Reliable and secure routers are key to the normal work of any organization. If these devices are poorly protected, they can expose corporate networks to hacking, data leaks, industrial espionage, and other cybersecurity risks.
Learn about the key attack vectors against routers and best practices to secure them. We’ll also share our experience using FACT to discover first-day vulnerabilities in Xiaomi Mi Router firmware.
This article will be useful for embedded software development and testing teams that heavily rely on remote connections in their projects and want to ensure the protection of their routers.
Why should you care about router firmware security?
Routers are one of the priority hacking targets since they are the foundation of any organization’s network. Malicious actors abuse router firmware vulnerabilities and hack these devices to bypass an organization’s security system and steal sensitive data of the organization or its end users.
The most common reason for router hacks is unpatched firmware vulnerabilities. Hackers and security researchers constantly discover new router firmware security issues. But they often are left unpatched either by the device manufacturer or by the user, who may not install firmware updates that contain fixes.
We see news about router vulnerabilities and other IoT security concerns along with negative security consequences quite often. Here are a few examples of recently discovered vulnerabilities and possible consequences of exploiting them:
- Researchers at IoT Inspector discovered 226 potential vulnerabilities in nine popular router models. The researchers focused on devices popular among private users and small organizations. The discovered vulnerabilities made it possible to connect to routers using default credentials, extract the encryption key, access hardcoded credentials, etc.
- Microsoft has reported vulnerabilities in the firmware for Netgear routers, which are popular within small and medium-sized organizations. Exploiting three critical weaknesses allows malicious actors to bypass authentication, access router management pages, and read any information stored on those pages.
- Cisco released vulnerable firmware for several devices of its Small Business RV router series. The most severe vulnerabilities of these routers allowed a hacker to bypass router authentication, install unsigned firmware updates, and even execute code with root privileges. The company quickly patched these vulnerabilities after discovering them.
As you can see, vulnerabilities in router embedded software can lead to dangerous hacking activity and security incidents. Such incidents can subject organizations to the following risks:
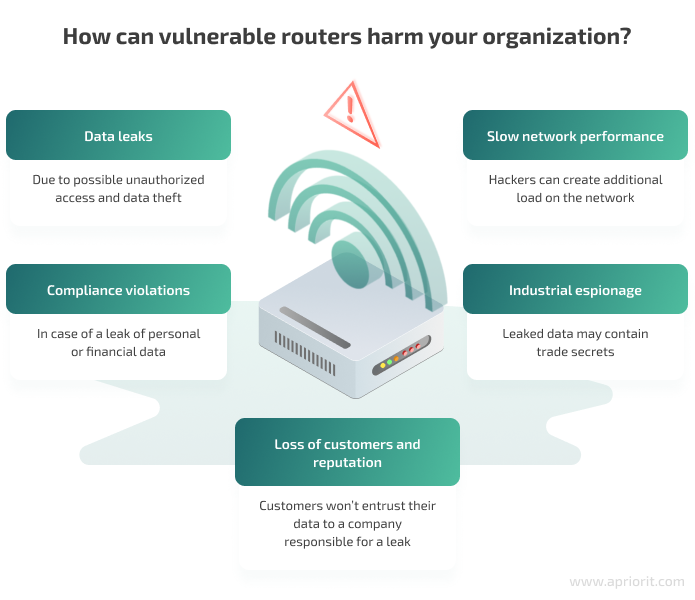
Malicious actors can inflict these risks on organizations by exploiting common router firmware vulnerabilities. In the next section, we examine how hackers usually compromise routers.
Looking to strengthen your cybersecurity defenses?
Partner with Apriorit to uncover hidden vulnerabilities in your systems and optimize your software & firmware security.
