Data is the new gold and diamonds. Hackers no longer wait for the perfect chance to come by it. Instead, they persistently plan, prepare, and execute complex targeted attacks, depriving businesses of valuable data.
Extended detection and response (XDR) offers a way to secure business data from advanced threats. XDR security solutions are designed to streamline incident response, equipping security teams with innovative threat detection technologies to improve and accelerate response workflows. However, most off-the-shelf XDR platforms only cover common tasks, forcing organizations with unique security needs to look for customizable options.
In this article, we take a close look at the nature of XDR platforms, discussing the benefits of XDR, comparing different types of platforms, and analyzing common architectures and feature sets. We also outline what to pay attention to if you decide to build or customize such a platform. This article will be helpful for technical leaders evaluating various implementation options and considering the creation of a custom XDR solution.
How to enhance business data security with XDR
Business data resides across multiple endpoints and flows over endless channels, creating a security landscape so large and complex that traditional tools can no longer protect it.
With no centralized place to monitor, analyze, and manage the security of their data, businesses often feel left in the dark in the face of advanced threats and complex cybersecurity attacks. The recent need to urgently shift to remote work only highlighted the importance and value of having such a centralized point of data visibility and management.
In response to this need, security professionals came up with a new concept: extended detection and response.
What is an XDR platform?
While there’s no unified definition of an XDR platform yet, popular definitions suggested by Nir Zuk, the creator of the concept, and Microsoft might be summarized as follows:
An XDR platform is a solution that provides a unified point for collecting security data from various sources, enabling contextual data analysis, advanced threat detection, and effective response.
The concept of an XDR security platform can be seen as the next step in the evolution of its predecessors:
- Endpoint Detection and Response (EDR)
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation, and Response (SOAR)
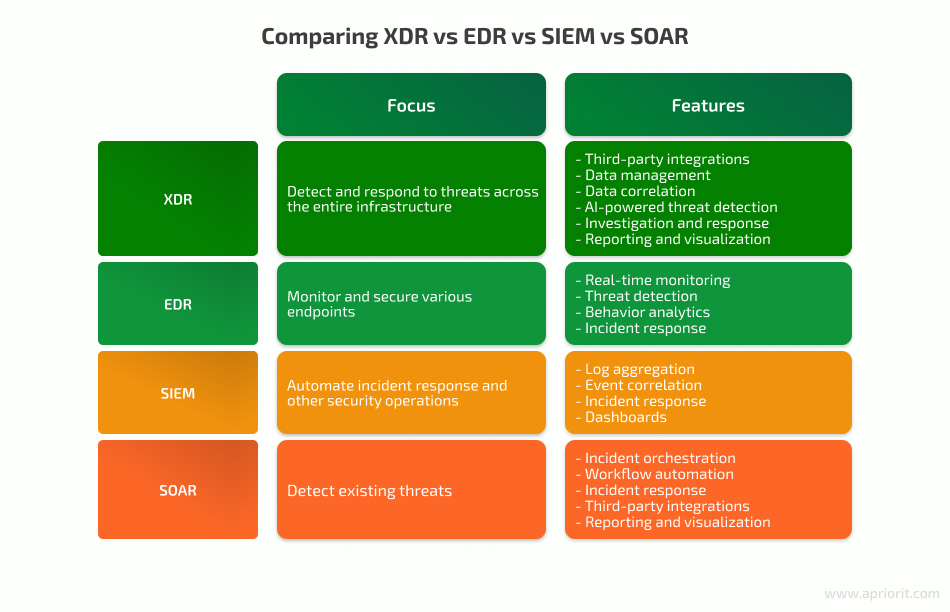
An XDR system is supposed to effectively integrate with its predecessors, including not only advanced EDR, SIEM, and SOAR systems but also more common tools like firewalls and antivirus software. Leveraging all these tools and systems as data and functionality sources, XDR enables security teams to finally overcome the limitations and cybersecurity problems they used to deal with in the past, which we cover in the next section.
Build a next-gen threat detection system
Reach out to our cybersecurity experts and build a customizable XDR solution for your business or customers.
How can your business benefit from using an XDR platform?
