Key takeaways:
- MDM software helps manage and control corporate devices, securing both the devices themselves and the data they store and process. MAM solutions only ensure the safety and security of specific apps (and the data they handle) on enrolled devices.
- MDM products work best for company-owned devices within highly regulated industries. MAM software is perfect for organizations that employ BYOD policies.
- Organizations that have user groups with drastic differences in access rights and responsibilities should consider a hybrid approach, leveraging both MDM and MAM functionality.
- Developing a custom MDM/MAM solution instead of purchasing an off-the-shelf product makes sense if an organization needs a very specific set of features, enhanced cybersecurity, and advanced measures to prevent users from bypassing restrictions.
Whether organizations provide employees with mobile devices or have a Bring Your Own Device (BYOD) policy, they still have to ensure secure use of devices and apps. For example, doctors often use tablets and smartphones for work, so healthcare organizations must protect sensitive patient data stored on those devices. The way to ensure this is by choosing the right approach and software for managing mobile devices.
In Apriorit’s experience, mobile device management (MDM) and mobile application management (MAM) are the most popular options. However, many organizations struggle to decide which fits them best. To help you pick the most fitting approach, we will compare MDM vs MAM software.
This article will be helpful for product and development leaders who are considering developing an MAM and/or MDM solution or enhancing existing software for mobile management. Apart from discovering the pros and cons of MAM and MDM solutions, along with their main differences, you’ll also find out how to use a hybrid approach and what to consider when you decide to build a custom system.
Understanding MDM and MAM
Whatever industry your business is in, it’s likely your users and/or employees receive, send, and process data via mobile devices. Perhaps they even use internally developed mobile apps. Thus, your IT administrators have a real burden making sure mobile devices, users, and data remain protected.
Two proven approaches to secure sensitive data on mobile devices are mobile application management and mobile device management. And since both could be part of more comprehensive approaches, let’s first define key terms to be on the same page:
- Mobile application management (MAM) covers services and solutions responsible for provisioning and controlling access to and use of mobile applications used within an organization.
- Mobile device management (MDM) is a methodology and set of technologies that control and secure the use of mobile devices.
- Enterprise mobility management (EMM) refers to people, tools, and processes responsible for organizing enterprise mobility. EMM software often combines MDM and MAM functionalities into a single tool.
- Unified endpoint management (UEM) is a comprehensive approach to secure all of an organization’s endpoints, including mobile devices, servers, IoT devices, etc. UEM software usually combines EMM, MDM, and client management systems.
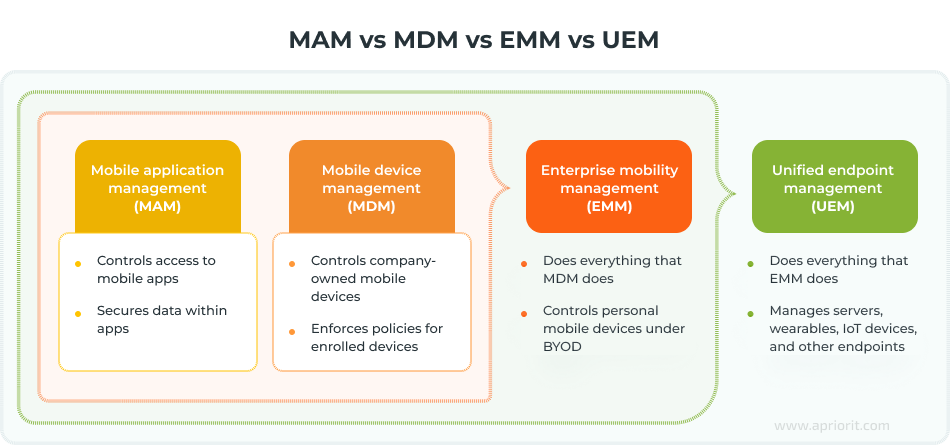
Since we are dedicating this article to MAM and MDM, let’s briefly overview the types of software that support these two management approaches.
What is MDM software?