Key router attack vectors
Understanding how a router can get compromised is the first step towards improving its security. Hackers usually look for known or common gaps in router security to get inside an organization’s network. Here are the key vectors of router attacks:
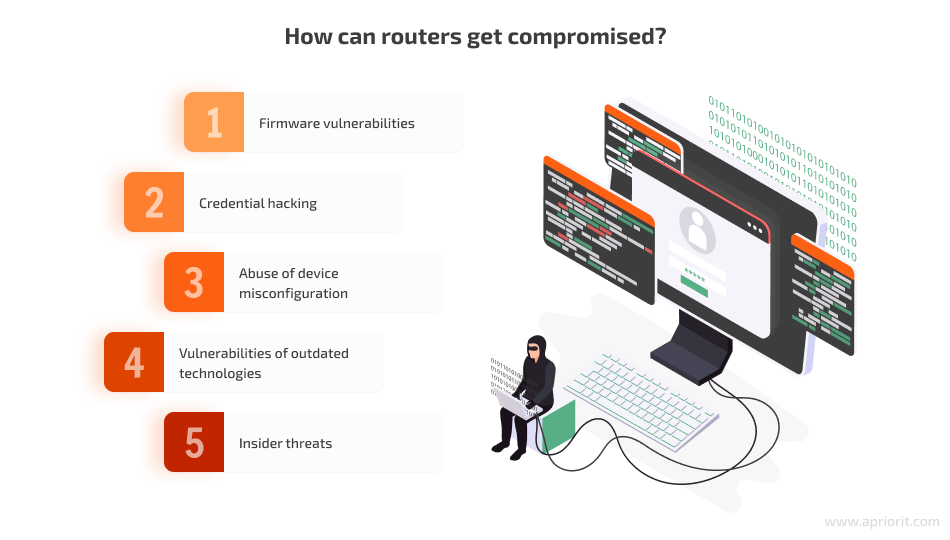
- Firmware vulnerabilities. As shown in the Cisco example above, manufacturers of popular device models can fail to notice security vulnerabilities in routers when preparing them for release. This generally happens because of human errors and lack of security testing. Malicious actors carefully examine new firmware versions to find their way in.
- Credential hacking. Using default or weak router credentials is a common bad security practice. Some organizations don’t bother changing default passwords or set easy-to-remember passwords. Such carelessness allows hackers to brute force credentials or simply use the default credentials to access router configurations.
- Abuse of device misconfiguration. Most popular router manufacturers leave security configurations up to end users. For example, a user can enable Wi-Fi protected setup (WPS) in an attempt to make a router work faster. Cybersecurity best practices call for disabling such router features, as they help malicious actors gain access to router configurations and listen to traffic.
- Vulnerabilities of outdated technologies. The firmware that controls the router can be based on old libraries, security checks, and other architectural elements. These outdated elements might have known security vulnerabilities that hackers can abuse. Fixing these vulnerabilities would require a router manufacturer to completely rework firmware, which is expensive and complicated. This attack vector is more common for devices that are several years old.
- Insider threats. Privileged users inside an organization have access to router configurations and can weaken device security accidentally or with malicious intent. Such activities can create additional vulnerabilities in an organization’s security. Admins can also fly under a security system’s radar because changes in configurations are made by a trusted user.
The good news is that you can discover router security issues and fix them before adding a device to your network. In the next section, we take a look at a practical example of detecting first-day vulnerabilities in router firmware.
Read also
12 Common Attacks on Embedded Systems and How to Prevent Them
Know what security risks to expect when handling embedded systems and discover valuable tips for preventing possible attacks. Apriorit specialists share helpful insights to help you strengthen your embedded systems and protect them against different vulnerabilities.
How to discover firmware vulnerabilities: a practical example
When talking about searching for vulnerabilities, we usually mean discovering first-day vulnerabilities — security issues that were already discovered and reported. The details of a reported first-day vulnerability help both for manufacturers to release a patch for their product and for malicious actors hack the affected software. Though you often hear about zero-day vulnerabilities, searching for them is a challenging process of trial and error, as the weaknesses are still unknown.
