Cybercriminals constantly find new ways to steal personal and financial data, disrupt business operations, destroy reputations, and commit fraud. To protect your business from threats powered by new technologies, you’ll need to adjust your approach to building software and adopt new technologies and methods in your software development process.
In this article, we explore the latest cybersecurity strategies and technologies that will help you protect your digital products in 2025 and beyond, as well as the main factors contributing to the shift in the cybersecurity landscape.
This article will be useful for CTOs and leaders of development and testing teams who need to stay informed about the latest trends in cybersecurity and adapt their security measures to emerging threats.
Top factors contributing to cybersecurity challenges in 2025
In the past several years, we’ve seen a significant shift in how businesses approach product development. AI advancements, cloud adoption, and the evolution of IoT have opened many doors to both businesses and cybercriminals.
Before we talk about what the cybersecurity market has to offer against these new challenges, let’s look at the main societal and technological changes in the current world that bring security challenges along with opportunities.
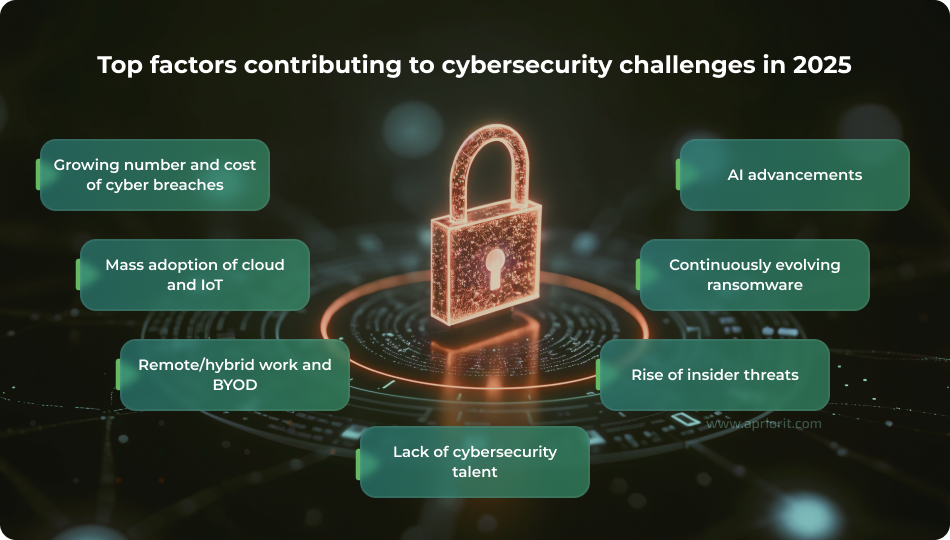
Growing number and cost of cyber breaches
One thing we as cybersecurity specialists deem stable year after year is the growth in the number and cost of security breaches. In 2025, the cost of breaches is expected to reach $10.5 trillion, growing at a rate of 15% annually.
Statista has been tracking the continuous growth of cybercrime for 11 years, and they expect the global cost of cybercrime to increase 69% between 2023 and 2028, reaching $13.83 trillion in 2028.
As the world becomes increasingly digital, the number of threats can only grow. However, the cybersecurity industry doesn’t stand still and is constantly developing more efficient defense mechanisms against all threats. We’ll discuss them later in this article.
AI advancements
Artificial intelligence (AI) has been around for years now, and while it has become a great tool for cybersecurity specialists and businesses, hackers haven’t been sleeping on this technology either. Cybercriminals use AI for all purposes, from small tasks like conducting phishing attacks, evading detection, and discovering vulnerabilities to full-scale end-to-end cyberattacks involving advanced malware and ransomware.
In 2025, we expect AI-driven threats to become even more sophisticated. One reason for this is the rise of generative AI (GenAI) — a form of artificial intelligence that is able to create new content like images, text, and even multimedia, rather than simply recognizing patterns or making predictions based on existing data.
As one of the most popular and fastest-growing categories of AI models, generative AI has its own set of security risks. They include:

- Use for powerful cyber attacks. Hackers can use generative AI for faster, larger, and more efficient cyber attacks. GenAI is able to create highly convincing phishing emails and variations of malicious code or malware. Hackers can also use it to enhance their brute-force attacks by generating and testing a large number of passwords.