While the feature sets of XDR solutions might differ, their goal stays the same — to help security experts address common limitations of traditional cybersecurity tools:
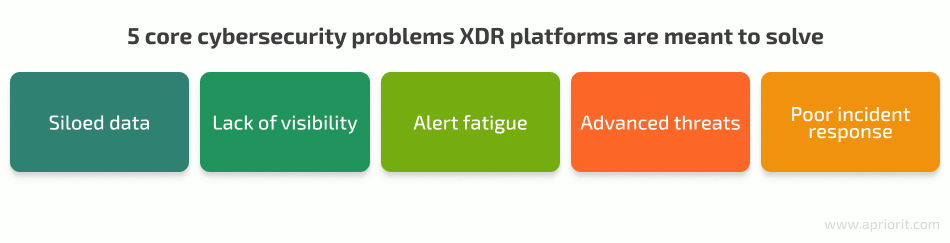
- Siloed data coming from different security tools and services. Such data reduces the efficiency of threat detection and incident response, as security specialists have to manually correlate data from different sources to see the full picture of an incident. XDR platforms can help simplify data management by aggregating data from different systems, services, and tools in a single place.
- Lack of visibility across multiple security layers. Tons of security data comes from different IT environments: endpoints, networks, and clouds. With traditional cybersecurity tools, it’s difficult to compose a large, unified picture out of all that data. For example, with an EDR, you might see the entry point used by attackers but have limited information on the further distribution of the attack and the users and systems affected by it. An XDR solution expands visibility across the entire IT infrastructure, enabling security specialists to correlate threat indicators coming from different sources and get the full context of each incident.
- Alert fatigue caused by the enormous number of false positives. This creates unnecessary overhead for security teams and increases the risk of inefficiently handling incidents and threats that pose a real danger. XDR platforms can reduce the number of alerts sent to your security team by unifying data gathered from different sources, applying advanced alerting rules, and improving overall workflow automation.
- Advanced threats coming from multiple attack vectors and attacks executed using advanced technologies like machine learning (ML) and artificial intelligence (AI). Such threats are difficult to detect for traditional security solutions. By applying advanced analytics techniques, machine learning, and AI mechanisms to correlate and process gathered data, XDR tools make it easier to detect and respond to such threats.
- Poor incident response mostly based on manual operations is prone to human errors and escalates threats by increasing the average response time. With XDR, you get access to improved threat analysis and granular automation of response operations, increasing your security team’s effectiveness.
The usual workflow of detecting a threat and mitigating it with the help of an XDR platform consists of three major stages:
