Application programming interfaces (APIs) help to integrate services in your software, exchange information between system components, and support other software development functions. Such vast capabilities make them a popular target for cyberattacks. In case of a successful attack, malicious actors can gain unauthorized access to sensitive information, leading to a variety of unpleasant consequences for businesses.
Therefore, it’s crucial to make sure APIs don’t have vulnerabilities that could lead to data leaks or malfunctioning. To help you achieve that, make sure your team comes up with a comprehensive approach to API security. By keeping API protection in mind during all development stages, you can get solid software security, ensure industry compliance, and gain customer trust.
In this article, we explore what API security is, why it matters, and which API security risks and vulnerabilities you should be aware of. You’ll also find six best practices for API protection to elevate your software security. This article will be helpful for software product leaders looking for expertise in API development and security.
What is API security?
During 2022 and 2023, 60% of organizations surveyed by the Ponemon Institute faced at least one API-related breach. And 74% of these endured three or more incidents, revealing how fragile APIs can be.
If attackers manage to compromise API providers, they could compromise all API data and functionality. Malicious attacks have a better chance of being successful if APIs aren’t protected with solid security measures. For example, attackers can inject malicious code to perform unauthorized operations or compromise the back end. To avoid and mitigate such threats, businesses should have a solid API security strategy in place.
API security is a combination of measures, techniques, policies, and practices that software development teams use to protect APIs from threats like unauthorized access, data breaches, and malicious attacks.
The main goal of API security is to ensure the secure exchange of data between different systems. To make that happen, engineers use various practices like elevated authentication, data encryption, input validation, rate limiting, and secure coding principles, which we explore in detail later in this article.
Because APIs play an essential role in software, API security lies at the intersection of three broad areas of security: application security, network security, and information security.
An API security strategy usually covers protection of all application programming interfaces used within a project, including REST APIs, SOAP APIs, and GraphQL APIs. When creating an API security strategy, your developers might need to establish different rules and principles for different API types. Whether these are private, public, partner, composite, or third-party APIs, they usually have different requirements for protection and access rights.
Level up your API game!
Make sure your APIs can face modern security threats by leveraging Apriorit’s 20+ years of experience in software development.
Why is API security important?
A well-rounded API security strategy makes your software more reliable and resilient towards security attacks while also providing extra benefits. Let’s briefly explore a few major advantages this approach can bring to your business:
- Enhanced protection of sensitive data. Establishing robust AI security can help you guarantee the confidentiality of sensitive data being transferred via your software APIs between applications, users, and servers. Also, by securing APIs, your team can make sure that messages sent via APIs haven’t been altered during transmission. Strong data protection mechanisms can help you prevent cybersecurity incidents and data leaks, maintaining a positive business reputation and winning user trust.
- Compliance with industry requirements. Healthcare, finance, and other industries that work with sensitive data are obliged to follow strict cybersecurity regulations, making sure the software they use protects personally identifiable information. Failure to comply can result in cybersecurity incidents, legal issues, and penalties. By thoughtfully designing and protecting APIs, your team can cover most common data security requirements, establishing software development compliance.
- Seamless functioning of complex ecosystems. Modern infrastructures and software products consist of various elements and have many integrated third-party services, which are tricky to take care of all at once. A solid set of API security practices can help your team spot potential vulnerabilities and other issues in a timely manner. Thus, your developers can fix problems as soon as they arise that may lead to communication issues between software components and negatively affect the overall system functioning.
To efficiently protect your APIs, you first need to know what issues to be aware of. Let’s take a closer look at common risks, vulnerabilities, and attacks your team must consider when developing an API security strategy.
Common API security risks and vulnerabilities
The key principle of ensuring API protection is following OWASP API Security Project recommendations. At Apriorit, we carefully study each OWASP project update, ensuring top-notch security for all software projects and protecting APIs from all possible vulnerabilities and risks.