- New vulnerabilities. As businesses integrate generative AI into their systems, it creates new entry points for hackers, who can target critical infrastructure through data poisoning, prompt injection, model inversion, perturbation, and more.
- Privacy and data storage risks. When using AI, businesses can share their sensitive data with third-party AI systems, placing it in third-party storage spaces. Without encryption and access controls implemented by companies that use AI or third-party providers, data can easily be misused or leaked.
Need to fortify your product against cyber threats?
Our team of software engineering experts can help you build a robust and efficient cybersecurity strategy!
Mass adoption of cloud and IoT
The cloud has become a default technology for most infrastructures. If your product isn’t fully in the cloud, you probably use the cloud for at least part of your processes. But cloud advantages like fast time to market, convenience of use, and cost reduction come with their own cybersecurity risks.

There are a few specific cloud cybersecurity trends for 2025 that are expected to emerge as a response to these factors according to Google:
- Continued use of zero-day and n-day vulnerabilities. Abuse of zero-day vulnerabilities is expected to continue growing in 2025. Attackers will continue using zero- and n-day vulnerabilities to maintain access to cloud environments for longer periods of time. In particular, hackers will use edge or IoT devices and virtualization software, as they’re more challenging to monitor than traditional endpoints like desktop computers or laptops.
- Increased risk of compromised identities in hybrid environments. The integration of identities spanning on-premises and multi-cloud architectures amplifies the potential impact of compromised credentials. Organizations face the challenge of securing distributed operations while minimizing risks from identity breaches.
- Heightened regulatory scrutiny. With critical infrastructure increasingly reliant on hyperscale cloud services, cloud providers face growing regulatory pressure to meet stringent controls and resilience standards. This poses challenges in ensuring compliance across diverse jurisdictions while maintaining operational agility.
To combat these threats, businesses will need to integrate efficient scanning and process monitoring into their systems to detect sophisticated threats that bypass traditional detection frameworks. One example is cloud-native security information and event management (SIEM) solutions, which Google predicts to be more widely adopted among businesses.
Continuously evolving ransomware
Ransomware has been a threat forever, and it’s not going anywhere in 2025. On the contrary, it’s expected to become more sophisticated and opportunistic, as cybercriminals will use their refined tactics to exploit zero-day vulnerabilities.
Examples of ransomware evolution are the appearance of ransomware-as-a-service (RaaS) platforms, new detection evading techniques like polymorphic malware, and the adoption of double extortion strategies.
Ransomware will continue targeting enterprises, so both organizations and customers should be educated on the typical threats. In 2025, attackers are expected to shift from performing the ransom themselves to selling exploit and vulnerability data to third parties.
Read also
How to Protect Cloud-based Systems from Ransomware
Learn how ransomware infects cloud services and how you can protect your cloud-based systems from it.
Normalization of remote/hybrid work and BYOD
Remote and hybrid work became the norm in 2020, and this trend shows no sign of slowing down. More and more employees are using their personal devices for work, and bring your own device (BYOD) has become common even in offices, at least when it comes to mobile devices.
One of the cybersecurity trends in 2025 is the growth in cases of mobile device and personal device exploitation. Hackers will use mobile devices to get to sensitive corporate data stored on them. Organizations will need to put a strong emphasis on deploying mobile device management (MDM) solutions, educating employees, and enforcing strict security policies.
Rise of insider threats
Insider threats became more frequent in 2024 and remain a major cybersecurity concern this year too. According to the 2024 Insider Threat Report by Cybersecurity Insiders, 83% of organizations reported at least one insider attack in the last year. Moreover, organizations that experienced 11–20 insider attacks saw a fivefold increase in the number of attacks compared to 2023 — moving from just 4% to 21% in the last 12 months.
With insider threats on the rise, it’s critical for businesses to recognize the real dangers that originate from inside their digital ecosystem while putting into practice effective threat management strategies to address them.
To protect sensitive data, organizations need to focus on insider threat detection capabilities as well as employee training and awareness. If your organization uses cloud infrastructure, you’ll need to put even more emphasis on monitoring, as detecting insider attacks is more challenging in the cloud.