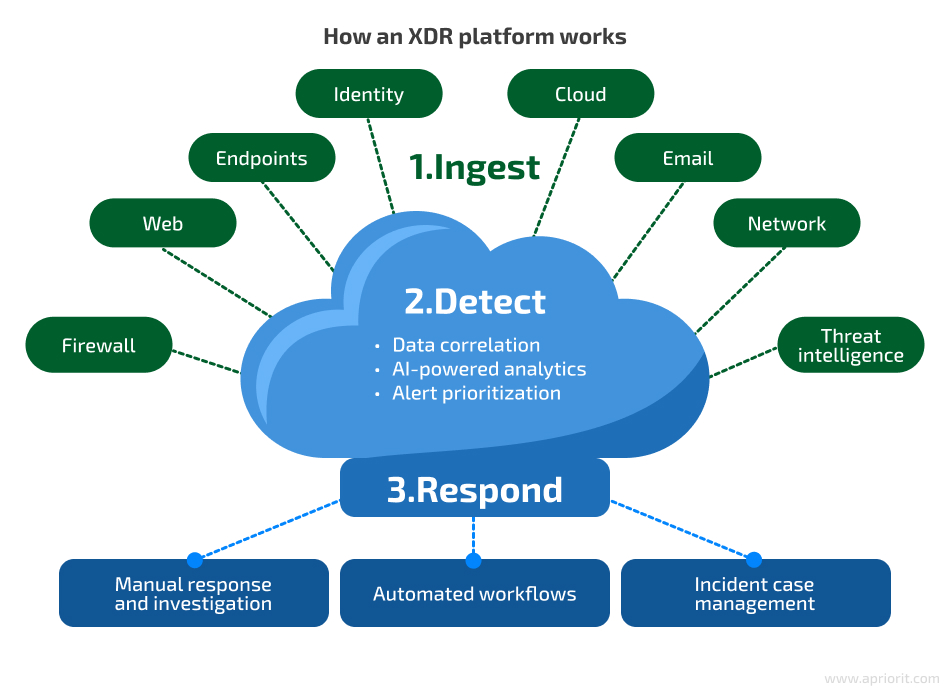
1. Ingest — Collect data from different sources: endpoints, cloud environments, network traffic, etc.
2. Detect — Correlate and analyze gathered data using advanced ML algorithms and AI models.
3. Respond — Orchestrate an automated response to detected threats according to their priority and gather contextual data necessary for manual investigation.
While the concept of XDR security is relatively new, businesses are already faced with multiple XDR platforms to choose from. In the following sections, we discuss what you should pay attention to when looking for an XDR platform that suits your business needs and how to determine if building a custom one will benefit you.
Read also
Implementing Artificial Intelligence and Machine Learning in Cybersecurity Solutions
Leverage the power of AI and ML for your cybersecurity solution. Discover the benefits, limitations, and use cases of these cutting-edge technologies.
Criteria to rely on when choosing the right XDR solution
When deciding which off-the-shelf XDR product to use for your organization’s cybersecurity, pay attention to the following three main criteria:
- Required features — While accomplishing the same high-level tasks, ready XDR security tools offer different feature sets. Some may have stronger AI modules, while others offer sophisticated data protection mechanisms. Consider your individual requirements when making the final choice.
- Configuration flexibility — The more flexibility you want to have within an XDR system, the harder it may be to find the right fit. Yet flexibility is crucial when it comes to configuring data aggregation, incident response scenarios, or reports. Determine in advance what features you want to be highly customizable.
- Ease of management — Being a complex solution, an XDR platform can be difficult to orchestrate and manage. Depending on the type of platform (more on that later), you might need to put extra effort into configuring and maintaining it.
Going over these criteria will help you determine your core requirements for an XDR system and, therefore, find your own perfect fit.
Another important detail to consider when evaluating ready XDR solutions is the type of platform. Currently, you may encounter two common types of XDR solutions:
1. Native XDR platforms integrate security tools and solutions from a single vendor. Among the key benefits of such platforms are minimized compatibility and integration issues. At the same time, these platforms are the most prone to vendor lock-in and, therefore, the least flexible. You won’t have many options for expanding your platform’s functionality with third-party tools.
Common examples of native XDRs include Microsoft 365 Defender, Cisco XDR, and Palo Alto Networks Cortex XDR.
2. Open XDR platforms aren’t limited to the products and services of a single vendor. While still offering centralized platform management capabilities, they rely on third-party tools and services of different vendors. Such platforms tend to be more flexible compared to their native counterparts yet still pose the risk of vendor lock-in, as you rarely get to choose the providers of core functionalities.
According to Gartner, open XDRs include Splunk, LogRhythm, and QRadar.
Some XDR vendors deliver their solutions in the form of a managed service. Similarly to cloud service providers, managed detection and response (MDR) vendors take it upon themselves to help businesses configure and orchestrate their cybersecurity resources. However, just like with regular cloud services, default MDR services are subscription-based, which may not be the best financial solution for some businesses. They also offer limited scalability and flexibility and don’t always meet the unique requirements of heavily regulated industries like healthcare or finance.
According to Gartner, the list of vendors offering MDR services includes Sophos, ReliaQuest, and Arctic Wolf.
If no existing solution fully meets your requirements, you can consider possible customization options — more on that in the next section.
Read also
Starting a New AI Project: 12 Questions to Assess If You’re Ready
Become confident in your AI journey. Learn how to assess your need for AI, prepare for its adoption, and ensure your AI project is sustainable and profitable in the long run.
How to get a customized XDR solution
Off-the-shelf XDR platforms can be a decent option for many organizations, but they may not be able to provide the exact level of flexibility or integration you need. Therefore, you might want to evaluate other options.
