Expanding your cybersecurity product is not just an option; it’s a strategic necessity. But how can you choose what functionality to add to your existing product to respond to ever-changing market trends and customer demands?
The cybersecurity market offers different types of solutions for you can choose when building your own product.
In this article, we explore the six most common development vectors for enhancing your cybersecurity solution — XDR, EDR, SIEM, IRM, SOAR, and DLP. We unpack the strengths of each type of cybersecurity platform so you can make an informed decision about which will work best for your product’s growth.
This article will be useful for tech leaders who want to enhance their existing cybersecurity solutions both for internal enterprise use and for their end users and who are considering different scenarios for further product growth.
Why invest in expanding your cybersecurity solution?
One of the main challenges for cybersecurity solutions is that end users face a wide range of new cybersecurity threats, from data breaches and malware attacks to ransomware and phishing scams. As a result, cybersecurity needs are constantly growing, forcing users to consider more sophisticated cybersecurity solutions.
Basic cybersecurity solutions usually address one or two major cybersecurity needs, which might include:
- Endpoint protection
- Vulnerability management
- Network security
- Access control
However, as the threat landscape changes and market demands evolve, a basic solution can no longer provide sufficient protection for your customers. Siloed security solutions simply can’t keep up with emerging threats and stay in tune with the latest cybersecurity trends.
One way to address this issue is to build several solutions that target different threat vectors. However, implementing a patchwork of individual solutions creates management headaches and integration challenges. These disparate systems often lack a central view of your security posture, leaving gaps in your defenses and creating blind spots for attackers to exploit.
Another approach is to expand your existing cybersecurity product to the level of a sophisticated platform that covers the needs of your end users and is easy to deploy and manage.
By growing your product into a full-scale cybersecurity platform, you can build a more robust, cohesive, and adaptive solution that’s ready to face:
- Evolving market demands. Customers are increasingly demanding comprehensive security solutions that address their specific needs. Businesses that fail to adapt their offerings to meet these demands risk losing ground in the competitive marketplace. With an advanced cybersecurity platform, you can integrate specific security tools or features that cater to the evolving needs of your end users.
- Rise of new cyber threats. Expanding your cybersecurity platform allows you to integrate new technologies and functionalities specifically designed to address the latest vulnerabilities and harden data protection against zero-day attacks.
- Need for automation. Many cybersecurity processes, such as incident response and log analysis, are time-consuming and resource-intensive. By offering to automate these processes, you can provide your platform’s users with benefits like reduced reliance on manual intervention, minimized human errors, and improved efficiency.
With these options in mind, let’s take a look at some popular types of cybersecurity platforms that you can use as a reference for expanding your product.
Ready to transform your cybersecurity product?
Leverage our expertise to build a robust and secure platform that meets all of your customer’s expectations.
Top 6 types of cybersecurity platforms
By incorporating additional features into your existing product, you can enable it to address a broader range of security tasks. But instead of chaotically adding new features, consider choosing a specific cybersecurity platform as a guideline for growing your product. Below, we explore six types of cybersecurity platforms that rule today’s cybersecurity market:
Each type offers unique strengths and caters to specific security needs. Let’s see what development vectors will best align with your product’s vision.
1. XDR: Extended detection and response platforms
What is XDR?
Extended detection and response (XDR) is an advanced type of cybersecurity solution that is designed to provide comprehensive threat detection and response across an organization’s entire digital environment. Such a platform often heavily relies on artificial intelligence. Unlike traditional security tools that focus on protecting certain parts of IT infrastructure, XDR integrates multiple security products into a cohesive system, enabling a unified approach to threat detection, investigation, and response across the whole infrastructure.
If you want to turn your cybersecurity product into an XDR platform, pay attention to its architecture. Your development team will need to design and build a thoroughly planned architecture that allows for ingesting, analyzing, and correlating security data from many sources.