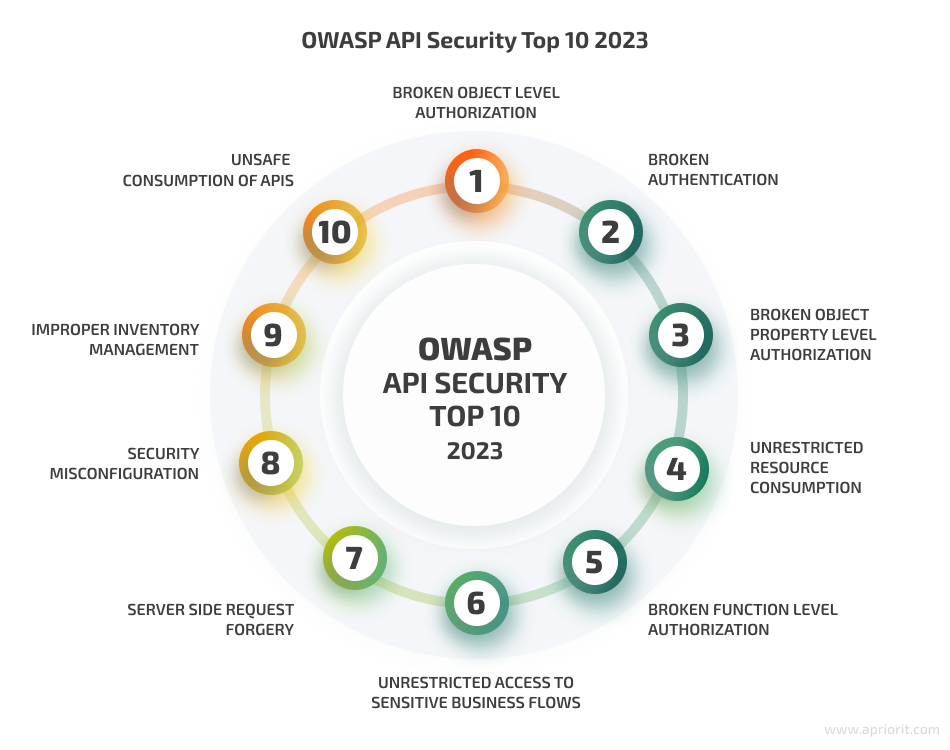
The OWASP list showcases the most widespread threats, but the full list of potential API risks and vulnerabilities is much larger. Your team has to look out for misconfiguration, insecure data transmission, sensitive data exposure, broken access control, and so on. Apart from that, you must secure your APIs from numerous cyber threats like injection attacks, API scanning, data scraping, DoS and DDoS attacks, and business logic abuse.
One blog article isn’t enough to list all API security risks and show ways to manage them. However, in the next section, we try to cover the key areas worth securing in the first place, sharing essential API security best practices from Apriorit’s experience.
Read also
Web Applications: Common Vulnerabilities and Ways to Eliminate Them
Be one step ahead of malicious actors by securing your web applications from potential vulnerabilities and attacks. Read on to find helpful insights from Apriorit experts.
How to secure your APIs
API security is a complex approach that can consist of multiple practices and methods. Which principles and techniques to choose depends on your project’s details. But whatever approach for API security you select, your team must be committed and consistent in implementing it.
At Apriorit, we put lots of effort into ensuring security during API development and maintenance using a variety of methods. In terms of how to secure APIs, we would suggest considering the following six best practices for all projects:

1. Ensure security by design
To avoid the risk of deploying APIs with in-built vulnerabilities and minimize work on security enhancement during later project steps, make sure to implement solid security measures at the API design and development stages.
- Follow the threat modeling approach. This is a systematic approach to identify, evaluate, and mitigate potential threats to an API. Threat modeling will help your team understand who can be granted access to APIs, what data is shared, and where vulnerabilities might exist.
- Secure all endpoints. Reduce the attack surface by limiting the exposure of endpoints and only exposing what’s absolutely necessary. Also, consider implementing the principle of least privilege for accessing all software endpoints.
- Use trusted and secure hosting providers. Providers you choose directly impact the reliability, performance, and security of your API services. Make sure they offer robust security measures like firewalls and regular security updates, and check hosting providers’ certifications and audits.