Currently, there are three ways you can try enabling XDR capabilities that are relevant to your business:
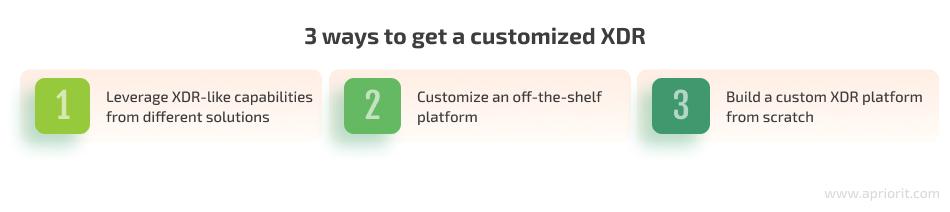
1. Leverage XDR-like capabilities from different solutions — The concept of extended detection and response is based on combining features and using data from different security tools. You may try getting the same results without deploying a dedicated XDR solution.
On the bright side, you get to choose exactly the solutions you want to use. The key challenge is that the more diverse the collection of tools, the more complex their management and configuration. A dedicated XDR platform provides a centralized point of data management and incident response, reducing overall administrative overhead. Without such a platform, it will be almost impossible to ensure the same level of user experience and data protection.
2. Customize an off-the-shelf platform — If there’s a ready solution that mostly works for you and only requires slight improvements, you may consider tailoring it to your specific needs. For example, if you have a custom security system or a specific data source you want to integrate with an XDR solution, you might need help with building special connectors or implementing custom APIs.
However, keep in mind that you’ll need to not only implement a custom improvement but also support the new feature or functionality over time, which on its own can be a source of extra challenges.
3. Build a custom XDR platform from scratch — Whether your organization operates in a unique niche with specific requirements or you want to become a vendor of managed XDR services yourself, building a custom XDR can be the right solution.
On the bright side, developing a custom XDR platform enables you to create a solution that 100% reflects your vision and meets all your needs, from the feature set and security to user experience and design.
Potential downsides include crucial factors like high costs, a long development process, and, most importantly, the need for niche development expertise. Consulting an expert business analyst can help you overcome these downsides and outline the optimal course of action for your project.
For 20+ years, Apriorit has been helping tech companies build secure and reliable solutions perfectly tailored to their needs. Want to know if building a custom XDR platform is the right choice for your business? Get in touch with Apriorit specialists to discuss your personal XDR development or customization strategy.
What is the basic architecture of an efficient XDR platform?
Whether you want to create a custom XDR solution from scratch or try leveraging XDR-like capabilities offered by existing services and tools, it’s important to understand what features to focus on first.
When it comes to the capabilities of an XDR platform, Microsoft cybersecurity experts highlight three core functions that we already mentioned:
- Ingest — Collect data
- Detect — Analyze collected data
- Respond — Manage incidents
But if we look closer at the way existing platforms really operate, the number of core functions doubles:
- Integration with the existing cybersecurity ecosystem
- Data management
- Data correlation
- Threat detection
- Investigation and response
- Reporting and visualization
Each of these functions has at least one corresponding component within an XDR platform, forming the platform’s basic architecture:
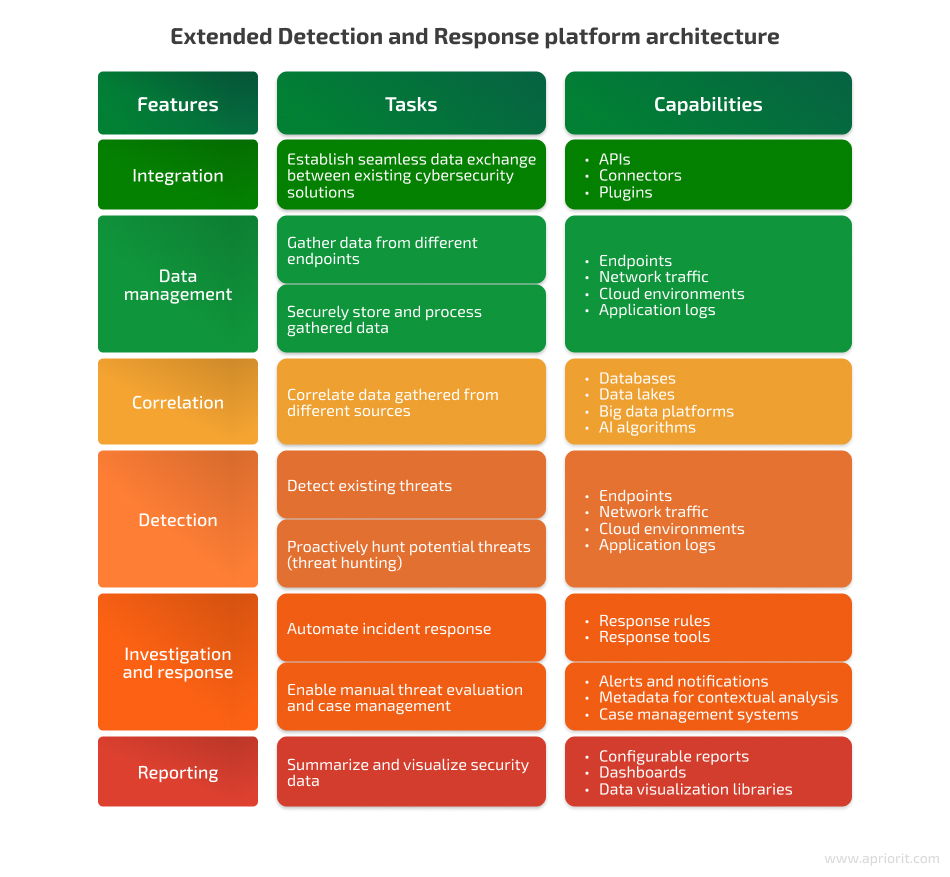
Let’s take a closer look at each of the key features.
