Сloud computing brings organizations lots of advantages compared to on-site resources, and that’s why it’s a popular target for inside and outside attacks. To ensure the security of an application in the cloud, take into account known cloud vulnerabilities and data protection best practices.
As a company with more than 20 years of experience in the cybersecurity industry, Apriorit has a lot of hands-on experience preventing different types of attacks in cloud computing. In this article, we overview key vulnerabilities of cloud computing technology, then take a look at the most common types of attacks on cloud computing. Finally, we offer practical advice on how to ensure the security of your cloud-based solution considering industry best practices and our own experience.
This article will be useful for development and product leaders who want to use cloud computing in their solutions and make sure they are protected.
What are cloud attacks?
Cloud computing provides organizations with a plethora of business-oriented benefits: reduced infrastructure cost, zero expenses for on-premises hardware, on-the-fly scalability to accommodate any number of users, etc. It also helps companies to quickly adopt trending technologies like generative AI, big data, and infrastructure as a service. That’s why the market for cloud software and corporate cloud budgets grow constantly. Gartner predicts that spending on public cloud will reach $678.8 billion in 2024.
From a cybersecurity perspective, cloud computing can make an application more vulnerable to threats and attacks compared to on-premises deployment. Also, while cloud computing market grows rapidly and offers more and more cloud applications, a lot of them can’t guarantee reliable security for sensitive data. That’s why cloud applications and storage attract a lot of attention from malicious actors.
A cloud attack is a harmful action towards any cloud-based system or service, including cloud computing, Software-as-a-Service, cloud storage, etc. It can come from outside and inside of an organization and have malicious or negligent intent. Cloud attacks can lead to a variety of negative consequences such as data leak or theft, disruption of services, and financial and reputational losses.

3 real-world examples of cloud attacks
Vulnerabilities in cloud computing technology have caused some of the biggest data breaches that get extensive media coverage. Here are several examples of cloud cyber attacks that led to significant damage for companies:
- Massive MOVEit hack. MOVEit, a tool that uses FTP and cloud infrastructure to transfer files, suffered a ransomware attack in June 2023. The Clop hacking group abused a security vulnerability to steal sensitive data transferred with MOVEit. This included data from US universities, public sector organizations, banks, energy and manufacturing companies, and legal services providers. At least 15 million people were affected. The US State Department is offering a $10 million bounty for information about the Clop group.
- Two T-Mobile breaches. T-Mobile disclosed that they experienced two massive data breaches in February and March 2023 that exposed the data of over 37 million customers. The company claims that a hacker accessed this information via an API that wasn’t protected with authorization.
- Leakage of US military emails. In February 2023, Anurag Sen, a security researcher, discovered an unsecured US Department of Defense email server hosted in Microsoft Azure. The server, which stored about 3 TB of sensitive military and personal information, wasn’t protected with a password.
Breaches of cloud infrastructure and applications can be caused by various factors, from targeted hacking activity to reckless employee actions and cloud misconfigurations. Let’s examine the key cloud computing vulnerabilities that make such breaches possible.
Want to secure your cloud app?
Leverage our 20+ years of experience to deliver a protected and robust cloud solution for your business.
7 vectors of cloud computing attacks
In a cloud environment, cybersecurity responsibilities are divided between a cloud service provider (CSP) and clients. This division complicates data protection because it creates more entry points for malicious actors and room for human error. The responsibilities of both sides also differ depending on the chosen cloud computing model.
Let’s take a look at some common vulnerabilities that can become cloud attack vectors:
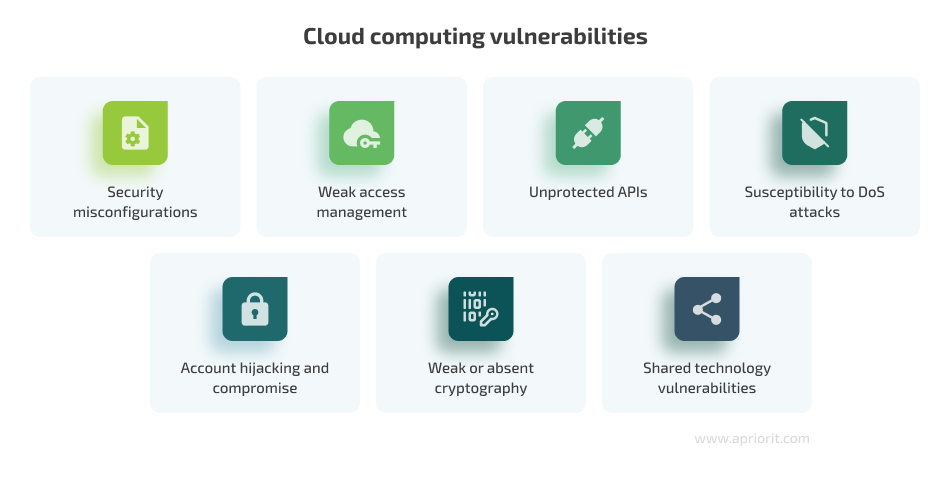
Security misconfigurations. Major CSPs like AWS, Google Cloud, and Azure provide their clients with numerous ways to configure the security of their environments. Developers can set additional protection measures for storage, infrastructure elements, virtual machines, etc. But developers can also misconfigure an environment due to:
- Human error
- Incomplete documentation from the CSP
- Hidden or unobvious settings
Malicious actors can abuse a misconfigured cloud environment to gain unauthorized access, compromise accounts, and malware injection attacks. Weak security configurations can also increase the risk of insider threats.