The search for first-day vulnerabilities starts with discovering libraries inside the router firmware. You need to gather library names and versions, then look for vulnerability reports on these libraries in vulnerability databases.
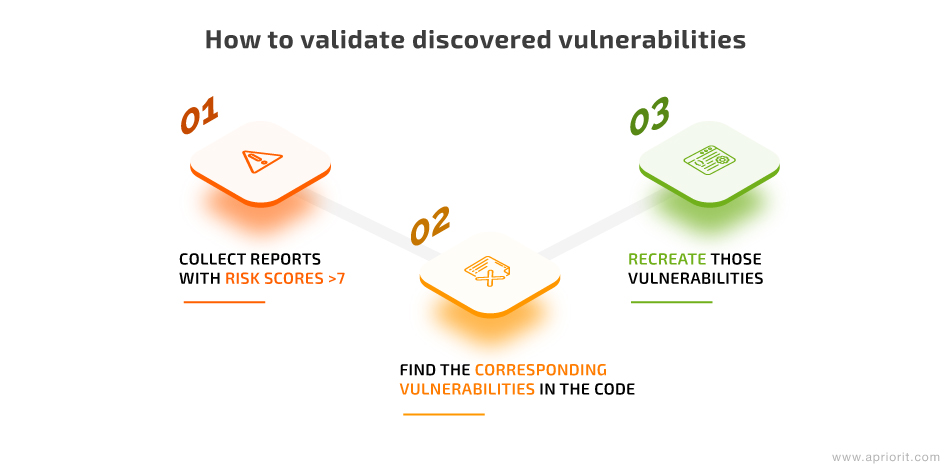
Then, look at whether your firmware has the reported vulnerabilities, recreate them, and move to fix them.
We described this process in detail in one of our previous articles, so make sure to check it out:
Read also
How to Search for Vulnerabilities in Embedded Software
Want to secure your embedded software for Linux-based systems? Apriorit specialists share useful techniques for conducting swift and thorough vulnerability searches, automating the process, and validating potential security threats.
For this article, we decided to show you the real-life process of searching for first-day vulnerabilities by examining firmware for the Xiaomi Mi Router 4A Gigabit Edition. We’ll use Firmware Analysis and Comparison Tool (FACT) — a tool for automated firmware analysis and searching for vulnerability reports.
We often rely on FACT in our embedded development and reverse engineering projects, as it saves a ton of time by automating part of the vulnerability search. FACT can analyze Linux-based firmware, discover libraries inside it, and find corresponding vulnerability reports in the National Vulnerability Database.
During this vulnerability search, we used the d6fd7d8ace1f222062ccc8ee239e796c2b1633bd revision of FACT downloaded from the official source and installed according to the instructions. We installed it on a virtual machine with Linux Mint 18 x64, 8 GB RAM, and 4 CPU cores.
When we open the firmware file with 7zip, we see that it’s a SquashFS image with rootfs inside:
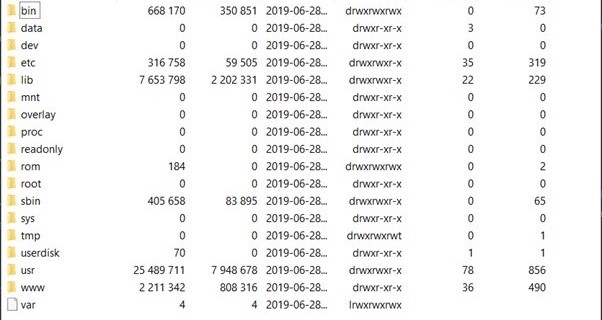
Image 1. Contents of the Xiaomi Mi Router 4A Gigabit Edition firmware
FACT can work with SquashFS images, so we can simply use this .bin file as our input. Let’s launch the tool with this command:
~/FACT_core/start_all_installed_fact_componentsWe’ll wait till the flow of console messages stops, then launch the browser and access the tool via http://localhost:5000. We see this welcome page:
Image 2. FACT welcome page
Now, we select Upload from the menu above to upload the firmware we want to analyze. The form for uploading firmware looks like this:
Image 3. Form for uploading firmware in FACT
We select the firmware file that we downloaded earlier with the Browse button. Next, we specify Device Class, Vendor, Device Part, and Version. All the fields except Device Part are needed only to help us identify the firmware to be analyzed. The Device Part helps FACT understand how to parse the uploaded file — in our case, it’s rootfs file.