MDM software helps organizations manage and control corporate devices like smartphones, tablets, laptops, and various terminals. The goal of such systems is to secure both devices and data they store and process by:
- Monitoring device usage
- Enforcing corporate policies on devices
- Forcing device updates
- Backing up files and data
What is MAM software?
MAM software allows organizations to ensure the safety and security of applications on enrolled devices. These can be both company-owned devices and personal devices registered under the BYOD policy. Security officers and IT administrators use MAM solutions to:
- Auto-complete application updates
- Configure permissions
- Monitor app performance
- Separate personal and corporate data within apps
These software solutions have some similarities. For example, they provide app wrapping and containerization features to update apps. Also, both product types usually offer access management capabilities to authenticate and authorize users when they’re accessing apps. Last but not least, MAM and MDM solutions often comprise a single product or are parts of EMM or UEM products, which might create confusion regarding what is MDM and what is MAM.
In the next section, we take a deeper look at how these two software types differ, covering their use cases, security capabilities, and other essential details.
Looking for a trusted software development vendor?
Leverage Apriorit’s expert skills and rich experience to create secure and scalable mobile management solutions tailored to your business needs.
Key differences between MDM and MAM solutions
The differences between MDM and MAM solutions are significant. Mostly, MDM and MAM software differs in terms of use cases, policy enforcement, and security capabilities:
1. Use cases
The main difference between MDM and MAM solutions lies in their purpose. While mobile device management allows your admins to control data at the device level, mobile application management only controls corporate applications on enrolled devices.
Below, we have gathered the most common use cases for MDM and MAM software to clearly show the differences in their purpose:
| MDM is used to: | MAM is used to: |
|---|---|
| Install and update apps remotely | Secure apps like web browsers and email clients |
| Set network preferences and customize mobile device settings | Provide an internal app store of approved applications |
| Activate user accounts | Configure and update apps |
| Control device permissions | Monitor app performance |
| Decommission devices | Support volume licensing |
| Enforce user policies | Enforce default and custom app policies |
| Track device locations and wipe data remotely | Separate corporate and personal data on personal devices |
2. Compliance and policy enforcement
MDM software helps IT teams enforce policies directly on all enrolled devices in bulk. For example, these can include policies for:
- Application management
- Operating system updates
- Device management
- Network and connectivity
- Compliance
- And more
Moreover, admins can easily push any necessary updates when policies are revised or updated. All of this makes it easier for organizations to maintain compliance with common laws, regulations, and standards like the GDPR, the CCPA, HIPAA, and PCI DSS.
Since MAM works at the application level, users can find many ways to ignore compliance requirements and policies, such as using personal apps for corporate tasks. However, if corporate applications have built-in compliance capabilities like data backups and encryption, IT admins can turn those on remotely.
3. Security capabilities
MDM solutions offer a broader range of security features compared to MAM solutions because of their ability to control and secure the entire device. To protect both the device and its apps, MDM products often come with additional security features like:
- Multi-factor authentication (MFA) to make sure only authorized users can interact with devices
- Geolocation, usually GPS-enabled, to track devices if lost
- Built-in VPN services to protect company data when employees work remotely
- Remote data wipe in case a device is stolen
- Device blocking, app and service blocking, activity monitoring, etc.
When working with MAM software, IT admins have to preconfigure corporate apps and push configurations to personal devices. To prevent unauthorized access, your team can also set up automatic app removal conditions if employees leave the company or lose a device. While MAM software is less invasive for users, it can’t provide the same degree of device-level protection as MDM solutions.
With an understanding of their key differences, let’s move to discussing upsides and downsides of MDM and MAM products.
Related project
Enhancing an MDM Platform with a Custom Audio Player in a Continued Partnership
Discover how our team delivered a high-performance custom audio player solution tailored to unique client requirements. Find out the details of how we also helped the client release an audiobook feature to start monetizing the new player early.
MDM and MAM pros and cons
The essential advantage of MDM software is that it lowers the risk of a data breach. Features like remote wipe and lock, data and device encryption, advanced password protection, and forced updates and patching significantly reduce the likelihood of unauthorized access and cybersecurity incidents.