Here’s a breakdown of the key features of an XDR platform:
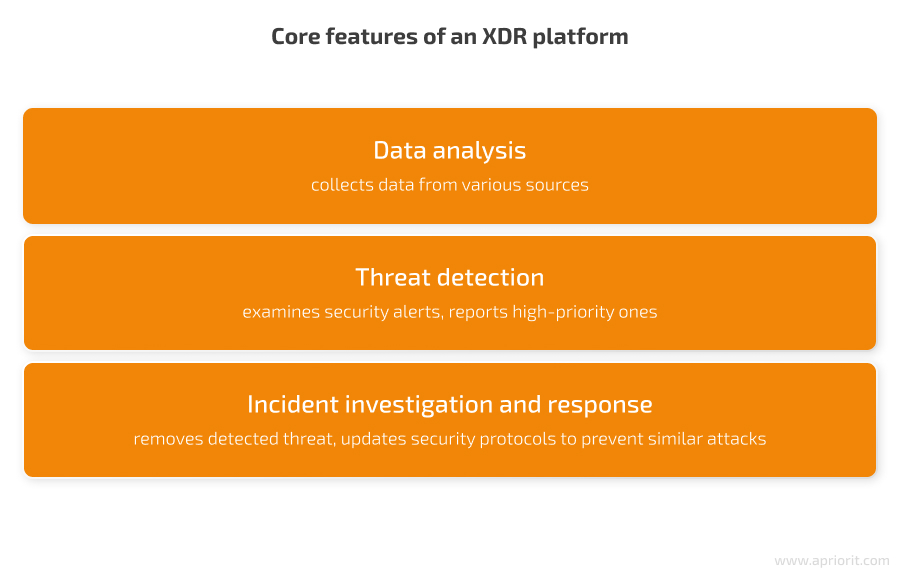
A typical XDR solution offers a lot of capabilities for an organization’s security operations, including:
- Real-time threat sharing across various tools for coordinated blocking
- Amplified signals for clearer threat detection
- Automated alert validation to reduce false positives
- Faster incident response with alerts that include only relevant data
- Simplified setup with a central hub for managing all configurations
As a result, an XDR platform can give you an edge in the market:

- Enhanced threat detection. XDR analyzes data across all security tools, giving a holistic view of users’ activity. This allows for much faster identification of sophisticated attacks like zero-day exploits and lateral movement.
- Improved incident response. When a security incident occurs, every second counts. XDR provides a unified view of all security events, giving a clear picture of the attack’s scope. This allows for swift prioritization of actions and decisive measures to contain the damage, minimizing potential losses.
- Reduced alert fatigue. By correlating events and prioritizing threats, XDR reduces alert fatigue, shortening the time needed for investigating false positives.
- Streamlined security operations. XDR automates many routine security tasks such as log collection and initial analysis, helping organizations free up resources for higher-level investigations and proactive threat hunting.
XDR’s effectiveness lies not just in its features but also in its practical application. Let’s explore how XDR capabilities can be leveraged in practice:
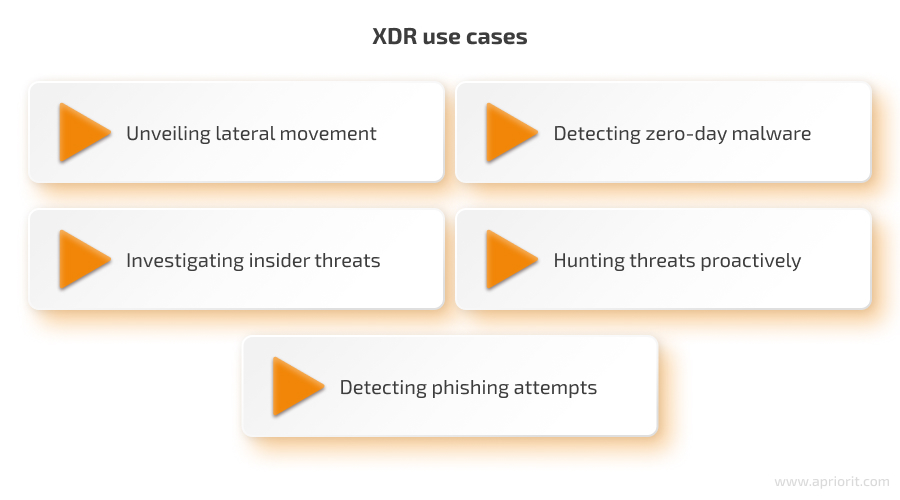
- Unveiling lateral movement. An attacker’s tactic is to move laterally after intrusion to access sensitive data on a server while remaining unnoticed. By correlating suspicious activity on a potentially compromised device with unusual network traffic patterns, an XDR platform can detect this type of attack. Upon detection, the platform can trigger an alert, allowing a security team to isolate the threat and prevent further damage.
- Detecting zero-day malware. Traditional signature-based detection solutions might miss a new strain of malware infecting a user’s endpoint. In contrast, XDR analyzes current endpoint behavior and identifies deviations from typical behavior. This anomaly detection capability allows for identifying previously unknown malware and taking quick action to contain an outbreak.