Lack of cybersecurity talent
The latest Cybersecurity Workforce Study from ISC2 estimates that the global cybersecurity workforce gap reached a record 4.8 million in 2024, a 19% increase from 2023. This gap represents the number of additional cybersecurity professionals needed to meet demand. Gartner predicts that this shortage will result in over half of significant cybersecurity incidents.
According to ISC2, 67% of organizations are exposed to security risks due to a shortage of cybersecurity professionals. Gartner warns that this talent gap will contribute to more than half of major cybersecurity incidents.
The shortage of cybersecurity professionals has left 67% of organizations vulnerable to security issues according to ISC2. As a result, not only will companies struggle to fight immediate threats; they will also find it challenging to build a comprehensive security strategy or implement new security systems to protect their products in the long run.
Now that we’ve talked about factors behind the growth in security threats in 2025, let’s look at emerging trends in cybersecurity and technologies you can apply to protect your software for years to come.
Trend #1. Growing adoption of AI for threat management
As organizations’ digital infrastructures become more complex, hackers get endless opportunities to attack and infiltrate systems through multiple entry points that make up the attack surface.
Several factors contribute to the growing complexity of organizational attack surfaces, including:
- Diverse technologies
- Cloud computing
- Internet of Things
- Mobile devices
- Third-party integrations
- Complex networks
- Human factors
All of these create possible attack vectors for hackers, allowing them to violate your system to steal data and conduct malicious operations. This can result in data loss, reputational damage, and interruptions in business operations.
As you can imagine, it’s extremely challenging to keep track of all potential threats and vulnerabilities when software systems are so complex. Here’s where AI and machine learning (ML) come into play.
If you’d like to leverage the power of AI and ML for your product’s security, particularly to reduce human intervention in anomaly detection and event prediction, consider threat detection, identification, and response (TDIR) and user and entity behavior analytics (UEBA) tools. At Apriorit, we can help you integrate these tools into your existing systems and products. Contact us for a consultation and estimate.
Need to prepare your product for the future?
Our team of cybersecurity experts can help you update your product with the latest technologies to protect it against current and future threats!
Trend #2. Use of advanced cryptography within AI systems
All cybersecurity experts, including those at Apriorit, have been preaching the importance of cryptography and encryption for years. However, in 2025, we expect these fundamental cybersecurity tools to become more advanced and be applied to AI systems that currently pose multiple risks for data exposure.
One advanced encryption system is attribute-based encryption (ABE), which allows access control policies to be embedded directly into encrypted data. ABE can enhance AI’s data security and implement fine-grained access control over sensitive records.
AI models often operate in dynamic environments where access control requirements may change over time. ABE can adapt access controls based on changing project requirements, user roles, and other contextual factors without the need to re-encrypt data.
Another critical consideration for the future of cryptography is preparing for the adoption of quantum computers. Once fully realized, quantum computers will have the power to break many existing cryptographic algorithms, such as RSA and ECC, making them insecure. To address this future threat, businesses will soon need to invest in post-quantum cryptography (PQC), which uses algorithms designed to resist quantum attacks.
Quantum computers, once fully developed, will be capable of breaking widely used cryptographic algorithms like RSA and ECC, rendering them insecure. To stay ahead of this threat, businesses must start investing in post-quantum cryptography (PQC), which relies on algorithms designed to withstand quantum attacks.
Implementing PQC into working systems is currently quite challenging. Many PQC algorithms are still underdeveloped and computationally heavy, which can impact the performance of the systems they are integrated into. However, businesses need to be prepared to integrate PQC algorithms into their systems as soon as they become widely available. For this, they need to implement crypto-agility. Crypto-agile systems allow you to quickly adapt to new cryptographic standards without significantly disrupting your operations or re-engineering existing systems. By making your AI system crypto-agile, you can future-proof it against both classic and quantum threats.
Apriorit experts can help you implement reliable encryption to protect sensitive data within AI systems and ensure strict access control to minimize data leak risks.
Read also
How to Build & Implement an Encryption Framework for an Android App
Learn how to develop a framework to implement transparent encryption that secures data even if the device is rooted.

Trend #3. Modernized authentication
Identity management is increasingly under threat as cyber attackers employ more sophisticated techniques. Advanced phishing, credential stuffing, and social engineering have contributed to the weakening of traditional identity management systems, so in 2025, there’s a glaring need for a new approach to identity management.