- Establish regular logging and monitoring practices. Start with identifying and clearly defining all elements and activities that must be logged, including non-security parameters like API performance, speed, and uptime. Thus, your team can draw a baseline of what is considered normal and easily outline unusual patterns, traffic spikes, and suspicious activities.
- Implement incident response. Implement a robust incident response plan so that your team can immediately react to potential danger and minimize the impact of breaches. Consider documenting response activities and establishing clear communication channels between IT, security, legal, and other relevant teams.
2. Control API access and use
While authentication helps with verifying users and entities that interact with APIs, authorization is concerned with what data they have access to. Therefore, securing APIs on these levels is crucial.
- Secure API access. Make sure to allow only authenticated users to call APIs and enable different levels of permissions for different users. It’s also a good practice to block requesters who exceed the rate limit, as it might be a sign of malicious activity. If your team allows certain non-admin users to access API data, ensure these users are granted read-only access.
- Monitor and control API use. Double-check that public APIs aren’t exposed to unvalidated requests, even from authorized users. Consider setting a limited duration for API sessions and making tokens expire at regular intervals to prevent replay attacks.
- Enable reliable security principles. Elevate your API authentication and authorization with proven methods and technologies like multi-factor authentication (MFA), OAuth 2.0, API keys, JSON Web Tokens, strong password policies, role-based access control, attribute-based access control, and a zero trust policy.
Related project
Enhancing the Security and Performance of a Virtual Application Delivery Platform
Explore insights into how the Apriorit team helped our client implement custom features to provide a better user experience, improve the client’s product security, and make the product more efficient.

3. Protect sensitive data handled by APIs
Since APIs act as the infrastructure’s veins in transferring data, protecting the way they handle data is a significant part of establishing API security. Apart from user and corporate data, make sure to secure user credentials to avoid incidents like the one that happened to Spoutible. Their publicly exposed API could have led to attackers stealing users’ 2FA secrets, encrypted password reset tokens, and more.
- Enable data classification. Categorizing the data handled by APIs can help your team choose relevant security measures to protect sensitive information and ensure compliance with regulatory requirements. You can enforce multiple data sensitivity levels for public, internal, confidential, and restricted records.
- Encrypt sensitive data. There are a variety of encryption techniques to secure data both at rest and in transit between clients and servers. You can use HTTPS, SSL/TLS protocols, and symmetric and asymmetric encryption to protect sessions between a client and a server, as well as to exchange data within these sessions. Also, consider masking or redacting sensitive data in API responses for better protection.
- Expose as little data as possible. Make sure your team limits the accidental exposure of sensitive information and avoids common development mistakes like storing passwords, keys, and other secrets inside APIs. To do that, set clear development guidelines and enable periodic audits to identify and address inadvertent data exposure.
4. Adopt rate limits and gateways
Rate limiting and API gateways are essential mechanisms to prevent abuse and misuse of your APIs.
- Implement rate limiting. By limiting how often an API is called, your team can ensure that an API remains available to legitimate requests. Consider using this practice against DDoS attacks, aggressive polling, and credential stuffing. Rate limits can be different for each specific API endpoint.
- Use API gateways. This practice ensures centralized control of all APIs, since an API gateway serves as a single entry point for all API requests. Thus, your team can simplify management of multiple APIs, streamlining routing, monitoring, and access control. API gateways also help to mitigate security risks by acting as a protective barrier between clients and backend services.
5. Prioritize secure coding practices
As with any software component, following secure coding practices when developing APIs brings lots of benefits in the long run. At Apriorit, we also follow the secure software development lifecycle (SDLC) approach, which requires thorough planning and dedication. Let’s outline a few key practices to help your developers bring more security to APIs when coding:
- Apply input validation and sanitization to prevent SQL injection, Cross-Site Scripting (XSS), and other types of injection attacks by ensuring that your application processes only properly formatted and expected data.
- Introduce content security policies to control what content your application can execute and load.
- Enable a Cross-Origin Resource Sharing (CORS) policy to control which domains are allowed to access your APIs.