We also need to flag these additional settings in the form below:
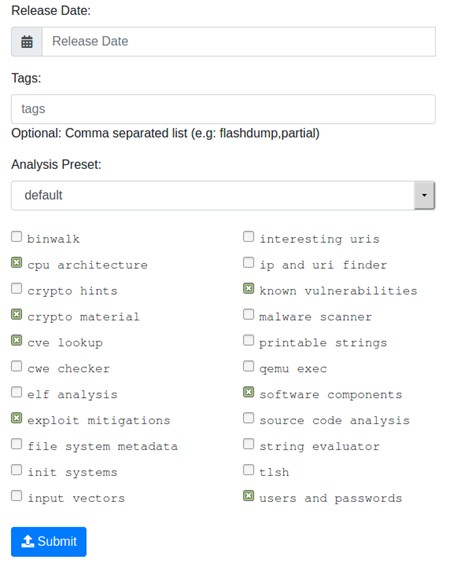
Image 4. Additional settings for firmware analysis
We only need to check the CVE lookup option to conduct a vulnerability search, where CVE stands for common vulnerabilities and exposures. The rest of the options help us search for additional firmware details. Let’s flag the options we need and click Submit:
Image 5. Successful file upload to FACT
FACT confirms the upload has been successful and provides us with a link to the report on the vulnerability scan. The tool will add its findings to the report as it scans the file. At the same time, we’ll see rapid activity in the console where we launched FACT:
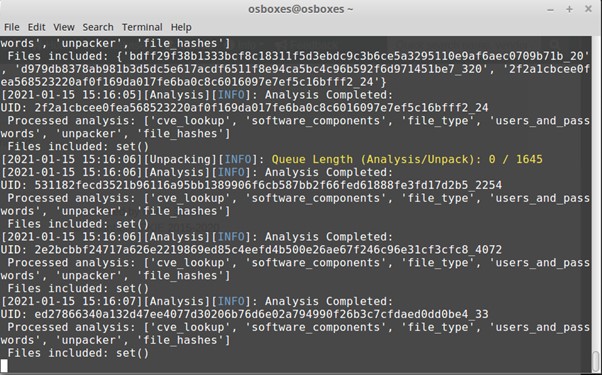
Image 6. Vulnerability search in the console
Here, we are interested in the yellow line about the queue length. It represents the queue of unprocessed elements. In this file, there are 1645 unprocessed elements and we need to wait until the number in this yellow line goes down to 0/0. After that, we can open the link to the report:
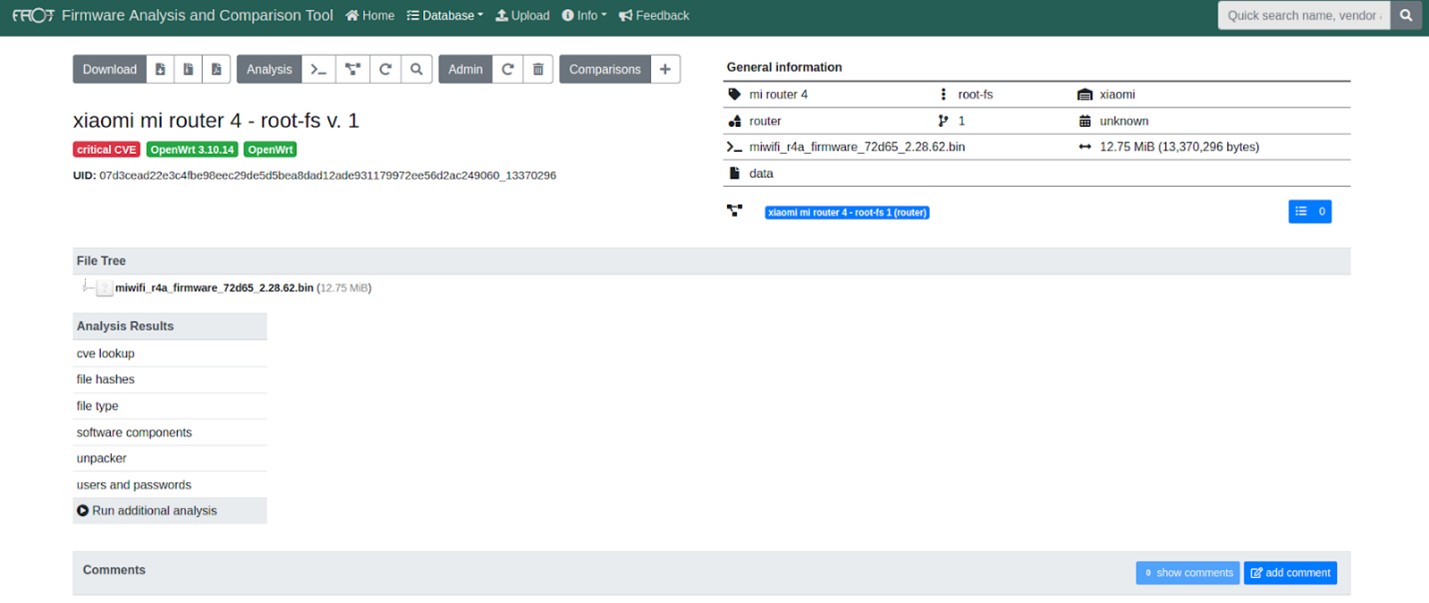
Image 7. Report on the results of the vulnerability search
Let’s click on the CVE lookup tab on the left to see the router vulnerabilities list in the firmware:
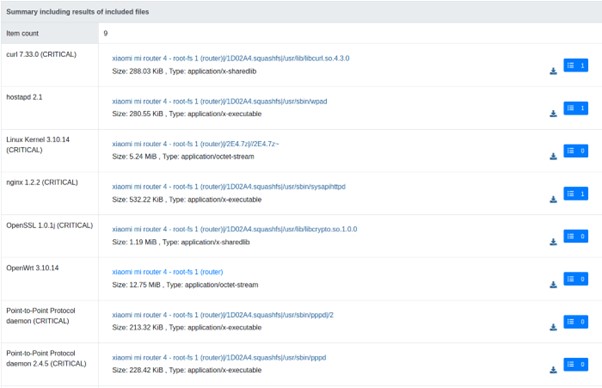
Image 8. Vulnerabilities discovered in the firmware
This tab lists files inside the firmware that contain vulnerabilities. We can choose a file and see the list of vulnerabilities it contains, coupled with links to their descriptions in the National Vulnerability Database (NVD).
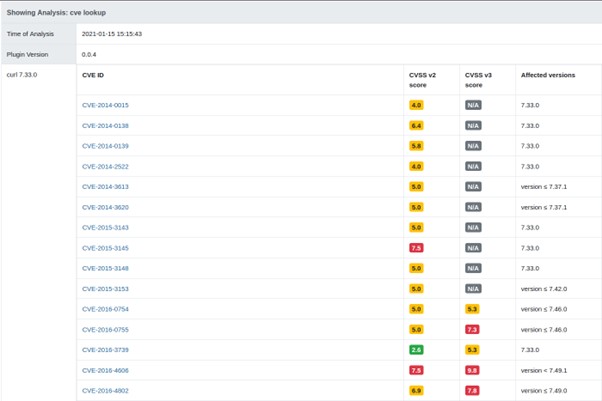
Image 9. Vulnerabilities discovered in a single firmware file
We can download analyzed files from the FACT web interface instead of disassembling the firmware ourselves:
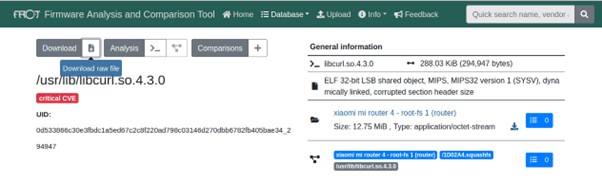
Image 10. Downloading files from the analyzed firmware
Now, we need to validate whether discovered vulnerabilities indeed affect our version of the firmware.