Additionally, IT teams get centralized visibility into all enrolled devices. This helps admins to detect and respond to suspicious behavior and anomalies within an organization’s mobile network. For example, they can spot attempts to install restricted apps. And since MDM solutions usually allow IT teams to enforce policies, updates, and app distribution in bulk, IT teams can accelerate and simplify their workflow.
However, MDM software is not without its cons. When launching a first solution, administrators have to make sure that the back end is designed to handle a growing traffic load as more devices are enrolled with time. And when shifting to a new solution, they have to be extra careful to ensure data integrity and minimize disruptions.
Another vital issue with enabling MDM tools is user and/or employee frustration. Because of significant restrictions on what they can do with mobile devices, employees are likely to experience decreased productivity and even try to bypass security measures. No wonder MDM solutions are rarely used in environments that follow BYOD policies, as people don’t want such intrusive software installed on their personal smartphones and tablets.
| MDM benefits | MDM downsides |
|---|---|
| Fewer security breaches | Challenging software migration |
| Holistic view of network security | Poor user experience |
| Simplified IT management | Complicated adjustment to BYOD policies |
MAM solutions shine best in BYOD environments. They allow employees to work using personal devices while admins enable corporate data protection via app-specific security measures. This provides a pleasant user experience, as employees have few restrictions on how they use their smartphones and tablets. Meanwhile, MAM tools assist IT teams with establishing robust protection for business apps by providing full remote control over them.
As for limitations, MAM software can be tricky to implement because administrators must integrate it seamlessly with existing IT infrastructure, including email servers and VPNs. There’s also a fragmentation issue, as IT teams have to make sure that enterprise applications are compatible across various devices and operating systems. And, as we mentioned earlier, MAM software only controls certain apps, leaving devices vulnerable to threats like malware, unapproved apps, and network spoofing.
| MAM benefits | MAM downsides |
|---|---|
| Perfect for BYOD environments | Challenging to implement |
| Improved app security | Fragmentation |
| Great user experience | Limited security capabilities |
With the most common pros and cons of MDM and MAM tools in mind, let’s discuss how to choose the right type of software for your business needs.
Read also
How to Build a Mobile Device Management (MDM) System
Building an effective MDM system requires the perfect balance of security, usability, and scalability. Dive into best practices, practical advice, and technical insights for creating a solution that meets your business demands.

Choosing between MDM, MAM, and hybrid approaches
Picking the right approach and relevant software to manage the use of mobile devices within an organization is tricky. When making a decision, your team should keep in mind details like security requirements, business goals, budget limitations, employee/user experience, and IT burden. Below, we offer brief recommendations on the most important things to consider when choosing a type of mobile management solution.
When to choose an MAM solution:
- Your organization isn’t obliged to comply with strict requirements. If your IT teams confirm that you can ensure proper protection of corporate apps on potentially insecure devices using MAM capabilities, there’s no need for more complex technologies.
- You have a limited budget. MAM tools are usually more affordable than MDM. The reason is that MAM solutions often employ a per-app or per-user pricing model, making them less expensive for businesses that only need to manage specific applications. Developing a custom MAM solution is also often cheaper and faster than developing a custom MDM solution. So, as long as they can cover your security requirements, you can choose MAM capabilities to save money. However, your team still needs to conduct precise calculations before making a final decision.
- Your business has a BYOD policy. MAM tools secure control over business apps without sacrificing privacy for employees who use personal devices for work. This leads to a better user experience and even better productivity, as employees aren’t frustrated with too many restrictions.
When to choose an MDM solution:
- Your industry is highly regulated. The more security requirements your business has to comply with, the more restricting the technologies you should use to safeguard data. This ensures advanced protection for sensitive information, including corporate, employee, and customer data.
- You only allow company-owned devices. If employees are obliged to use corporate tablets and smartphones for work, then there’s no need for half measures like MAM control. In this case, your IT teams can enforce any strict security policies across the entire device with minimum consideration for user privacy.