- Investigating insider threats. Unusual user activity, such as accessing unauthorized data or downloading large files at odd hours, might indicate an insider threat. XDR platforms can correlate user activity with other security events, such as failed login attempts from unusual locations.
- Hunting threats proactively with UEBA. Security teams can leverage XDR’s user and entity behavior analytics (UEBA) capabilities to hunt for potential threats proactively. By analyzing patterns in user behavior and entity activity with AI, XDR solutions can identify suspicious events that might indicate compromised accounts or impending attacks.
- Detecting phishing attempts. Phishing attacks are a common entry point for cyber threats. XDR solutions can analyze email content, user behavior, and network traffic to identify phishing attempts.
With an XDR solution, an organization’s security team transforms from reactive responders to proactive protectors. XDR gives security teams the tools and insights needed to stay ahead of cyber threats and safeguard the organization’s data and systems. If you decide to grow your product into an XDR platform, you’ll be providing your end users with some of the most advanced cybersecurity tools.
Read also
How and Why Should You Build a Custom XDR Security Platform?
Discover how custom XDR solutions can protect your business from sophisticated attacks. Explore our valuable insights into the benefits of XDR and build a tailored solution to meet your unique security needs.

2. EDR: Endpoint detection and response platforms
What is EDR?
An endpoint detection and response (EDR) platform focuses on protecting a specific area of an organization’s IT infrastructure: endpoints, which include laptops, desktops, servers, and mobile devices. EDR solutions rely on endpoint data (including hardware and operating system information) to detect sophisticated threats and ongoing attacks. While some raw data processing happens locally on the endpoint, more complex analysis is handled by machine learning algorithms.
EDR platforms enable organizations to:
- Boost endpoint protection against targeted threats
- Detect and respond to threats in real time
- Hunt threats proactively
- Minimize attacker dwell time for reduced impact
- Automate tasks for streamlined security operations
The feature core of an EDR platform is somewhat close to that of an XDR platform, as these two types of cybersecurity products are related:
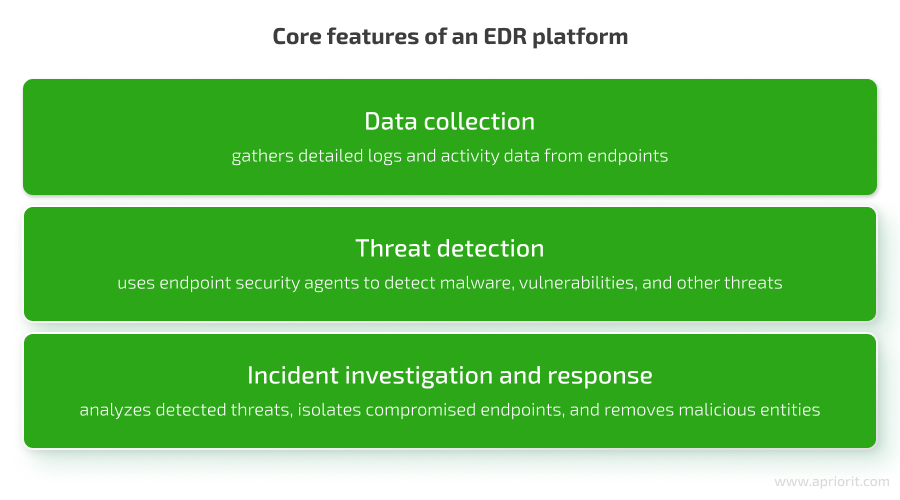
Since EDR platforms act like dedicated security shields, they provide security teams with the visibility needed to uncover incidents that would otherwise remain undetected. Here’s a breakdown of the key advantages of EDR platforms and how their capabilities can enhance your cybersecurity product:
- Continuous endpoint monitoring. EDR solutions continuously monitor endpoint activity, detecting unauthorized access attempts, malware execution, or data exfiltration attempts. This allows for identifying potential threats before they escalate into major incidents.
- Real-time threat detection and response. EDR tools analyze endpoint data in real time, enabling swift identification of and responses to potential threats. As a result, organizations can take immediate action, such as isolating infected devices, blocking malicious traffic, or launching an investigation, minimizing potential damage.
