Companies developing cybersecurity solutions as well as those using them commonly look for reliable methods to validate the effectiveness of the prevention and detection mechanisms that those solutions provide. This can be effectively done with the help of the ATT&CK matrix, which was developed by MITRE, a company known for its other projects (CVE, CWE, etc.). The ATT&CK matrix is a huge collection of effective cyber attack mechanisms, tactics, techniques, and procedures. It’s also a model that can help a user understand in detail how these elements are put together to penetrate the target’s defense.
Our development team implements the best tactics to prevent any malicious influence on our operating system. In this article, we help you understand the actions of hackers and find the best-case scenario to detect and stop them.
Cyber Kill Chain
The MITRE ATT&CK™ matrix is closely related to the well-known Cyber Kill Chain® framework developed by Lockheed Martin.
The Cyber Kill Chain framework was developed as an advanced method to detect and prevent any cyber intrusion. The MITRE ATT&CK matrix uses this model to understand an attacker’s logic.
For a better understanding of the principles of the MITRE’s ATT&CK matrix, let’s consider the Cyber Kill Chain framework in detail.
The framework contains the following seven steps that adversaries have to take to achieve their malicious intents:
- Reconnaissance — Choose a target and get as much information about it as possible.
- Weaponization — Based on the information acquired during reconnaissance, choose the best tools for carrying out the attack.
- Delivery — Deliver the weaponized bundle to the target’s environment.
- Exploitation — Exploit the vulnerability to execute code in the target’s system.
- Installation — Install a persistent backdoor to maintain remote access to the target’s environment.
- Command and Control (C&C) — Establish a command channel to enable the adversary to remotely manipulate the victim.
- Actions on Objective — Take the planned illegal action, such as data destruction, exfiltration, or encryption.
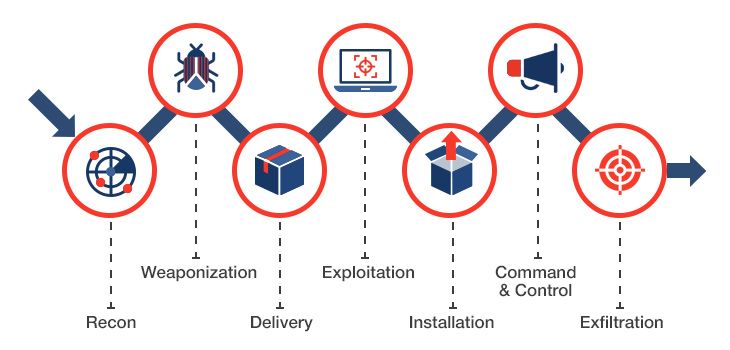
Image 1. Cyber Kill Chain
The main feature of the Cyber Kill Chain is that it’s circular, not linear. As soon as the hacker has penetrated the network, they again begin carrying out additional reconnaissance and performing horizontal promotion within the system.
To break the chain of attack, the attacker must be stopped at any stage. For a successful attack, an intruder must go through all stages. This puts the odds in favor of the security specialists, as they only need to block the adversary at any given stage to prevent an attack.
The Cyber Kill Chain is a systematic process for an attacker to achieve the desired effect. Using the ATT&CK matrix and keeping in mind the attack stages the adversary has to undertake, cybersecurity developers, testers, and officers get a powerful method to create and emulate various attack scenarios to verify the reliability of an enterprise platform or company’s defensive systems.
Indicators of compromise
The Cyber Kill Chain concept is interesting not only by itself; there’s also the possibility of combining it with other information, including linking each stage of the Kill Chain to relevant indicators of compromise.
Although fileless malware has become increasingly common, the most attacks are still impossible to carry out without leaving traces, otherwise known as indicators of compromise. Adversaries have their preferred tools, web services, techniques, and so on. Their preferences could help you to collect information about attackers to identify them in future. Because attacker tools are still technologically limited we have the ability to record, track, and group information about adversaries, develop profiles, and improve our defensive mechanisms.