- You need device-level control. If you need to manage critical device features like camera access, web filtering, and app installations, MDM is the best choice. For example, companies might want to disable camera or Bluetooth functionality to prevent data leaks or unauthorized data sharing. Also, if devices store critical information, MDM’s ability to launch remote data wipe in case of device loss or theft is crucial.
What should you do if you need some features of both approaches?
Apart from using strictly MDM or MAM capabilities (or deploying advanced EMM or UEM software), businesses can employ a hybrid approach. This could come in handy when organizations have user groups with drastic differences in access rights and responsibilities. With a hybrid approach, your IT team can ensure that:
- Staff that handles the most sensitive data has MDM capabilities deployed on their devices.
- Staff with limited to no access to sensitive information has MAM capabilities on their devices.
This allows organizations to provide highly protected devices only to those who need them while still partially leveraging the benefits of BYOD policies, as other employees can use their personal smartphones and tablets.
Note: When choosing the hybrid approach, make sure your tech team selects compatible tools that support both MDM and MAM functionalities for seamless integration. It’s also crucial to choose solutions that are compatible with your existing IT infrastructure. Another option is to build a custom solution that’s flexible and tailored to your business needs.
Let’s explore what a custom product for mobile management can bring to your organization and what to consider when creating such software from scratch.
Related project
Developing a Custom MDM Solution with Enhanced Data Security
Find out how the Apriorit team created a scalable and secure Android MDM platform to help our client enhance enterprise mobility management and ensure seamless device control.
What to consider when creating custom MDM and MAM solutions
Choosing to build a custom MAM, MDM, or hybrid solution instead of using a commercial solution can help your organization to:
- Enable the exact features you need, without paying for unnecessary features included in off-the-shelf solutions
- Ensure support for all devices and operating systems used within your networks
- Implement strong security mechanisms in accordance with technical and industry requirements
- Introduce robust measures to prevent users from bypassing MDM/MAM restrictions
Let’s take a look at key details to consider when deciding to build a custom solution for mobile management:
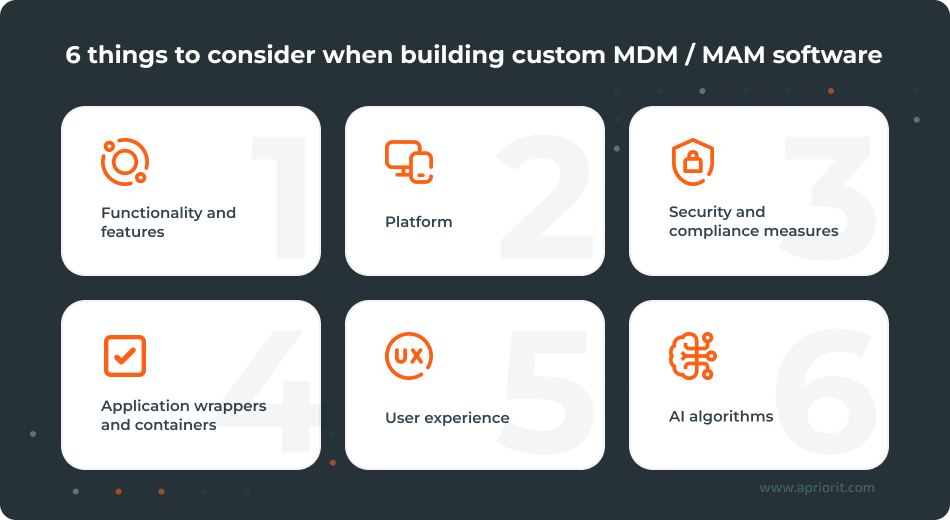
1. Functionality and features
Choosing what features to include in your future solution can be trickier than you might expect. When researching functionalities presented in third-party software, it’s easy to get overwhelmed and plan features that seem helpful but are not exactly necessary for your business. Make sure to focus on organizational needs first and start your planning phase by evaluating the most critical functionalities. Below, we briefly explore key functionalities and features worth considering.
For mobile device management solutions:
- Enrollment functionality is crucial for installing an MDM solution on a mobile device. Make sure your software development provider ensures support for bulk enrollment to install software packages on multiple devices at once. Also, consider over-the-air (OTA) technology to distribute and install MDM software and its components and modules via a website or app.