- Improved threat hunting. The advanced analytics capabilities of EDR platforms empower security teams to hunt for malicious actors before they strike. Analytics is also crucial for analyzing user behavior patterns and identifying unusual network activity, potentially uncovering hidden threats lurking within target systems.
- Reduced dwell time for attackers. EDR’s rapid detection and response capabilities are crucial. By identifying and responding to threats quickly, EDR-like solutions can minimize the time for which attackers have access to target systems, significantly reducing the potential damage from an attack.
- Streamlined security operations. EDR tools automate routine endpoint security tasks like initial analysis and basic response actions.
Even though EDR solutions excel in endpoint security, organizations with complex IT environments might benefit more from an XDR’s broader threat detection capabilities that cover the entire network infrastructure. Let’s see what tasks EDR-like solutions are most suitable for:
- Detecting malware infections. EDR solutions constantly monitor endpoint activity, which allows for the detection of malware infections and even previously unknown strains. EDR tools can identify suspicious file behavior, network connections, and resource usage patterns, alerting security officers to take immediate action, such as quarantining infected devices or blocking malicious processes.
- Investigating endpoint attacks. If an attack has already happened, EDR systems collect incident-related data from the compromised endpoint, including system logs, file changes, and network activity. With this data, an organization’s security team can reconstruct the attack timeline, identify the attack vector, and determine the scope of the breach, allowing for a targeted response.
- Obstructing lateral movement. Attackers often try to breach a single device and then move laterally across your network to access sensitive data. EDR solutions can help prevent such attacks by identifying suspicious network connections initiated from the compromised device and alerting security teams.
- Protecting against ransomware. EDR solutions monitor endpoint activity for unusual file encryption behavior, identifying potential ransomware attacks at early stages.
With EDR, a security team can change their cybersecurity approach to be more active in protecting the organization’s critical data and systems against cyber threats.
Read also
Remote Browser Isolation — The Next Step in Endpoint Security?
Explore how remote browser isolation (RBI) can enhance endpoint security and shield your remote employees from sophisticated browser-based attacks. We discuss the features and challenges of RBI so you can make an informed decision about improving your cybersecurity measures.

3. SIEM: Security information and event management platforms
What is SIEM?
Security information and event management (SIEM) is a cybersecurity technology that provides real-time analysis of security alerts generated by applications and network hardware. SIEM systems combine security information management and security event management to offer comprehensive security monitoring and incident response capabilities.
Since SIEM solutions collect and analyze data from various sources, organizations can leverage them to detect, investigate, and respond to security threats effectively. Here’s why SIEM features can become a valuable addition to a sophisticated cybersecurity platform.
- Improved cybersecurity visibility. SIEM grants visibility across an entire IT infrastructure, regardless of the organization’s size. This allows security teams to monitor for threats and maintain a strong security posture more effectively.
- Streamlined security operations. SIEM automates routine tasks like log collection and initial event correlation.
- Enhanced threat detection. By correlating data from diverse sources, SIEM tools allow for identifying complex threats that might go unnoticed by other security tools. This allows for faster detection and response to sophisticated attacks.
- Reduced alert fatigue. Security teams are often overloaded with alerts. SIEM helps by correlating events and prioritizing threats based on severity and context. As a result, security officers can focus on the most critical issues depending on their priority.
- Actionable security insights. SIEM platforms provide comprehensive security reports, offering valuable insights into trends, user activity, and the overall security posture. This data helps security specialists make informed decisions and prioritize security initiatives.
- Simplified compliance management. Many security regulations mandate organizations to maintain detailed security logs. SIEM solutions facilitate compliance by providing a centralized repository for security data that can be easily exported for reporting purposes.
SIEM might not be ideal for businesses whose primary focus is endpoint security. While you can integrate SIEM with EDR or XDR, it doesn’t offer the same level of deep endpoint visibility and investigation capabilities on its own. However, there are several use cases where SIEM can really shine. You can choose to grow your product into a custom SIEM-based platform when you aim to:
- Provide a centralized view of security data across an entire IT infrastructure, including firewalls, intrusion detection systems, and endpoint security solutions
- Improve threat detection by correlating events from various security tools
- Streamline security operations by automating tasks like log collection and initial event correlation
- Maintain detailed security logs for your end users to be able to prove adherence to regulations, laws, and standards such as the GDPR, HIPAA, and PCI-DSS
A SIEM platform isn’t a simple log collector; it’s a powerful tool widely used by businesses of all sizes to gain a holistic view of their security posture.