For example, FACT states that the libcurl.so.4.3.0 library contains the curl v7.33.0 library, which has discovered vulnerability CVE-2016-8618. The description of this vulnerability in the References to Advisories, Solutions, and Tools section guides us to its technical details described on the cURL website. And there we can find the patch for fixing this issue.
Our job here is to see whether libcurl.so.4.3.0 has already been patched. The patch changes the alloc_addbyter() function located in /lib/mprintf.c. Let’s upload libcurl.so.4.3.0 to the Interactive Disassembler (IDA) to check its source code. Here we can see some export functions, but no sign of alloc_addbyter().
Then, let’s download curl v7.33.0 source and see that the curl_mvaprintf() export API uses alloc_addbyter(). Let’s run the decompiler on it:
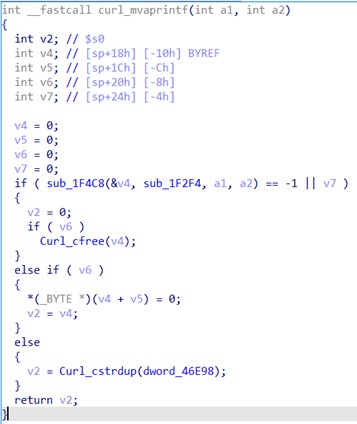
Image 11. Decompiling curl_mvaprintf() API
Now, let’s compare it with the source code:
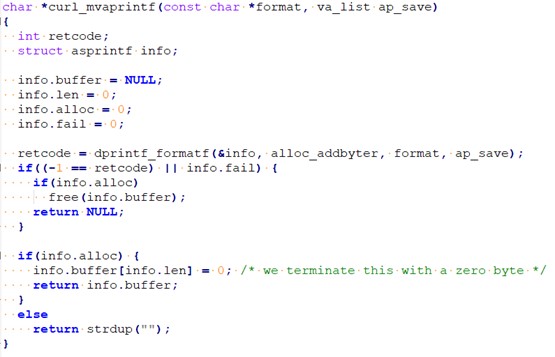
Image 12. curl_mvaprintf() source code
Here we see that sub_1F2F4 corresponds to the alloc_addbyter() function. Let’s continue analyzing the decompiled code:
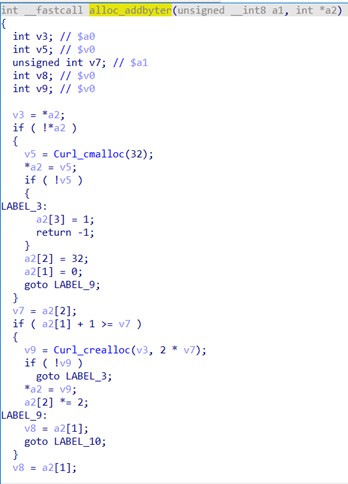
Image 13. Decompiling the alloc_addbyter() API
And here’s the realloc function call that required patching:
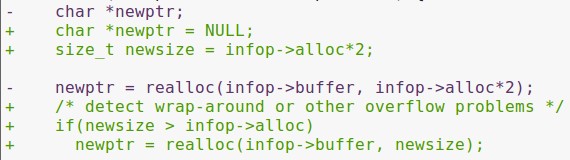
Image 14. Unpatched code with a vulnerability
In the unpatched version of the curl v7.33.0 library, realloc was called from infop->alloc*2 as the second argument. The same goes for the library that our firmware uses: Curl_crealloc(v3, 2 * v7).