- Profile and policy management allows admins to assign profiles for device users and manage sets of rules and permissions for a given device group.
- Device administration and troubleshooting provide opportunities for pushing and updating policies remotely, monitoring devices remotely, detecting suspicious actions, and investigating them. You can also add location tracking via GPS.
- Kiosk mode helps administrators to limit what software can be downloaded on the device.
For mobile application management:
- App distribution should be established and automated based on user groups to provide employees only with the apps they need for their jobs.
- A self-service portal can help employees or users request approval for commercial and in-house apps from the IT team.
- App management features should help admins conveniently configure app permissions and settings, preventing potential modifications on the end-user side. This feature set should also include capabilities for pushing app updates.
- Application blocking functionality is crucial to ensure data and device security by mandating the presence of specific apps.
Both solution types should also enable features like custom VPNs, single sign-on, and threat detection.
2. Platform
All organizations should first identify the types of devices they intend to manage, as the hardware and software of smartphones, tablets, and laptops vary across manufacturers.
When selecting a platform for mobile management, consider cross-platform compatibility, making sure your solution can operate across iOS, Android, and the web to enhance user accessibility and engagement.
Another critical factor when choosing a platform is ensuring integration with existing customer relationship management, enterprise resource planning, payroll software, and other enterprise systems. This can help your business enable a smooth data flow between apps, reducing the risk of errors.
3. Security and compliance measures
Key mechanisms and practices to safeguard data both at rest and in transit include:
- Strong encryption protocols like TLS, AES, and EAP-TLS
- Secure authentication methods like MFA
- Regular security audits to identify vulnerabilities and ensure that the system remains resilient against emerging threats
- Regular app updates and patching to address vulnerabilities and improve overall app performance
Compliance-driven measures depend on what countries and industries an organization operates in. Most commonly, MAM and MDM solutions must comply with the EU’s General Data Protection Regulation (GDPR). If your business is healthcare-related and operates in the US market, make sure your software development vendor pays attention to the Health Insurance Portability and Accountability Act (HIPAA) when implementing data security measures.
4. Application wrappers and containers
Application wrapping and containerization are essential techniques that enhance the flexibility of MDM and MAM solutions. Though they aim to protect corporate data, they differ in implementation and functionality:
- App containerization involves creating code-based containers that can be integrated directly into applications. These containers effectively separate corporate apps from personal data on the device, ensuring that sensitive information remains secure and accessible only within the containerized environment.
- App wrapping applies dynamic libraries over an application’s compiled code without requiring access to the source code. This method allows organizations to define custom security measures, such as encryption protocols, tailored to individual applications.
The choice between application wrapping and containerization depends on an organization’s needs and existing infrastructure. Containerization offers broader management capabilities across multiple apps, while wrapping provides a quicker, more straightforward implementation for securing individual apps.
5. User experience
We’ve mentioned above that MDM solutions tend to provide a poor user experience, unlike MAM software. However, when developing a custom solution, you can overcome issues related to using highly restricted devices, reducing employees’ frustration and improving productivity.
Here are key details to keep in mind when planning the user experience for a custom mobile management solution:
- Provide an intuitive design so IT admins can quickly get used to the software
- Offer adequate training resources to help users understand how to work with a restricted device or with limitations in application usage
- Enable feedback mechanisms to gather insights from staff on app performance and usability, guiding the development team on what updates to plan for the future
- Ensure that new features can be added or existing features easily modified as your business needs evolve
6. AI algorithms
When building a custom mobile management solution, it’s worth considering using artificial intelligence to automate administrative tasks and enhance cybersecurity capabilities. The most promising use cases of AI implementation in MAM and MDM software include:
- Predictive maintenance to analyze device performance data and forecast potential failures or maintenance needs
- Device management automation to accelerate tasks like application installations, updates, and policy enforcement
- Advanced user analytics based on patterns in app usage, device location, and data consumption
- User activity monitoring to quickly detect suspicious behavior, which can be a sign of unauthorized access, malware presence, or other cybersecurity threats
- Virtual assistance to provide users with immediate support for simple device-related issues and allow administrators to focus on complex requests
To deliver a truly successful mobile management solution, make sure to partner with a trusted software development vendor who has experience in device and application management.