Related project
Improving a SaaS Cybersecurity Platform with Competitive Features and Quality Maintenance
Learn how you can elevate a SaaS-based cybersecurity platform to meet the highest industry standards with our assistance. We helped our client implement new features, fix bugs, and improve their platform’s UI/UX, resulting in increased stability and competitiveness.

4. IRM: Insider risk management platforms
What is IRM?
Insider risk management (IRM) is a cybersecurity strategy focused on identifying, assessing, and mitigating risks from insiders such as employees, contractors, or business partners. These risks can come from malicious or unintentional actions that compromise security. Unlike external threats, insider risks require specialized approaches to detection and management as they originate from within the organization.
IRM platforms go beyond simply monitoring insider activity. They use a multi-layered approach to minimize insider risks.
- User behavior analytics (UBA) leverages AI capabilities to track user behavior patterns, including file access, data downloads, and application use. Deviations from normal activity might indicate suspicious user behavior that needs to be addressed by security specialists.
- Data loss prevention (DLP) features monitor and control the transfer of sensitive data, helping to prevent accidental or intentional data exfiltration attempts by insiders.
- Risk scoring and assessment functionality assigns risk scores to users based on their behavior, access levels, and other contextual factors, helping prioritize responses to potential threats.
Insider threats can be devastating, causing financial losses, reputational damage, and data breaches. Cybersecurity platforms that have been enhanced with IRM features can:
- Address internal threats that originate from within the organization
- Protect sensitive information, such as proprietary data and intellectual property, from being leaked or misused
- Combine other security measures that focus on outside threats for even better protection
Enhancing your cybersecurity product with IRM capabilities can bring significant benefits:

- Reduced risk of insider incidents. IRM helps prevent insider-related incidents by identifying unusual activity patterns and potential threats. This proactive approach minimizes the risk of data breaches and other security incidents caused by insiders, protecting critical business assets.
- Mitigation of data breaches. Data breaches can result in hefty fines, penalties for regulatory non-compliance, and a significant loss of customer trust. IRM helps mitigate these risks by monitoring users’ access to sensitive data and flagging suspicious activity.
- Improved employee monitoring. Keeping an eye on employee activity might sound intrusive. But with IRM, the focus is on the security of employees who might fall victim to phishing attempts or accidentally leak sensitive data — not micromanaging workers.
IRM can be applied to various scenarios to mitigate insider risks:
- Monitoring privileged users. Privileged users with unrestricted access to sensitive data can pose a significant threat if their accounts are compromised or misused. IRM solutions can monitor the activity of admins and other privileged users, flagging suspicious events like failed access attempts or unusual data transfers.
- Preventing data exfiltration. Data exfiltration, whether intentional or accidental, can lead to the loss of proprietary information, customer data, and other sensitive materials, causing financial and reputational damage. IRM systems use data loss prevention techniques to monitor and control the movement of sensitive data. These systems can identify and block attempts to send or transfer critical information outside a company’s network.
- Detecting insider fraud. Insider fraud can take many forms, from embezzlement to manipulating financial records. By monitoring user activity, particularly around financial systems and sensitive data, IRM solutions can help detect unusual patterns or suspicious transactions that might indicate fraudulent behavior.
An IRM platform can help organizations proactively address potential security vulnerabilities from within, safeguarding sensitive data, financial assets, and, ultimately, the organization’s reputation. If your product already has strong access management or user activity monitoring features, consider expanding it to the level of a full-scale IRM platform.
Read also
How to Efficiently Organize and Manage a Distributed Software Development Team
Our client wantedLooking for effective strategies to assemble and manage a distributed software development team? Discover our insights on how to gather top talent, optimize workflows, and ensure timely delivery of quality products.

5. SOAR: Security orchestration, automation, and response platforms
What is SOAR?
Security orchestration, automation, and response (SOAR) is a set of technologies that enable organizations to collect data about security threats from multiple sources and respond to low-level security events without human assistance.
A SOAR platform combines orchestration, automation, and response components to improve the efficiency and effectiveness of security operations.
SOAR solutions are known for their ability to:
- Seamlessly connect and coordinate existing security tools and systems
- Quickly and consistently respond to security incidents using automated playbooks
- Automate data collection and analysis for proactive identification of potential threats
- Consistently apply security policies and procedures across the organization
After adding SOAR functionality to your cybersecurity product, you’ll enable it to provide:
- Rapid incident response. SOAR capabilities allow for creating automated playbooks that define the steps to be taken when a security incident occurs. These playbooks can trigger actions such as isolating affected systems, blocking malicious IP addresses, and notifying relevant personnel, all within seconds. With predefined automated workflows, incident responses are consistent.