In 2025, businesses will be looking for more technologically advanced ways to protect their data from unauthorized access. One of the top cybersecurity trends of 2025 in this area is the rise of passwordless technology.
Passwordless technology shifts from traditional passwords to more secure and user-friendly authentication methods like:
- Biometrics
- Smart cards
- Devices
- Security keys
This technology addresses the challenges associated with traditional passwords like weak user practices, password reuse, and phishing, offering your users more security and convenience.
You can pair passwordless technologies with AI to further protect your product’s identity management. AI-driven identity products allow you to analyze the behavior of authorized users to detect any anomalies early, thus detecting cases of authentication hacking and unauthorized access.
Trend #4. Zero trust as a necessity
The concept of zero trust isn’t new, but in 2025 it’s bound to become a necessity rather than an option due to the increasing sophistication of insider threats and cyber attacks. This approach to authentication and monitoring is a significant shift from traditional implicit trust in users or devices to a model where trust is never assumed.
Here are the key principles of zero trust that make this security model transformative:

- Trust must be earned continuously. Every user and device should prove it has a right to access the system, and instead of giving access one time, zero trust systems continuously verify every user on the network.
- Constant monitoring. Zero trust relies on real-time analytics to detect anomalies and potential security threats. Behavioral analysis contributes to the early identification of malicious activities.
- Network micro-segmentation. Zero trust encourages dividing networks into smaller, isolated segments. This limits lateral movement for potential attackers, containing the impact of a security breach.
- Principle of least privilege. Users are granted the minimum level of access required to perform their duties. This principle ensures that even if a user’s credentials are compromised, damage to the overall system is minimized.
Zero trust can significantly reduce the risk of insider threats and hacking by constantly verifying users and providing them with fine-grained access to sensitive data.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Learn how we implemented new features in a low-level vulnerability detection engine and improved the platform’s stability and user experience.

Trend #5. Focus on resilience and digital immune system adoption
Security incidents can not only cause data breaches but also disrupt day-to-day operations, resulting in further reputational and monetary losses. That’s why in 2025, businesses will focus on resilience in their software development and adopt the concept of a digital immune system, as coined by Gartner.
Drawing inspiration from the adaptive nature of biological immune systems, a digital immune system aims to be a dynamic, self-learning defense mechanism that can identify threats and withstand disruptions to support continuous and uninterrupted work.
The principles of a digital immune system include:
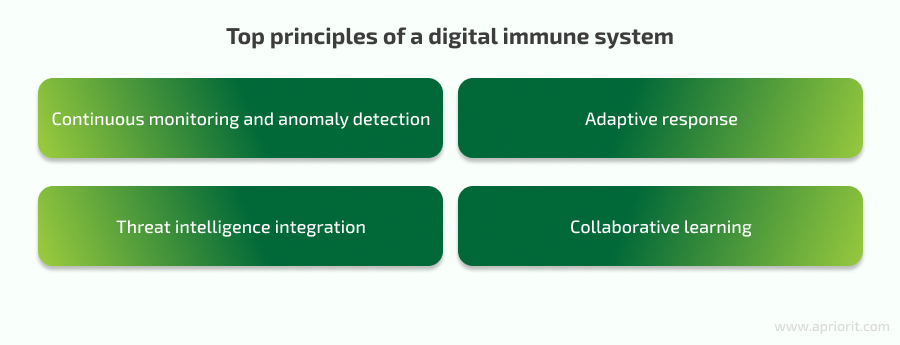
- Continuous monitoring and anomaly detection. Anomaly detection mechanisms use baselines of normal behavior and alert all systems to all potential threats.
- Adaptive response. The system automatically responds to threats depending on their type and severity.
- Threat intelligence integration. Digital immune systems integrate threat intelligence feeds and use real-time data on emerging threats to enhance their detection and response capabilities.
- Collaborative learning. Insights from one part of the system contribute to the overall defense posture, creating an interconnected security infrastructure.
To further fortify their security and create fault-tolerant infrastructure, organizations in 2024 will use DevSecOps and CloudOps in combination with digital immune systems.
DevSecOps (development, security, and operations) offers a modern approach to software infrastructure development that integrates security at each stage of the software development lifecycle. This allows organizations to create inherently protected products and build automated security pipelines from the very start of their development projects.