Weak access management. Access to cloud resources should be protected with multi-factor authentication (MFA), password management, configurable access rights, etc. Ideally, users should be able to access only the resources they need after the system verifies their identity, credentials, and access rights.
When a CSP doesn’t provide enough access protection capabilities or cloud administrators neglect to use them, hackers can hijack and compromise user accounts and use their access credentials for data theft and leaks.
Unprotected APIs. APIs allow users to interact with cloud-based services. Vulnerabilities in APIs may significantly impact the security of a cloud-based application. For example, an API can overshare access information, grant unwanted visibility into the internals of an application, or ignore a service’s traffic limitations.
That’s why hackers often use cloud APIs to gain unauthorized access to data or perform a denial-of-service (DoS) attack.
Susceptibility to DoS attacks. One of the key benefits of cloud computing is 24/7 availability of a cloud application. If an organization and CSP fail to implement DoS protection mechanisms, malicious actors can spam their instances with requests and make them unavailable to legitimate users.
In this way, an organization can lose access to its sensitive data and internal cloud-hosted applications, or fail to provide services to its users. In some instances, hackers also demand a ransom from organizations to stop DoS attacks.
Account hijacking and compromise. Privileged access to cloud infrastructure and applications is often the target of hacking attacks. Using an admin’s credentials, hackers can infiltrate an organization without anyone noticing. Compromised account activity can also be masked as insider attacks.
Account compromise can happen because of social engineering, failing to secure admin credentials, failing to detect keyloggers and similar malware, and cross-site scripting and buffer overflow attacks.
Weak or absent cryptography. Though cloud providers use cryptography to prevent insider and other attacks in cloud, they usually rely on limited sources of entropy to automatically generate random numbers for data encryption. For instance, Linux-based virtual machines generate random keys from the exact millisecond. There may need to be more flexible to ensure for strong data encryption, as attackers also use sophisticated decoding mechanisms to hack information.
Thus, your team should think about how to secure data before moving it to the cloud.
Shared technology vulnerabilities. Cloud computing involves the use of shared technologies such as virtualization and cloud orchestration. By exploiting vulnerabilities in any part of these technologies, attackers can cause significant damage to many cloud users.
Weaknesses in a hypervisor can allow hackers to conduct side-channel attacks or gain control over virtual machines or even the host itself. In case a hacker escapes a virtual machine, they can gain unrestricted access to the host through shared resources. It’s necessary to pay attention to the security of the cloud provider that you entrust with your cloud solution.
Read also
Multi-Cloud Computing: Use Cases, Pros, and Cons for Enterprises
Expand your possibilities with multi-cloud. Learn when it’s worth investing in multi-cloud, how to build an efficient architecture, and avoid common implementation pitfalls with our comprehensive guide.

How to prevent cloud computing attacks
The dynamic nature of cloud services breaks the traditional security model for on-site software. It’s obvious that an organization can’t fully rely on its CSP to secure the cloud computing environment and needs to put in additional effort to ensure data protection.
At Apriorit, we strive to secure cloud applications during development, cloud infrastructure configuration, and maintenance. Here’s how to prevent cloud computing attacks and improve your state of security:
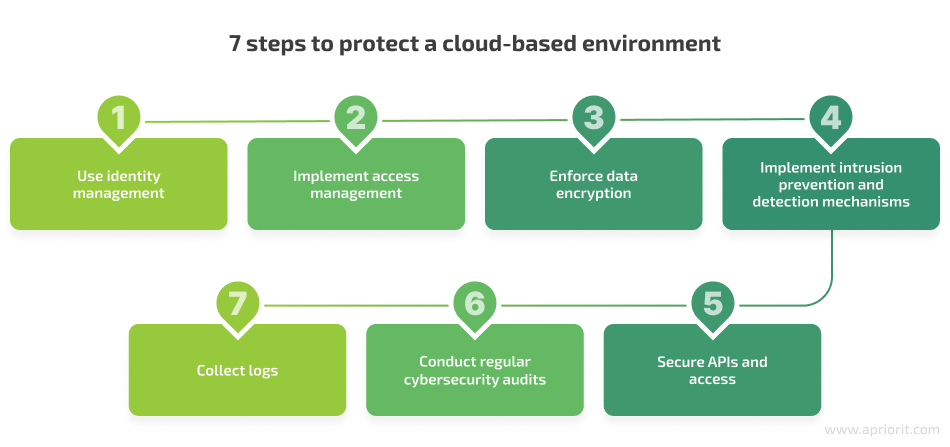
1. Use identity management
Identity management allows a cloud environment to verify a user’s identity before granting the user access to protected resources. This simple but effective measure makes it harder for malicious actors to use stolen credentials to access sensitive information.