- Reduced alert fatigue. SOAR solutions use advanced algorithms to filter and prioritize security alerts. By correlating data from multiple sources and applying threat intelligence, SOAR can distinguish between false positives and genuine threats, allowing the security team or end users to focus on the most critical issues. SOAR also reduces the overall volume of alerts that need to be manually reviewed.
- Enhanced threat intelligence. SOAR solutions collect and correlate data from various security tools, threat intelligence feeds, and external sources. This offers better threat detection capability by feeding high-fidelity threat intelligence into detection tools like SIEM, EDR, and Network Detection Response (NDR). As a result, your team can take proactive measures, such as threat hunting and vulnerability management, based on a more accurate and comprehensive understanding of the threat landscape.
Here are some scenarios where SOAR capabilities prove especially helpful:
- Phishing attack response. When a phishing email is detected, a SOAR platform can automatically isolate the compromised endpoint, quarantine the malicious attachment, and notify your team of the potential threat.
- Vulnerability remediation. SOAR solutions can identify vulnerabilities detected by security scanners and automatically trigger workflows to patch vulnerable systems or isolate them from the network.
- Malware outbreak response. In the event of a malware outbreak, SOAR systems can automatically deploy predefined remediation steps, such as quarantining infected devices, updating antivirus signatures, and initiating a system scan.
With the help of a SOAR platform, a security team gains the opportunity to respond to threats more efficiently. If enhanced orchestration and automated incident response is what you want your product to have, start with turning it into a robust SOAR platform.
Read also
Data Management Based on SQL Server: On-Premises vs Cloud Database
Explore the key differences between on-premises and cloud SQL Server deployments, including cost-efficiency, security, flexibility, and data control. You will be equipped to choose the best data management solution for your unique software needs.

6. DLP: Data loss prevention platforms
What is DLP?
Data loss prevention (DLP) refers to a set of tools and processes designed to prevent the unauthorized sharing, transfer, or loss of sensitive data. DLP solutions monitor data in use, in motion, and at rest, identifying and protecting information according to predefined policies and rules.
DLP platforms use a comprehensive approach to protecting sensitive data throughout its lifecycle, whether the data resides on a company server, is used on an employee laptop, or is transmitted across the network.
While the core concept remains preventing unauthorized data loss, DLP solutions can be categorized based on the type of data they protect:
- Network DLP solutions focus on monitoring data transfers across the user’s network, including email traffic, file downloads, and data uploads. They are ideal for preventing sensitive data from being leaked through external communication channels.
- Endpoint DLP solutions are deployed on individual devices like laptops, desktops, and mobile phones. They monitor data at rest and in use on these devices, preventing unauthorized copying or transfer of sensitive data to external storage devices or cloud services.
- Cloud DLP systems focus on securing data stored in cloud environments and monitoring data transfers between on-premises networks and the cloud.
A cybersecurity platform enhanced with DLP functionality can offer the following benefits:
- Protection of sensitive data. DLP solutions act as a safety net, preventing leaks of sensitive data such as customer information. By monitoring data transfers and identifying sensitive information, DLP tools help safeguard the most valuable assets, reducing the risk of data breaches and unauthorized disclosure.
- Improved regulatory compliance. Many data privacy regulations and laws, such as the GDPR and HIPAA, mandate organizations to implement measures to protect sensitive data. DLP also helps avoid fines and potential legal repercussions associated with non-compliance.
Here are some of the scenarios where DLP solutions are most effective:
- Preventing accidental data leaks via email. DLP solutions can scan outgoing emails and identify sensitive data. They can then take action, such as blocking the email, asking for confirmation, or encrypting information before sending it.
- Protecting sensitive data on removable storage devices. Data loss can also occur through physical means. DLP solutions can be configured to monitor data transfers to removable storage devices like USB drives or external hard drives. For example, DLP tools can monitor and log all data transfers to removable storage devices.
- Safeguarding intellectual property during mergers and acquisitions. A watermarking feature that embeds digital fingerprints into sensitive documents can help track their movement and prevent unauthorized copying during mergers and acquisitions (M&A). DLP systems can also restrict access to sensitive intellectual property to authorized personnel involved in the M&A transaction.
