When building a new mobile app or maintaining an existing mobile app, your team should focus on the security of user data. Users entrust your app with all kinds of information — personal data, payments and transactions, credentials, etc — and they expect it to handle this data with great care.
How can you ensure that critical data is secure within your app?
One way is to follow the recommendations from the OWASP Mobile Top 10, which is the gold standard for secure mobile application development. In this article, we overview the latest version of this list — OWASP Mobile Top 10 2024 — and compare it to the renowned 2016 version. This analysis will help you and your development team learn which mobile cyber threats and misconfigurations to be wary of when building or improving your mobile products.
Contents:
- What is the OWASP Mobile Top 10?
- OWASP Top 10 Mobile Risks: mitigation strategies for essential protection
- M1: Improper Credential Usage
- M2: Inadequate Supply Chain Security
- M3: Insecure Authentication/Authorization
- M4: Insufficient Input/Output Validation
- M5: Insecure Communication
- M6: Inadequate Privacy Controls
- M7: Insufficient Binary Protections
- M8: Security Misconfiguration
- M9: Insecure Data Storage
- M10: Insufficient Cryptography
- Build secure mobile applications with Apriorit
- Conclusion
What is the OWASP Mobile Top 10?
Since its founding in 2001, OWASP has become an established online community whose main goal is to deliver unbiased and free analysis and guidelines on cybersecurity. In particular, OWASP delivers comprehensive vulnerability lists that software developers and cybersecurity specialists largely consider the gold standard.
Custom cybersecurity tools and clear technical guidelines, such as the OWASP mobile security testing guide, make OWASP valuable and trustworthy for technical communities. That’s why the OWASP Top 10 for mobile applications is a go-to guideline for building well-secured, vulnerability-free solutions for mobile development teams worldwide.
The OWASP Mobile Top 10 security list is based on data carefully gathered from vendors and consultants, analyzed, and distilled into ten categories encompassing the most common and critical mobile security vulnerabilities.
The official OWASP website provides a complete description of each risk category. In the next section, we analyze what has changed since the previous update in 2016 and analyze each risk category from the latest version of the Mobile Top 10.
Need to evaluate your mobile app’s security?
Apriorit quality assurance experts will thoroughly analyze your application and provide actionable tips on improving its security.
OWASP Top 10 Mobile Risks: mitigation strategies for essential protection
Before we analyze the current top ten categories of mobile security risks according to OWASP, let’s briefly overview the main differences between the current list and the 2016 version.
With an initial release in 2023 and final release in 2024, the renewed OWASP Top 10 mobile risks list has four types of changes:
- New risk categories
- Merged risk categories
- Reordered risk categories
- Removed risk categories
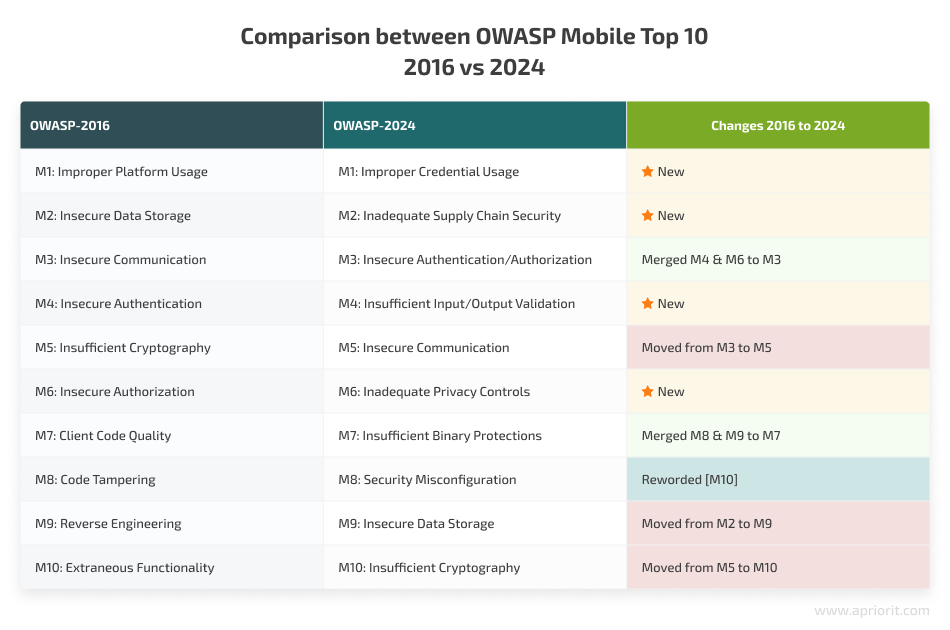
Now that we understand what has changed, let’s analyze the possible impact of relevant vulnerabilities and then move to discussing recommended mitigation and prevention strategies for each of these ten risk categories.