The main thing when detecting indicators of compromise is being able to immediately respond to them so adversaries won’t be able to use the same method to perform an attack again. Of course, not all indicators are equal, and some are much more valuable than others. We’ll consider one classification of indicators of compromise as an example.
Read also:
Fileless Malware Protection Tips
Pyramid of Pain
There are many ways to classify indicators of compromise. One classification that we find interesting is David Bianco’s Pyramid of Pain. This is one of the best representations of the relationship between indicators of compromise (which are used to detect an adversary’s activities) and the stages of the Kill Chain.
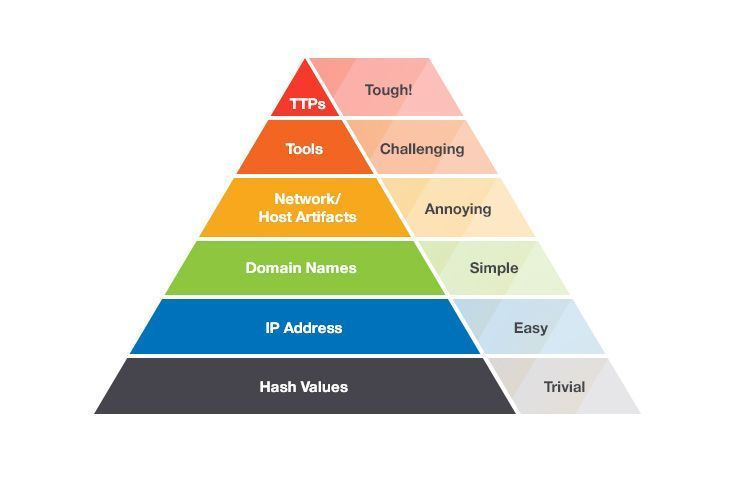
Image 2. Pyramid of Pain
- Hash values — These are probably the most accurate indicators, as the chance of two different files having the same hash value are slim to none. Any insignificant change to a file, like adding a null to the end or flipping a bit in an unused resource, will produce a radically different and unrelated hash value. Therefore, there are so many hashes around that sometimes it isn’t worth the effort to track them.
- IP addresses — Malicious domains and IP addresses are the most fundamental indicators because adversaries have to use a network connection, which implies IP addresses, to carry out the vast majority of attacks. Together with hashes, IP addresses are placed in the widest part of the pyramid because there are so many of them. As with hashes, adversaries can easily change IP addresses whenever necessary. Even if the use of one malicious IP is denied, adversaries can quickly recover with no consequences to their initial plan. If you limit yourself to checking only proxy logs, you can miss out on malware that’s trying to contact the network directly or that’s requesting a non-existent domain name generated via DGAs (Domain Generating Algorithms), or DNS (Domain Name System) tunnels.
- Domain names — It’s rather difficult to change domain names due to the obligatory procedure of domain registration, payment, and hosting. Nevertheless, today there are a great number of free DNS providers, which simplifies the process of changing a domain name. It may take about two days to make a new domain visible throughout the internet, however, and they’re still harder to change than IP addresses.
- Network and host artifacts — When you block adversaries at this level, you start affecting their plans quite tangibly, as they have to go back to the lab and modify their tools.
- Tools — Detecting artifacts of hackers’ tools will help you make those tools useless. This will give you some time, as your adversaries will have to create or find a new tools for their malicious purposes. Of course, this may require investment from hackers to do so, especially if you block several of their tools.
- TTP (tactics, techniques, and procedures of intruders) — If you’re able to detect and prevent an attack at this level, you’re directly responding to your adversary’s behaviors, not against their tools. This forces them to do the most time-consuming thing possible: altogether redesign their behaviors.
11 tactics of the MITRE ATT&CK matrix
The ATT&CK matrix developed by the American corporation MITRE is another interesting classification that has more practical application and can be used in threat modeling.
MITRE ATT&CK is an acronym for adversarial tactics, techniques, and common knowledge definition. It includes about 200 different kinds of adversarial behavior types and continues evolving as more data is added regularly.