Related project
Building a Complex Parental Control App for Android
Discover how Apriorit developed a cutting-edge parental control app equipped with advanced monitoring tools, secure communication features, and a user-friendly interface to empower parents in safeguarding their children online.
How Apriorit can help you with MDM and MAM development
No matter the industry your organization operates in and the complexity of the solution you need, Apriorit is ready to help.
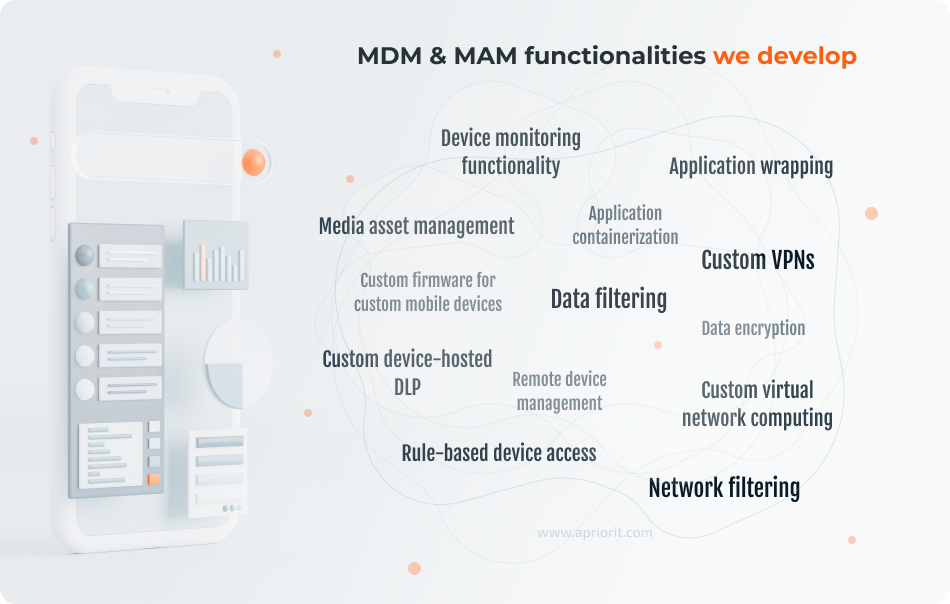
We have rich experience working on MDM and MAM functionalities. For example, our engineers can help you:
- Develop parental control applications with robust traffic filtering capabilities, custom VPNs, and blocking of restricted apps
- Build enterprise MDM solutions with a strong focus on cybersecurity, improved data protection measures, and advanced capabilities for managing tablets
- Enhance MDM solutions with additional features according to your business needs, such as custom audio players for music and audiobooks
With 20+ years of experience delivering various software products, we focus on helping our clients achieve their business goals by:
- Providing thorough research and conducting a project discovery phase
- Choosing the most relevant and efficient technologies and tools to streamline software creation
- Building protected solutions by using the secure software development lifecycle (Secure SDLC) approach
- Conducting professional quality assurance activities and offering support and maintenance services
- Delivering efficient software products that meet clients’ technical requirements and business needs
Once you delegate your mobile management project to Apriorit, we will proceed with careful planning and implementation, regularly updating you on project progress and achievements.
Conclusion
Though used for different purposes, both mobile device management and mobile application management software help organizations control mobile devices and protect user and corporate data. Once you decide which approach to use, you might find that off-the-shelf solutions don’t provide enough functionality to cover all your security needs.
Developing a custom solution for managing mobile devices within your organization’s networks can help you achieve the best results. Whether you choose MDM, MAM, or a hybrid approach, Apriorit’s engineers are ready to help you compose and deliver the exact software you envision.
Need to create a robust mobile management solution?
Level up your mobile device and app management with custom MAM/MDM software development services by Apriorit experts.