This means that we discovered and validated a first-day vulnerability in the router firmware. With this particular vulnerability, we can fix the issue by simply applying the patch from cURL. But that’s not always the case. So let’s take a look at some best practices for mitigating security vulnerabilities in routers and improving their protection.
Read also
A Brief Guide to Assessing Risks with Penetration Testing
Elevate your risk assessment strategy with Apriorit’s guide to penetration testing. Discover the main types of security testing approaches for evaluating cybersecurity risks, their benefits and limitations, and best practices.
7 best practices for securing router firmware
Before you plug a new device into your organization’s network, you need to make sure it’s well-protected and won’t endanger the network by opening the door for some malicious activity. Here’s how you can secure router embedded firmware:
1. Apply firmware updates. This practice sounds a little obvious, but many developers disregard it and put their devices and networks at risk for reasons that are easy to avoid. When working on a new version of firmware, device manufacturers usually aim to improve the device’s performance and fix newly discovered security issues.
2. Search for first-day vulnerabilities. The process we described above is a great way to avoid investing in poorly protected routers and exposing your network to already discovered security issues. Major device manufacturers usually upload firmware files to their websites, so you can download and reverse engineer these files before buying a router.
3. Change default credentials and SSID. Manufacturers may set weak security parameters to help end users install a new router quickly and suggest changing them as soon as possible. However, many people ignore this advice and expose their devices to credential hacking and unprotected malicious access. Default credentials allow hackers to connect to the router. The default service set identifier (SSID) usually contains the name of the device model. With it, hackers can quickly search for first-day vulnerabilities in device firmware and abuse them.
4. Disable unneeded configurations. Modern routers offer their users multiple quality of life improvements: remote access protocols, universal plug and play (UPnP), Telnet, WPS, and more. These protocols and features simplify installing a router and connecting to it. But they also may help hackers breach the device, since all of these protocols have discovered vulnerabilities.
5. Manage access to device configurations. Make sure that only authorized users can access and change router settings. If any user can change device and network settings, you’ll have no control over the entry points to the network and will expose your organization to insider threats. To avoid this, create a list of users who need to manage routers (IT administrators, DevOps engineers, emergency accounts, etc.), manage their credentials in a secure manner, and make sure you can audit them and revoke access.
6. Enforce WPA3 encryption. WPA3 is the latest Wi-Fi encryption standard that was released in 2018. It uses 192-bit cryptography and the SAE method to encrypt data transmitted via Wi-Fi and mitigates security vulnerabilities of WPA2. Most devices produced after 2018 support the newest standard, and only they can connect to a WPA3 network.
7. Conduct penetration testing. Penetration testing helps you discover both first-day and zero-day vulnerabilities in router firmware, as it simulates an external hacking attack. Black-hat pentesting conducted by an independent third party is an unbiased assessment of your organization’s security posture. It also shows you how malicious actors can abuse your routers and how you can secure them.
These practices will help you ensure the security of Wi-Fi routers for your organization and make sure your network is protected from external attacks.
Related project
Developing a Custom Secrets Management Desktop Application for Secure Password Sharing and Storage
Discover our client’s success story of enhancing their organization’s security with a custom secrets management solution. Our experts made sure that only authorized users have access to critical data, significantly improving the client’s security score.

Conclusion
Routers with vulnerable firmware can expose an organization to a security incident and data loss. That’s why you need to carefully examine each device before plugging it into a corporate network.
At Apriorit, we combine our skills in reverse engineering, embedded development, and penetration testing to make sure we deliver not only efficient but well-protected software.
Protect your digital assets
Leverage Apriorit’s comprehensive engineering services and a strong focus on security to elevate your cyber defense.