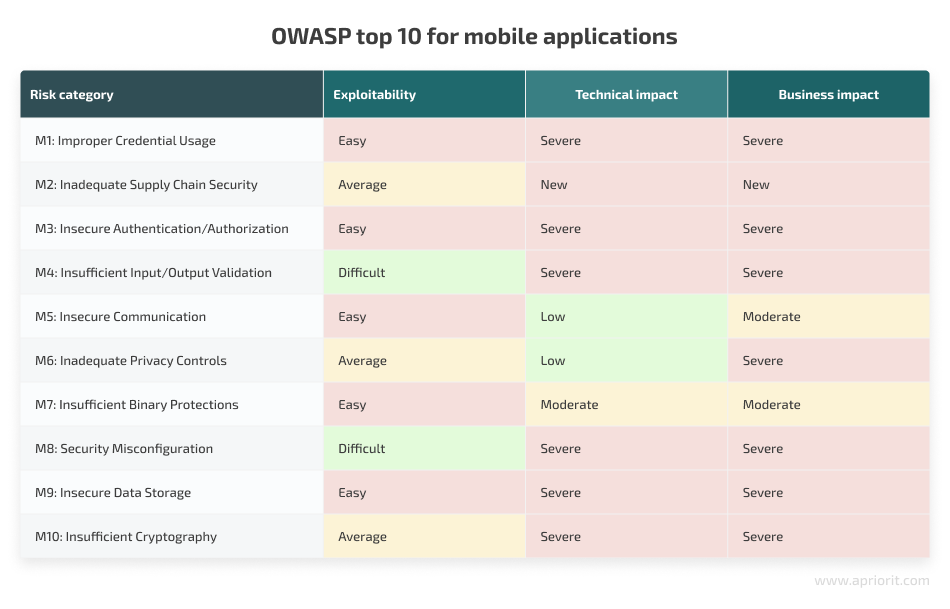
In the following sections, we cover the core aspects your development teams will need to consider, including possible impacts and recommended mitigation practices for specific categories.
M1: Improper Credential Usage
Mobile applications rely on credentials to provide regular and admin users different access levels to services and data. When misused or exploited by hackers, these credentials can lead to data breaches and unauthorized access to sensitive data or enable fraudulent activities within the app.
To prevent these risks, your mobile development team should pay attention to:
- Storage of credentials — Avoid having credentials hardcoded in the application’s code and stored as plain text.
- Transmission of credentials — Rely on secure communication protocols (e.g., HTTPS) and use data encryption.
- Authorization mechanisms — Enforce strong password policies to prevent the use of weak, guessable passwords and poorly secured password recovery channels.
Read also
Comparison of Identity and Access Management Services: Building an On-premises Solution vs a Cloud-hosted Solution
Explore which deployment option to choose before building your custom identity management solution.

M2: Inadequate Supply Chain Security
Third-party components like libraries and SDKs play an integral part in developing mobile solutions. However, if not properly managed, these components can lead to significant security risks, including insertion of malicious code, data loss, and unauthorized access to sensitive data.
To mitigate these risks, mobile development teams need to pay special attention to the following:
- Choosing secure, vetted components — Ensure that all third-party libraries and SDKs used in an application come from reliable sources and get regular security updates.
- Implementing secure development practices — Deploy secure coding practices to maintain a safe development environment and prevent vulnerabilities during development.
- Application distribution and monitoring — Verify the application’s integrity during distribution with code signing measures and continuously monitor code for unauthorized modifications or tampering.
M3: Insecure Authentication/Authorization
Implementing poorly secured authentication and authorization mechanisms within a mobile app is associated with vulnerabilities that, when exploited by hackers, create significant security risks, such as identity theft and unauthorized data access.
To prevent these risks, make sure your engineers dedicate enough time to improving:
- Authentication practices — Enforce complex password requirements, use multi-factor authentication (e.g., biometrics), and store passwords using strong hashing algorithms.