All major CPSs provide some set of identity management features. When choosing a reliable CSP for a new project, we always evaluate its capabilities for:
- Multi-factor authentication
- Use and management of static and dynamic passwords
- Use of hardware tokens or biometrics if needed
- Integration with identity services
Keep in mind that during application maintenance, your team has to periodically review identity management configurations, conduct an audit, and secure or delete any suspicious identities and tokens.
2. Implement access management
Once granted access to a cloud environment, users should be able to interact only with the resources they need. Providing users with unrestricted access to any resource creates the risk of experiencing an insider attack and increases possible damage from credential theft.
To ensure the security of services, cloud app developers should implement role-based permissions to different administrators, privileged users, third parties, and regular users. This way, an application owner can configure access rights, establish access policies, and limit the possible impact on their cloud infrastructure.
Moreover, cloud orchestration should enable privileged users to establish the scope of other users’ permissions according to duties within the company.
3. Enforce data encryption
Data in the cloud environment needs to be encrypted at all stages of transfer and storage:
- At the source (on the user’s side)
- In transit (during transfer from the user to the cloud server)
- At rest (when stored in the cloud database)
Modern data encryption and tokenization technologies are effective defenses against account hijacking. Moreover, it’s important to prove end-to-end encryption for protecting data in transit against man-in-the-middle attacks. Using strong encryption algorithms that contain salt and hashes can effectively deflect cyber attacks on cloud computing.
Even if end-to-end encrypted data gets leaked, it’s unusable to hackers as they will not be able to decrypt, read, and use it.
Related project
Supporting and Improving Legacy Data Management Software
Discover how Apriorit specialists improved user satisfaction with our client’s legacy system by improving its supportability and preparing it for a migration to a new platform.
4. Implement intrusion prevention and detection mechanisms
Many CSPs provide their clients with built-in intrusion detection and prevention systems that monitor either network traffic or machines in the client’s infrastructure to detect malicious activity and suspicious user behavior.
When developing a cloud-based application, the team should enable an intrusion detection system and make sure it works as intended to ensure cloud attack prevention. They can also implement custom intrusion detection or ensure their clients can integrate their solution into a third-party system.
5. Secure APIs and access
Cloud developers should be sure that clients can access the application only through secure APIs. If left unprotected, APIs can leak sensitive data, provide hackers with access to cloud infrastructure, and lead to DoS attacks.
Common API protection measures include:
- Using web application firewalls
- Limiting the number of allowed requests
- Reviewing and limiting API access rights
- Implementing OAuth 2.0 for authentication
- Encrypting API responses
6. Conduct regular cybersecurity audits
Security audits help cloud app developers detect cloud misconfigurations, vulnerabilities, and outdated data protection mechanisms they have overlooked, as well as to improve the overall cybersecurity posture of their solutions.
As a cybersecurity-oriented development company, we conduct independent audits of cloud-based solutions for our clients. During an audit, we pay special attention to:
- Authentication and access control
- Configuration of cloud storage, computing endpoints, network, and other elements
- The state of databases, applied encryption mechanisms, and backup procedures
- Compliance with requirements and regulations applicable to a client’s solution
To conduct an audit, we use checklists based on best practices recommended by the CSP as well as our experience with a given cloud platform. You can examine our checklists for auditing AWS and Azure environments.
After an audit, we provide the client with a detailed report on detected vulnerabilities and possibilities for improvement. We also offer advice on how to improve the security of their cloud application or service.
Read also
The 6 Most Common Security Issues in API Development and How to Fix Them
Protect the sensitive data flowing through your APIs. Learn the common API threats and discover how to make your APIs immune to hacker attacks in our expert guide.
7. Collect logs
Detailed logs of all activities inside a cloud environment are essential for conducting security audits, investigating incidents, researching vulnerabilities, and more. That’s why any cloud-based solution should be able to log as much information as possible about its work.
It’s considered a good practice to log user and network activity, changes in the state and configuration of infrastructure elements, and data flows inside the cloud. These logs should be encrypted at any state. Many developers also add an option to integrate their solution with popular SIEMs and allow it to share logs securely.
Conclusion
Cloud computing technology is extremely popular among users due to its many advantages. However, cloud technology also introduces vulnerabilities that can lead to devastating and costly cyber attacks. By understanding and securing vulnerable elements of cloud computing technology, developers can better protect their products from different types of attacks on cloud.
At Apriorit, we often develop cloud-based products from scratch, manage cloud infrastructure, and audit the security of existing products. When working on any cloud-related task, our specialists in virtualization and cloud infrastructure management take into account the characteristics of the chosen CSP, security best practices, and requirements applicable to the product, using this information to deliver highly functional and well-protected solutions.
Looking for experienced cloud developers?
Reach out to our team of developers and build a secure and efficient cloud infrastructure for your product!