The matrix implementation allows red team members to design an integrated campaign to test various aspects of an organization’s defenses. Blue team members can, in turn, analyze malicious behavior as well as use ATT&CK Matrix for Enterprise and ATT&CK Mobile Profile techniques, and tools (for example, rkhunter, chkrootkit, etc.) for precise awareness — at what stage they can help within a global attack campaign.
This matrix doesn’t replace the Cyber Kill Chain but merely clarifies what lies behind the last three stages of it. Let’s review the eleven tactics in the current version of the ATT&CK matrix.
1) Getting initial access
The attacker’s goal at this stage of the attack is to deliver some malicious code to the system under attack and ensure that it can be executed. Techniques belonging to this tactic are used during the delivery stage of the Kill Chain.
The best-case scenario for your security solution is to recognize and properly respond to attacks at this stage. In this case, the rest of the matrix content becomes no more than interesting and educational reading.
Obtaining initial access can take many forms, starting from a spear-phishing link and ending with a trusted user who either unintentionally or intentionally leaks sensitive information to the attackers. This stage is all about penetrating the target’s environment. This drives us to the conclusion that analyzing the environment’s entry points and employing penetration testing to check how easy it is to penetrate them is a must.
2) Execution
This stage corresponds to the exploitation step of the Kill Chain.
If the beginning of the attack has not been detected in time, execution begins via such technologies as scripts, APIs, or services. Certain attacks begin directly at the execution stage — for example, attacks that are launched through third-party software, Windows Management Instrumentation, DLLs, PowerShell, and other lower-level mechanisms, as most of time their initial access stage occurs during legitimate, authorized activity.
Considering the layered security infrastructure, this step in the matrix shows us that monitoring the execution of events is a critical activity.
3) Persistence
This tactic relates to the installation stage of the Kill Chain. Once attackers have penetrated the target system and executed their payload, they have to remain there. Their presence in the attacked system may be lost after the attacked system is restarted, if the attacker loses credentials, or after remote access tools are blocked when the attack is detected. Here, adversaries will try to modify boot sectors, create accounts or hidden files and directories, shim applications, and so on. Defending against a persistent attack requires non-stop monitoring of the various classes of system events and noting atypical ones.
4) Privilege escalation
Performing certain attacks requires a high level of privilege, so this is when privilege escalation comes in. Privilege escalation can take many forms, from manipulating access tokens to bypassing user account controls with DLLs and shimming applications. However, for each of these methods, a malicious insider should avoid generating notifications to system administrators. The defensive tactic here is to track and notify each time a new account is created or an account’s privileges are changed. This tactic can greatly help in avoiding the risk of unauthorized privilege escalation.
5) Defense evasion techniques
Attackers have to bypass existing defensive mechanisms in the process of compromising a target system. Strategies can vary from relatively simple deletion of log changes to complex code obfuscation and encryption. Attackers have to choose particular techniques depending on which types of security mechanisms have to be evaded.
Deleting various log files that contain an attacker’s activity traces as well as creating hidden files and hidden directories can be effective tools when it’s necessary to deceive system administrators. In addition, indirect file execution, port knocking, and side-loaded files can prove indispensable for bypassing security tools and systems. Although security tools are becoming more complex against this stage of attack, we see multi-level approaches to evasion.
There’s currently no single security tool that can defeat every evasion technique that exists. Therefore, the development of advanced security technologies, machine learning, and human behavior analysis should be continued to avoid a potential bottleneck at this level of the campaign.
6) Access to credentials
To freely move within the system under attack, adversaries need to lay their hands on legitimate credentials — and this is the next step in their campaign. The fact that credentials can be found in various places and in many different ways (surprisingly, some applications even today hold user credentials in an unencrypted form in their logs) is a huge advantage for attackers. At the same time, this is extremely bad news for the security guys.
Credentials can easily be stolen through social engineering, for example through spear-phishing, whishing (WhatsApp phishing), and social network phishing, when people are tricked into giving sensitive information to the attackers themselves. So protection against unauthorized credential access should begin with educating employees about phishing. In addition, encrypting all credentials, using multi-factor authentication, and actively monitoring all logins for time and location are vital defensive steps.