- Authorization mechanisms — Implement role-based access control (RBAC) to limit users’ access permissions according to roles. Ensure that backend systems validate roles and permissions independently of the mobile device.
- Session management — Implement secure session timeouts and re-authentication mechanisms to protect against unauthorized access due to prolonged sessions.
Read also
How to Ensure Your Mobile Banking App’s Security: Tips and Best Practices
Get expert advice on what to pay attention to when building a custom mobile solution for the banking or financial sector.

M4: Insufficient Input/Output Validation
When applications fail to validate and sanitize input and output data, they open themselves up to various security threats, including SQL injection, command injection, and cross-site scripting (XSS) attacks.
These threats can lead to the exposure of confidential information, system compromise, and data manipulations.
To safeguard against these risks, your mobile development team needs to be cautious about:
- Input validation — Implement input validation, using allowlisting techniques to allow only specific, known-safe inputs and reject anything that doesn’t meet established criteria.
- Output encoding — Apply output encoding to ensure that any data presented to the user is safe and cannot be executed as code. This reduces the risk of injection attacks where malicious content is interpreted as executable code.
- Database interactions — Leverage parameterized queries when working with databases to ensure proper separation of data and code, thus preventing SQL injection attacks.
- Content security policies (CSPs) — Enforce CSPs to mitigate XSS attacks. In particular, specify valid content sources, ensuring that the app loads only trusted scripts and resources.
- Security libraries and frameworks — Install new security updates and patches regularly to promptly address discovered vulnerabilities.
M5: Insecure Communication
Mobile apps that transmit data without proper encryption or use outdated communication methods become vulnerable to data interception and tampering, including to man-in-the-middle (MITM) and phishing attacks.
Possible risks related to poorly secured communication include identity theft, interception and manipulation of transmitted data, and unauthorized access to critical data.
To mitigate these risks and improve the security of data transmitted by a mobile app, development teams can:
- Secure data transmission protocols — Secure data in transit by using HTTPS instead of HTTP, ensuring proper data encryption and preventing eavesdropping on sensitive information.
- Implement certificate pinning — Use SSL/TLS certificate pinning to prevent MITM attacks in which attackers intercept communication by presenting a forged certificate.
- Enhance data storage security — Avoid storing sensitive information like passwords locally and ensure that stored data is encrypted and securely managed.
- Improve session management — Enforce secure session practices such as session timeouts and token regeneration to protect the app against session hijacking.
Related project
Developing a Custom ICAP Server for Traffic Filtering and Analysis
See how we helped our client attract new customers and increase revenue by increasing the security of their cloud service with a custom ICAP server for traffic filtering and analysis.
M6: Inadequate Privacy Controls
Hackers often specifically target personally identifiable information (PII) like names, credit card details, and other sensitive personal data. When developers fail to implement robust measures to protect users’ data privacy, it can result in excessive data collection, adoption of inadequate consent mechanisms, and weak data handling practices that can eventually lead to:
- User privacy violations
- Identity theft
- Fraud and misuse of payment data
To mitigate risks associated with user data privacy, mobile app development teams need to work on:
- Data collection and storage — Store only the data required for the app’s functionality and use robust encryption methods to protect it from unauthorized access.
- User consent for data collection and storage — Implement clear and informed consent mechanisms for data collection and storage. Enable app users to manage and update their consent preferences within the app, ensuring transparency in how their data is used.
- Data deletion mechanisms — Implement clear procedures for deleting unnecessary private information and create options for users to delete their data on demand.
- Security audits — Conduct regular security audits and assessments to identify and address potential data security vulnerabilities and data privacy violations. This includes reviewing and erasing unnecessary user data to minimize potential risks.
M7: Insufficient Binary Protections
App binaries are critical to the functionality and security of mobile applications. However, they are often targeted by attackers who may use dynamic analysis and reverse engineering techniques to find and exploit weaknesses in your app’s code. If successful, they can cause significant security issues such as:
- Exposure of sensitive data and proprietary logic
- Injection of malicious code and code tampering
Your development team should implement robust security measures to safeguard application binaries and ensure the integrity and confidentiality of your app. Recommended binary protection measures include:
- Runtime protections — Employ tamper detection mechanisms and runtime application self-protection (RASP) solutions to monitor and defend the app during its execution.
- Monitoring and integrity checks — Regularly check the app’s binary code for unauthorized modifications using checksums, digital signatures, and integrity checks.