1. Integration with the existing cybersecurity ecosystem — Successful implementation of an XDR platform requires it to be deeply integrated with an organization’s existing cybersecurity tools and services. In this way, platform users can greatly benefit from the tools they’re used to working with while powering them up with XDR capabilities.
Making your platform easy to integrate with solutions like antivirus software, firewalls, SIEM, and SOAR systems will help you:
- Save resources of security teams working with the platform by automating repetitive tasks and processes
- Enhance threat detection by gathering data from different security tools and systems in a single place
- Simplify security data analysis by automating data correlation and visualization, allowing security specialists to focus on complex tasks that require human expertise
On the technical side, your development team can implement third-party integrations in different ways: with APIs, special connectors, or plugins. The choice of integration approach will depend on the specific solutions and services you want your platform to work with.
2. Data management — To provide comprehensive visibility into an organization’s security landscape and enable efficient threat detection and response, an XDR system requires tons of data. That data should be gathered, processed, and stored in a secure and efficient manner. Therefore, a significant part of your development team’s efforts will go to establishing efficient and secure data management mechanisms within your XDR system.
As XDR platforms are continually working with application logs and databases, your team will need to rely on technologies that enable:
- The creation of scalable data lakes and data warehouses
- Indexing of both structured and unstructured data
- Rapid data retrieval for security analysis and correlation
Only then can you ensure that your security experts can efficiently analyze incidents, make proactive data-driven decisions, and maintain the needed security posture.
3. Data correlation — In order to get actionable results from data analysis, an XDR solution needs to be able to precisely correlate data received from different sources. This involves combining, comparing, and deeply analyzing security data received from both internal and external sources, logs, endpoints, networks, and cloud environments to threat intelligence feeds.
Quality data correlation brings several meaningful benefits:
- Increased accuracy of threat detection
- Reduced number of false positives in automated incident response
- Enriched context for incident investigation
- Efficient detection of advanced threats
- Threat intelligence and proactive threat hunting
4. Threat detection — Locating and handling cybersecurity threats is one of the key tasks of an XDR platform. In contrast to traditional cybersecurity solutions, XDRs rely on sophisticated solutions like machine learning algorithms and AI-powered behavior analysis. They analyze data coming from different sources and look for advanced, non-obvious indicators of potential attacks or incidents.
To increase the effectiveness of threat detection, it’s important to integrate the XDR system with advanced data on new threats and threat indicators. One possible source of such information is threat intelligence feeds. Using these feeds, you can ensure that your XDR platform can both:
- Reactively detect and respond to existing security threats, looking for malware signatures and other indicators of known attacks
- Proactively hunt for potential zero-day vulnerabilities and advanced new threats that try to evade detection, looking for traits of malicious behavior
Quality implementation of threat detection capabilities is vital for ensuring efficient performance of the next XDR feature we’re going to talk about.