Now that we’ve explored the specifics of the XDR, EDR, SIEM, IRM, SOAR, and DLP platforms, let’s compare them side by side.
Read also
Regular Expressions for Cybersecurity: What Is the Best RegEx Library to Discover Sensitive Data?
Learn how to leverage regular expressions (RegEx) to efficiently process and analyze large volumes of data for improved cybersecurity. Discover the best RegEx libraries that will help you strengthen your product’s security.
XDR vs EDR vs SIEM vs IRM vs SOAR vs DLP: What format to choose?
Each type of platform can bring its own benefits to businesses that work on expanding their cybersecurity products. Let’s see the key takeaways to determine what platform you should invest in.
| Platform | Focus | Data source | Key function | Results |
|---|---|---|---|---|
| XDR | Broad threat detection and response | Various security tools (EDR, SIEM) | Correlate data from multiple sources for faster, more accurate threat detection and response | Unified view of security posture, faster incident response |
| EDR | Endpoint security | Endpoints (laptops, desktops, servers) | Detect and respond to endpoint threats like malware and ransomware | Improved endpoint protection, faster threat isolation |
| SIEM | Security and compliance | Various security tools, network devices, applications | Collect, analyze, and store security data for threat detection, investigation, and compliance reporting | Centralized log management, improved threat visibility, compliance assistance |
| IRM | Mitigating insider threats | User activity data, access controls, insider info | Identify and mitigate risks posed by malicious or negligent insiders | Reduced insider threat risk, improved data security |
| SOAR | Incident response | Security tools, internal workflows | Automate incident response workflows to improve efficiency | Faster incident response, fewer human errors |
| DLP | Data security and compliance | User activity, dataflows | Prevent sensitive data from being exfiltrated from the organization | Sensitive data protection, compliance with data privacy regulations |
No matter which type of cybersecurity platform you choose as a guideline, there are certain risks and concerns that you and your development team will need to address:
- Data overload. Consolidating data from various security tools can create information overload, making it difficult for security analysts to identify and prioritize real threats.
- Integration challenges. Integrating disparate security solutions with varying architectures and data formats can be technically challenging and time-consuming.
- False positives. Each new functionality might contribute to generating false positives, further adding to the workload of security analysts who need to sort through them.
- Skill shortage. Developing and managing a complex security platform may require the specialized skills of a cybersecurity team.
While each security tool offers unique strengths, you can leverage even more benefits when they work together. You can combine different features from each type of platform to create an efficient and outstanding custom product.
Related project
Enhancing the Security and Performance of a Virtual Application Delivery Platform
Discover how Apriorit helped Cameyo improve the performance and security of their platform and attract new users with several extra features.

How can Apriorit help you enhance your cybersecurity platform?
At Apriorit, we provide you with a comprehensive suite of software development and quality assurance services, empowering you to build secure and reliable software solutions.
In particular, we can help you with:
- Building secure products from scratch. Our team collaborates with you from the very beginning, integrating secure coding practices, threat modeling, and secure architecture principles throughout the entire software development lifecycle. This ensures your product is built with security in mind from the get-go.
- Introducing new security features into your existing product. Does your existing software need a security boost? Our developers can seamlessly add new security features to strengthen your product’s defenses, making your product more resilient against cyberattacks and protecting the safety of your end users.
- Uncovering vulnerabilities with security audits and penetration testing. Even the most secure software can have hidden weaknesses. Our QA teams employ industry-standard tools and techniques to simulate real-world attacks, identifying potential vulnerabilities before they can be exploited by malicious actors.
- Enhancing your product’s legacy code. Apriorit provides the expertise needed to update your legacy applications, integrating modern security measures and improving the maintainability of your product.
Together, we can build a secure, scalable, and feature-rich platform that exceeds your and your customers’ expectations.
Conclusion
Depending on your cybersecurity needs and priorities, you can choose to grow your product into an XDR, EDR, SIEM, IRM, SOAR, DLP, or other type of system. You can also combine typical features of several types of cybersecurity solutions, building a unique product that perfectly matches your vision.
However, creating such a layered security platform will require access to specialized skills and extensive expertise. By partnering with Apriorit engineering teams, you can ensure your platform is built to the highest standards, delivering unmatched security and peace of mind.
Transform your product into a powerful cybersecurity platform!
Let Apriorit experts unlock the full potential of your cybersecurity systems, empowering you to deliver unmatched value to your customers.




