:
1. Cost. Being a complex technology, AI has high adoption barriers. To build and maintain an efficient AI-powered solution, you need to invest time and money in researching the technology, finding experienced team members, allocating enough computing power and data centers, etc. So before rushing to develop an AI-driven cybersecurity solution, make sure to assess all possible risks and study the market to evaluate product demand.
2. Lack of datasets. Accurate and extensive datasets are a must for developing any AI-based solution. Developers need them not only to help algorithms learn but also to test them. To create the datasets for a cybersecurity solution, your team may need to find examples of malicious code, malware, and anomalies, depending on what your solution is supposed to do.
Gathering and labeling data manually is an extremely time-consuming process. To save time, consider purchasing ready datasets or try looking for free datasets. But make sure that the datasets you collect:
- Fit your project’s purposes
- Contain complete and undamaged data
- Contain data with accurate and correct labeling
4. AI-driven attacks. Considering various types of hacking activities is essential when building a cybersecurity product. Make sure to pay attention to the fact that hackers also use AI to make their attacks smarter, and think of ways to address these threats.
For instance, in April 2020, researchers discovered that phishing attacks can be performed by employing a deep neural network-based phishing URL generation system called DeepPhish. Curiously, to prevent such attacks, they designed an ML-based detection system called PhishHaven. Researchers claim PhishHaven can identify both AI-generated and human-crafted phishing URLs.
5. Vulnerabilities in AI systems. Just like any other solution, AI-powered software itself can be vulnerable to attacks. Common attacks on AI solutions include attempts to confuse the underlying ML model and bypass what the AI system is supposed to do.
To build complex and efficient products, developers use ready-to-go ML algorithms, various libraries, and other third-party components that also may be vulnerable. If malicious actors manage to find vulnerabilities in at least one of these components, they might use their knowledge to exploit them and attack your solution.
For instance, when studying the impact of platform vulnerabilities in AI systems, MIT researchers decided to test the Cognitive Toolkit (CNTK) — an open-source deep learning toolkit developed by Microsoft — against an attack. Their goal was to use a malicious input image for CNTK and cause the engine to misclassify other images. Thanks to the vulnerability researchers found, the attack was successful.
To overcome such challenges, carefully research third-party components you’re going to use in your cybersecurity solution and test your product against a vast number of possible attacks. Ensure security not only within the trained model but within the trained data and algorithms.
With all the benefits and challenges in mind, let’s explore nuances you should keep in mind when building an AI-powered cybersecurity solution.
Read also
AI and ML for Fraud Detection: Top Use Cases, Approaches, and Technologies
Protect your data with AI-powered fraud detection. Discover industry benefits and essential technologies for effective implementation of AI and ML in real-world examples.

5 things to consider when developing an AI-based security solution
If you want to integrate AI and ML in your existing cybersecurity solution or create an AI-powered security product from scratch, you should be aware of several key aspects of this process:
1. Define which product functionalities need AI. Make sure you apply AI and ML technologies only where other approaches prove inefficient or overly expensive. The most common types of tasks to solve with AI and ML are visual identity verification, big data analysis, and vulnerability detection.
2. Search for qualified team members. Apart from developers with experience in both cybersecurity and AI, you’ll also need data scientists familiar with data analysis, computer science, and statistical modeling, as well as data analysts who have deep knowledge of mathematics and experience using analytical tools to extract insights from big data. If you’re looking for an outside vendor, find out whether the development team has previously deployed advanced analytics for cybersecurity.
3. Research existing algorithms. During the research phase, it’s vital to examine existing algorithms and models, evaluate which can be used for your purposes, and choose the most suitable ones for development. Building your machine learning algorithms for cybersecurity purposes from scratch can be unaffordably time-consuming and expensive, especially for small projects.
4. Acquire a comprehensive dataset for model training. AI developers use big data about malicious activities to train their algorithms. Determine how and from where you will acquire the necessary data for your solution.
5. Keep testing nuances in mind. Testing AI systems has its own specifics, so your QA and testing teams have to be aware of them. For instance, it’s important to know whether the ML model used is underfitting or overfitting, whether the system is supervised, what types of data were used for model training and how old the data is, etc.
The aspects mentioned above are the most common for all types of AI-powered cybersecurity solutions. However, every product is likely to have its own development nuances. So make sure to conduct thorough research and consult experienced developers before starting AI and ML implementation.
Conclusion
The use of artificial intelligence is an ongoing trend in the cybersecurity market. The reason is that AI and ML offer an exciting potential to help businesses build efficient cybersecurity solutions enhanced with advanced analytics, self-learning algorithms, and task automation.
But despite a wide number of benefits and possible use cases, applying artificial intelligence in cybersecurity tools also has some pitfalls. Creating AI-powered solutions is a complex process that requires extensive resources, thorough planning and research, as well as strong development and testing skills.
At Apriorit, we’ve gathered dedicated teams of specialists with expertise developing cybersecurity systems and AI-based solutions for different industries. We are ready to help you successfully overcome all the complexities of embedding artificial intelligence in your cybersecurity products.
Enhance your next application with AI!
Let’s cooperate on building a truly smart solution that will help you bring your services to a new level.