- Code encryption and obfuscation — Encrypt sensitive parts of the binary code and use obfuscation tools to make it difficult for attackers to reverse engineer the app and understand its inner logic and operations.
Read also
Using LLVM to Obfuscate Your Code During Compilation
Learn how bytecode obfuscation with LLVM can help your development team ensure comfortable maintenance and easy debugging of highly secure, obfuscated code.
M8: Security Misconfiguration
Mobile app security measures can be either not implemented at all or inadequate, with a common issue being the use of default, usually insecure settings. If exploited by hackers, such misconfigurations make the application vulnerable to denial of service attacks, sensitive data exposure, access abuse, and more.
Mitigation measures meant to strengthen and improve security configurations of mobile apps include:
- Customizing default settings — Ensure mandatory modification of default security configurations to increase data protection and limit access permissions.
- Implementing secure coding practices — Your development team should adhere to security best practices and guidelines at each stage of your app’s development lifecycle.
- Running vulnerability assessments — Regularly scan and analyze your mobile app for possible data security and access control misconfigurations. This can be done with automated security tools or independent security audits.
M9: Insecure Data Storage
When a mobile application has weak authentication mechanisms and poor or nonexistent encryption, the data stored by the application can be intercepted, stolen, deleted, or manipulated by hackers. This can result in data breaches, identity theft, and fraudulent activities.
Here are some practices your development team can implement to enhance data storage security:
- Deploy robust encryption mechanisms — Encrypt sensitive data both in transit and at rest and establish proper security measures for managing cryptographic keys.
- Incorporate secure storage practices — Store sensitive information in secure, well-protected locations, avoid storing unnecessary data, and delete data you no longer need for your app’s operation.
- Enhance access controls — Implement role-based access controls and advanced authorization mechanisms, remove excessive access permissions, and limit access to your app’s critical data and components.
M10: Insufficient Cryptography
When a mobile application relies on weak encryption mechanisms or mismanages cryptographic keys, hackers can easily decrypt and misuse critical data, thus violating its confidentiality, integrity, and authenticity.
Preventive measures for enhancing data encryption mechanisms include:
- Using strong encryption algorithms — Employ robust encryption methods like Advanced Encryption Standard (AES) encryption algorithms and update them regularly to maintain effective protection against emerging cyber threats.
- Proper key management — Protect encryption keys from unauthorized access and rotate them regularly.
- Security audits — Regularly conduct security assessments to identify and timely address vulnerabilities in deployed encryption mechanisms.
Read also
Building a Transparent Encryption Framework to Secure Android Applications: A Step-by-Step Guide
Explore an expert guide on building a custom automated encryption framework that improves ciphering transparency and saves mobile app developers’ time.

Build secure mobile applications with Apriorit
With over 20 years of experience in cybersecurity, Apriorit can help you ensure the ultimate security for your mobile application.
Depending on your project needs, our seasoned experts can help you with:
- Research & discovery — Elicit requirements and estimate the budget for your new project.
- MVP development — Create a future-proof MVP or PoC to test your idea and present it to investors.
- Mobile app development — Build a custom mobile application from scratch.
- Legacy product modernization — Enhance your existing product with new features and capabilities.
- Quality assurance — Test and audit the security and performance of your mobile application.
When you delegate your mobile project to Apriorit, you can be sure that our team will consider OWASP recommendations as well as local and industry-specific regulatory requirements.
Conclusion
Creators and vendors of mobile solutions should pay special attention to how they authorize users and handle their credentials, employ robust encryption mechanisms for data both in transit and at rest, and only store data necessary for their applications’ proper functioning.
OWASP Top 10 Mobile Risks is a helpful guide that mobile development teams can use when developing, testing, and supporting mobile solutions to identify and mitigate the most impactful cybersecurity risks, thus ensuring an application’s security, performance, and competitiveness.
By partnering with Apriorit, you can establish a dedicated team for your mobile app project with hand-picked experts in mobile app development, quality assurance, business analysis, and cybersecurity.
Along with ensuring the timely delivery of a secure and competitive product, the Apriorit team will gladly assist you with evaluating and enhancing the security of your application code to strengthen your mobile app against emerging cybersecurity threats.
Want to build a highly protected mobile solution?
Leverage Apriorit’s expertise in cybersecurity and mobile app development for the benefit of your business!