- Use IP allow-lists and deny-lists to allow/block certain IPs from accessing your APIs.
- Establish scheduled code reviews, fostering a security-oriented culture within development teams. At Apriorit, we conduct regular code reviews with a focus on security and offer code audit services.
6. Establish regular audits and updates
Once your APIs are securely developed and implemented into organizational or software infrastructure, your team must regularly check and improve API security during the support and maintenance stage.
- Conduct API security audits and penetration testing. These measures will help your team assess the current protection of your APIs and plan appropriate ways to enhance API security. Consider hiring certified independent experts for penetration tests and audits to help you detect and address potential gaps, improving your API’s security posture.
- Establish patch management. Make sure your team deploys virtual patching to address detected vulnerabilities. Regularly patch and update server software, and enable API version control measures.
- Implement API discovery and inventorying processes. By having an updated list of all APIs, your team can significantly improve API management and immediately and fully react in case any security vulnerabilities appear or attacks arise. Make sure to document details like API names, versions, endpoints, and authentication methods. You might also want to automate the API discovery process; according to the Cloudflare 2024 API Security & Management Report, Cloudflare found 30.7% more API endpoints through machine learning-based discovery compared to what organizations self-reported. Consider using tools to automatically scan networks, code repositories, and documentation to discover APIs.
- Conduct regular vulnerability assessments. Timely identification of vulnerabilities is essential for further mitigation of potential threats. Consider employing behavioral, pattern, and heuristic analysis for proactive vulnerability and risk detection.
Read also
6 Most Common Security Issues in API Development and How to Fix Them
Find out the most widespread API vulnerabilities and how malicious actors can exploit them. Read the full text to discover practical ways to protect your APIs from such security issues during development.
How Apriorit can help you with API development and security
With 20+ years of development experience, Apriorit has gathered best practices for creating, protecting, integrating, and maintaining APIs. We’ve already helped dozens of clients expand their product’s functionality via third-party integrations, relying on a security-first approach.
Whether you need assistance creating an API management strategy, scaling your API ecosystem, selecting the technology stack, or building custom APIs, Apriorit experts are ready to take the development burden off your shoulders.
By following principles of a secure software development lifecycle, we make sure each and every solution performs exceptionally and has strong protection.

- Build new custom APIs. By delegating API creation to Apriorit, you’ll receive reliable and secure products tailored to your project needs. Custom APIs can help your business seamlessly connect systems within your infrastructure and better control data flow, taking into account your project specifics.
- Assure the quality and security of your APIs. Let our experienced engineers bulletproof your systems with API security testing, data encryption, and other proven security techniques. We’ll aso ensure scalability to meet potential traffic spikes, helping your products meet increased demand.
- Integrate APIs of any complexity. We’ll choose the most suitable API integration protocol for your project needs, ensuring smooth integration into your product.
- Maintain and improve existing API solutions. Apriorit engineers will keep all your APIs well-managed by reviewing and updating old APIs, supporting legacy code, and ensuring a smooth connection with all connected apps, systems, and devices.
By entrusting Apriorit with API creation, you’ll get full-cycle development and support at each stage, from research and design to performance optimization and troubleshooting.
Conclusion
APIs are often used to connect different software components and transfer data. Especially with the popularity of microservices and serverless architectures that consist of multiple components, APIs have become a must for almost every enterprise application’s basic functionality.
Going the extra mile when securing APIs helps businesses safeguard corporate and user data, meet data privacy requirements, and ensure smooth product functioning. All these benefits play an important role in gaining users’ trust and upholding an organization’s reputation.
However, implementing robust API protection is complex. Your team must have solid knowledge and experience in API development and integrations and must think big when it comes to your API management strategy.
At Apriorit, we have dedicated API development teams with a strong focus on cybersecurity and experience applying a secure SDLC approach. Whatever API project you have in mind, our engineers are ready to assist you.
Need help securing your APIs?
Invest in API data protection for long-term success and resilience against cyber threats. Entrust API creation and support tasks to experienced Apriorit engineers.