Read also
The 6 Most Common Security Issues in API Development and How to Fix Them
Protect the sensitive data flowing through your APIs. Learn the common API threats and discover how to make your APIs immune to hacker attacks in our expert guide.
5. Investigation and response — Enabling security teams to efficiently respond to and investigate cybersecurity incidents is one of the key purposes of XDR tools. To make your XDR solution truly efficient, it’s important to implement the necessary means for both automated and manual incident response.
For events that have clear determiners, such as three sequential unsuccessful login attempts, automated response scenarios should be implemented. The response will vary depending on the incident and the context, ranging from additional user identity verification to permanent blocking of the user or process.
Automated incident response provides two important benefits:
- Reduces the response time, minimizing an incident’s potential impact
- Lowers the security team’s overhead, freeing up expert resources for cases that require manual evaluation and investigation
However, not all incidents can be dealt with automatically. In some cases, it’s important to get a human expert’s evaluation before taking further action. To enable granular configuration of such scenarios, it’s important to implement a flexible alerting system with a rich set of customization capabilities.
6. Reporting and visualization — To make your XDR platform a tool that’s truly helpful for security teams, it’s important to include robust data visualization and reporting features. Think about capabilities like default metrics for data analysis, report templates, and customizable dashboards. You may also want to incorporate special data visualization libraries and frameworks like D3.js, Plotly, or Tableau to enable the creation of custom data visualizations and charts within your XDR system.
For security experts, this feature will be a source of systematized information on the current state of the infrastructure. Using the results of multi-level data analysis, security experts can:
- Evaluate the organization’s overall security posture
- Determine areas for further optimization and improvements
- Get prepared for passing internal assessments and external compliance audits
Gathering and summarizing key takeaways from the analyzed data into well-structured, informative reports and then turning them into easy-to-analyze visuals, an XDR platform also makes it easier for company management and stakeholders to make informed, data-driven decisions on the organization’s security.
But to ensure ultimate data security with XDR, your development team needs to plan for not only building core features but also mitigating possible risks. You can read about what factors to focus on first in the next section.
How to address common risks of building a custom XDR platform
Aside from choosing the feature and functionality sets that best suit your case, there are several risks your development team should pay special attention to when working on an XDR platform:
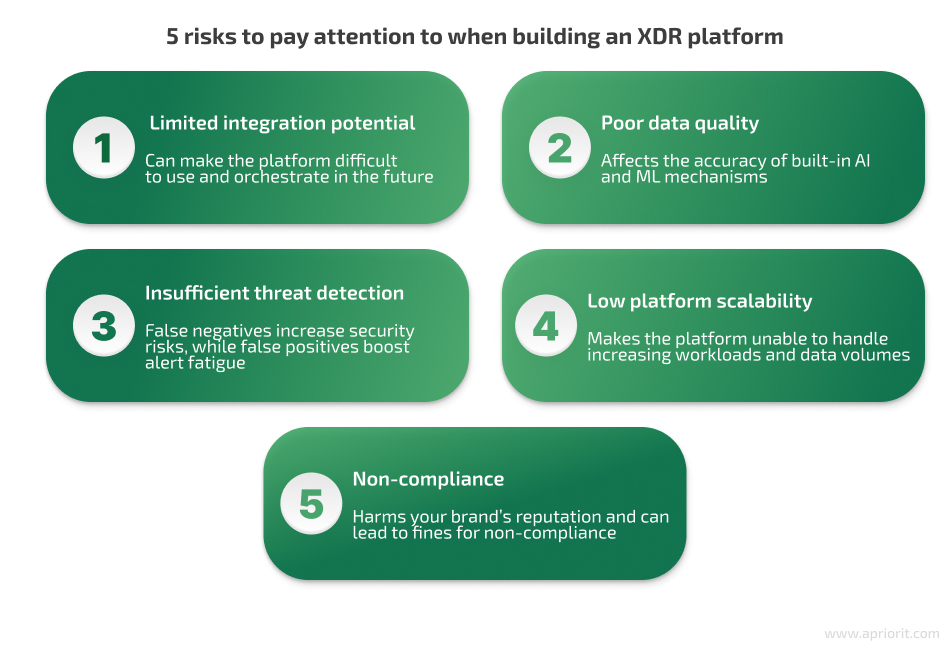
1. Limited integration potential — The more third-party tools and services you want your platform to be compatible with, the greater the complexity of the development process. Issues like the inability to handle different data formats or limited support for API integrations can compromise your platform’s overall performance and data processing capabilities and even lead to vendor lock-in. Also, without seamless integration with security tools and systems, it will be difficult to effectively orchestrate your platform.