CloudOps (cloud operations) complements this security-first strategy by centralizing security management and allowing for efficient coordination and response across the entire cloud environment.
You can combine a digital immune system, CloudOps, and DevSecOps to create a comprehensive protection system. Based on continuous monitoring, such a system can quickly respond to cybersecurity incidents and automatically adapt to future threats.
Trend #6. Rust programming language for secure development
Rust is becoming a go-to language for building secure software. It offers unique features that address many common vulnerabilities associated with traditional languages like C and C++. Features that make Rust a good option for cybersecurity are:
- Memory safety. Rust enforces strict memory management rules through its ownership model and other features, helping developers manage memory-related processes and avoid errors, crashes, and security issues.
- Concurrency safety. Rust’s design ensures that different parts of the program don’t change the same data at the same time, making it safer and more reliable for complex, multitasking systems.
- Error handling. With its robust type system, Rust forces developers to handle potential errors explicitly, reducing the likelihood of unexpected runtime failures.
- High performance. Rust offers zero-cost abstractions, making it as efficient as low-level languages like C while maintaining higher security standards.
What solutions can you use Rust for?
Rust excels at low-level system programming, especially for developing operating systems, drivers, and embedded systems. Its support for asynchronous programming also makes it great for building high-performance network systems and tools. Rust is becoming a popular choice for building cybersecurity products like encryption systems and intrusion detection tools. At Apriorit, we also use Rust for cybersecurity tasks, such as performing penetration testing and building cryptographic applications.
Read also
Secure Development with Rust: Benefits, Features, and Use Cases
Explore how Rust can enhance security, boost performance, and simplify development for your project. Read our in-depth article on Rust’s potential for cybersecurity solutions.

How Apriorit can help you safeguard your product in 2025
Apriorit is a team of cybersecurity experts with over 20 years of experience building secure IT solutions for clients that are protected from most cyber threats. Our deep industry knowledge and ability to solve the most complex technical tasks make us a trusted partner in addressing existing and upcoming challenges in securing your product.
You can leverage the experience of our cybersecurity specialists and engineers in all aspects of cybersecurity protection, from addressing particular issues to creating full-scale products with a security-first approach.
Here are just a few examples of projects we’ve worked on:
- A custom enterprise MDM solution to help our client securely manage Android tablets. We implemented enhanced data security and an admin panel for centralized device management.
- A SaaS-based cybersecurity platform for a worldwide provider, to which we applied our rare skills to implement new features in a low-level vulnerability detection engine.
- A corporate network monitoring product that we enhanced with centralization features and process optimization.
- A custom secrets management system for internal corporate use. We applied our strong knowledge of cybersecurity to deliver an effective and bulletproof desktop app for storing and sharing passwords.
Apriorit is a leader in cybersecurity solution development with over 20 years of experience creating solutions for a wide range of needs. Cybersecurity is the foundation of our work, and we have built a strong base of expertise and extensive resources over the years. With a pool of top cybersecurity talent, you can rely on us at any stage of your development project — from planning to maintenance and support. We can also help you ensure:
- Full compliance with the latest data privacy and security policies and regulations
- Impeccable system security and protection from the latest threats
- That your current product is up to date and all security-critical updates are installed
- Adherence to a secure software development lifecycle (SDLC) to minimize vulnerabilities at every stage of development and ensure robust security practices are integrated into your project from the start
No matter what challenges 2025 puts before us, let’s work together to provide an incident-free future for your product and keep it secure and reliable for both you and your customers!
Conclusion
Every year, cybersecurity threats become more frequent, severe, and costly. The emergence of advanced technologies like AI and the lack of cybersecurity talent promises to fuel the need for strong cybersecurity strategies and new approaches to software development.
By prioritizing security during development and implementing holistic strategies like zero trust and digital immune systems, you can significantly increase your product’s security and prepare your business for new cybersecurity challenges.
At Apriorit, we always keep a close eye on the latest changes in cybersecurity to outpace hackers and give our clients the best protection. Our team of experts can help you build a comprehensive strategy that relies on the latest trends in cybersecurity.
Need a reliable team of cybersecurity experts?
Apriorit can provide you with top software engineering and quality assurance talents to tackle any cybersecurity task and safeguard your product!