7) Discovery
After gaining access to the target system, attackers search for confidential information. Usually, this starts with scanning the file system, services, open ports, and other system components and continues with reading configuration and log files, querying the registry and local databases, and so on. Attackers do everything they can to find any information that might provide a more precise definition of the current state of the environment and, of course, its users.
It’s important to monitor and understand why and by whom certain information is accessed to detect the attacker’s discovery activities in the system. That’s why credential access and privilege escalation are used by attackers before they enter the discovery stage. If they acquire system admin privileges, looking at any piece of information won’t look suspicious and won’t raise any questions regarding its legitimacy.
8) Lateral movement
Typically, an attacker’s goals aren’t limited to only one machine. Often they use such machine as a starting point for distributing the attack in the network. Therefore, it doesn’t matter whether a campaign is aimed at launching a distributed denial of service (DDoS) attack, crypto mining, or stealing sensitive data. The wider the attack surface, the better.
Lateral movement is usually set up using different types of remote services, though there are many other techniques at an attacker’s disposal. For example, scripts, hash passing, and ticket passing are can help an adversary fully take control of a system. Network traffic between endpoints is common to all of these methods. To detect atypical or unauthorized traffic, intrusion detection and prevention systems can be used. Unusual traffic can be the first sign that something is wrong within your organization’s environment.
Read also:
DDoS Mitigation Techniques
9) Data collection
This is the stage when attackers gather all kinds of information to use for their malicious purposes. Data collection techniques range from database parsing to using keyboard loggers that capture sensitive data such as credentials and payment information. This stage can also be one of the most difficult to detect as it’s taking place on a single machine. Moreover, if all previous steps are completed successfully, the evidence of collection activity can be obfuscated or just deleted.
10) Exfiltration
Once the required information is gathered, it’s vital to get it safely out of the system under attack. So here exfiltration techniques come in handy. The exfiltration process involves getting data from where it is to the hands of the criminals who have worked very hard to steal it. Exfiltration takes many forms, from putting data on a USB drive and walking it out to establishing a VPN tunnel and sending it out in portions. However, there are techniques that allow data exfiltration to go almost unnoticed. For example, control channels and out-of-band communication channels allow sending information in such a way that firewalls, intrusion prevention systems, and network monitoring services won’t be triggered. So it’s vital to monitor all communications happening in your network to notice any unusual senders and destinations, ports, channels, or communication types. This allows a greater chance of detecting and stopping exfiltration.
11) Сommand and control (C&C)
If attackers have passed all the previous stages uninterrupted, the command and control (C&C) tactic can freely take over. During this stage, the infected machines communicate with the master C&C servers to execute any kinds of actions, for instance downloading and installing new applications, employing different obfuscation techniques, attacking other systems, and so on and so forth. C&C communications are maintained in many different ways with the help of many different means such as conventional and custom protocols, ports, and encryption. It can be really difficult to detect and stop an attack when it reaches this stage, as C&C messages are almost always lost among other traffic passing through the network. So the best-case scenario is to detect and stop attackers before they ever reach the C&C stage.
Conclusion
The MITRE ATT&CK (Adversarial Techniques, Tactics & Common Knowledge) data model describes the behavior of attackers step-by-step, their methods, and tactics used in various attacks. In addition, in some cases, for a set of indicators classified using ATT&CK (to advance Cyber Threat), you can carry out attribution of intruders, thereby associating intruders with certain groups or malicious campaigns.
The ATT&CK knowledge base and matrix is an extremely powerful tool for red teaming, threat hunting, and building more reliable detection and prevention mechanisms. However, there’s one important point to keep in mind while working with the matrix, which is that it’s updated post-factum. This means it lists existing techniques and tactics. So it doesn’t provide a silver bullet for preventing zero-day attacks.
Nevertheless, it’s a robust framework that can help you build fail-safe security mechanisms. At Apriorit, we actively use this matrix not only when implementing various kinds of security modules and using malware evasion techniques but also when conducting penetration testing and validating the efficiency of defensive methods we develop. We would be glad to help you in your network protection using our knowledge and experience in this area.