How to address this risk: Design and build your platform with integration possibilities in mind. Enable support for open APIs to reduce the risk of vendor lock-in and make your platform easy to integrate with. Make sure to securely integrate all needed APIs and run thorough API testing along the way. If needed, consider building custom APIs to expand the capabilities of your XDR platform.
If needed, you can also plan for migrating data from your legacy systems and security services to ensure the continuity of historical data within your solution.
Related project
Supporting and Improving Legacy Data Management Software
Discover how Apriorit specialists improved user satisfaction with our client’s legacy system by improving its supportability and preparing it for a migration to a new platform.
2. Poor data quality — ML algorithms and AI-powered systems are the core of any efficient XDR platform. They are responsible for gathering separate threat indicators from different sources, correlating them, and recreating the full picture of a potential threat or attack. And data is the main weakness of any AI system. Without quality data, your AI models can produce inaccurate results, making threat detection and response more challenging instead of simplifying it.
How to address this risk: Choose data sources most relevant to your specific use case. Look for internal data that can be fed to AI models and hire an expert team of AI professionals who can properly clean and annotate your data, build an efficient model, and train it to perfection.
3. Insufficient threat detection — A platform that generates too many false positives or false negatives worsens the organization’s cybersecurity posture and causes alert fatigue for security teams. The main reasons for inefficient performance of an XDR platform include the use of low-quality data and inefficient ML and AI algorithms, lack of configuration flexibility, and overreliance on outdated, signature-based threat detection mechanisms.
How to address this risk: Along with paying attention to the quality of your data and AI solutions, make sure to use relevant threat intelligence feeds and incorporate next-gen threat detection mechanisms into your platform. Also, plan for advanced customizability of security rules and alerts within your platform early on.
4. Low platform scalability — As the platform grows, it will need to handle larger data volumes and serve larger numbers of users. If sudden spikes in workloads and an increase in users weren’t accounted for at the design stage, your initially effective platform can become insufficient and difficult to work with.
How to address this risk: Plan for your platform’s future growth early on by designing a distributed platform architecture using advanced data storage and retrieval mechanisms and dedicating extra effort to efficient orchestration and automation of your cloud-based operations.
5. Non-compliance — Depending on your industry and region, you might need to comply with varying requirements. For most organizations processing personal data, compliance with the GDPR is a must. Organizations handling cardholder data must comply with PCI DSS, while healthcare service providers are required to comply with HIPAA. Failing to meet applicable requirements can cause significant reputational damage and lead to extensive fines for non-compliance.
How to address this risk: Determine the compliance requirements you must or want to comply with and account for key measures and features to ensure compliance when designing and building your platform. Run corresponding tests and compliance audits as your platform comes to life.
Read also
How We Scaled API Performance in a High-Load System and Avoided CPU Overload
Keep your system running even during the high load. Learn how to scale your API performance so your system can handle increased load without shutting down.

Conclusion
To efficiently mitigate emerging cybersecurity threats, businesses need to deploy advanced, sophisticated security solutions such as XDR. However, if your business has specific requirements regarding the platform’s flexibility, scalability, security, and compliance, solutions available on the market might not be the perfect fit.
Whether you want a custom-made XDR platform perfectly tailored to your needs or an improvement to your existing cybersecurity system, Apriorit specialists will make it happen. With over 20+ years of experience delivering secure and reliable solutions, we can help you design, develop, test, and maintain software solutions of any complexity.
Need a team of cybersecurity experts?
Contact us to leverage our 20+ years of experience in delivering bullet-proof cybersecurity solutions!




