As quantum computing advances at an unprecedented pace, it threatens traditional cryptographic methods that software creators currently rely on for security. The power of quantum computers has the potential to break widely used encryption algorithms, leaving sensitive data vulnerable to decryption.
For software providers, this means one thing: preparation is essential. When post-quantum cryptography (PQC) becomes standardized, software vendors must be ready to seamlessly integrate these new algorithms. This demands a shift towards crypto-agile architectures — flexible software systems that can quickly adopt new encryption methods and security practices.
This article is for cybersecurity solution owners and those seeking to enhance the security of their systems against the threats posed by quantum cryptography. We will explore the main principles of a crypto-agile architecture, practical steps for implementation, and how preparing for post-quantum cryptography will allow your business to stay safe and relevant in the long run.
What is post-quantum cryptography?
Post-quantum cryptography, also called quantum-safe or quantum-resistant cryptography, is the development of algorithms designed to secure data against both classical and quantum computing attacks.
Today, digital security heavily relies on cryptographic algorithms such as Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). These algorithms secure communications, financial transactions, and data across industries.
Traditional cryptographic algorithms depend on the inability of classic computers to perform certain mathematical calculations, such as factoring large numbers and solving discrete logarithms. On the other hand, quantum computers can potentially solve these problems — for example, Shor’s algorithm can theoretically crack RSA and ECC. This becomes possible due to quantum computers using quantum bits (qubits) instead of classical bits. They exploit quantum phenomena such as superposition and entanglement to perform certain types of computations exponentially faster than traditional computers.
Unlike traditional cryptographic methods, PQC algorithms are resistant to both classic and quantum computing attacks. This means they rely on mathematical problems that are hard to solve even with quantum computational capabilities.
Currently, quantum computers lack the power to execute harmful quantum algorithms and crack traditional cryptography. However, as soon as quantum computers become more available and powerful, hackers will be able to use them and cause detrimental consequences for businesses, including:
- Compromising encrypted data. Even if encrypted using traditional cryptography methods, sensitive data will no longer be protected, as quantum computers will be able to decrypt it rapidly.
- Stealing intellectual property. Quantum computers can efficiently break cryptographic protections around proprietary technologies, software, and algorithms, allowing adversaries to reverse engineer and exploit these assets.
- Obtaining unauthorized access. Digital signatures that are currently secure could be forged using quantum computers, leading to unauthorized access to systems, fraudulent transactions, and other incidents that lead to financial and reputational loss.
- Exposing sensitive data. Quantum computers can decrypt previously intercepted secure communications, exposing sensitive business data that was believed to be secure.
- Negating future-proofing efforts. Businesses may end up having wasted the time and money put into encryption as quantum computers make current cryptographic methods obsolete.
Businesses will eventually need to integrate PQC algorithms into their systems to protect their data, reputation, and business operability. Let’s discuss the current state of the PQC landscape and find out what is available for organizations.
Want to protect your software against quantum threats?
Leverage our vast experience to improve your software today so your data is shielded from the cybersecurity threats to come.
NIST progress in defining PQC strategies
In 2024, the National Institute of Standards and Technology (NIST) finalized the post-quantum cryptography standards with the approved PQC algorithms. They include:
Table 1: NIST-approved PQC standards
| Category | Standard | Algorithm | Former algorithm name |
|---|---|---|---|
| General encryption and key exchange | FIPS 203 | ML-KEM (Module-Lattice-Based Key-Encapsulation Mechanism) | CRYSTALS-Kyber |
| Digital signature | FIPS 204 | ML-DSA (Module-Lattice-Based Digital Signature Algorithm) | CRYSTALS-Dilithium |
| FIPS 205 | SLH-DSA (Stateless Hash-Based Digital Signature Algorithm) | Sphincs+ | |
| FIPS 206 (draft) | FN-DSA (FFT over NTRU-Lattice-Based Digital Signature Algorithm) | FALCON |
These algorithms are intended to replace or augment current cryptographic methods that are vulnerable to quantum attacks.
Currently, it’s quite challenging to apply these algorithms to real-world solutions, as there are very few post-quantum libraries with integrated PQC algorithms.
Despite this, a few companies are already experimenting with implementing PQC algorithms in their products, libraries, and services. Here are some examples of projects that have applied PQC to their solutions:
- The Open Quantum Safe project uses PQC encryption in their C library liboqs.
- Microsoft is working on a PQ Crypto fork of OpenSSL, one of the most popular encryption libraries.
- The Chrome browser supports Kyber768, a NIST-approved key encapsulation method.
For most businesses, however, PQC integration isn’t feasible right now, as it’s currently associated with high costs, significant computing requirements, and the inability to field-test quantum algorithms.
With NIST having finalized the post-quantum cryptography standards, more PQC implementations are becoming available to developers. To take advantage of these advancements, it’s crucial for your software to be ready for seamless integration as these implementations emerge.
This is where crypto-agility comes in. By adopting a crypto-agile approach, you can ensure that your software is prepared to quickly incorporate the latest NIST-approved PQC algorithms, keeping your systems secure and adaptable to future cryptographic developments.
Crypto-agility as a way to prepare for post-quantum cryptography
Cryptographic agility, or crypto-agility, is a set of qualities that allows software systems to quickly switch between different cryptographic algorithms or protocols without significant overhead and operational disruptions.
Making your software systems crypto-agile will allow you to swap to quantum-resistant algorithms once they become more widely available and protect your data and system integrity from future quantum threats. In addition, adopting crypto-agility will improve your overall cybersecurity posture, help you gain customer trust, and stay competitive.
What makes a system crypto-agile?
According to NIST, crypto-agile systems should be able to:
- Select appropriate security algorithms in real time based on current operations
- Add new cryptographic features and algorithms to existing software
- Easily retire cryptographic algorithms that are no longer secure and relevant
To have these abilities, your software solution should have crypto-agile properties.
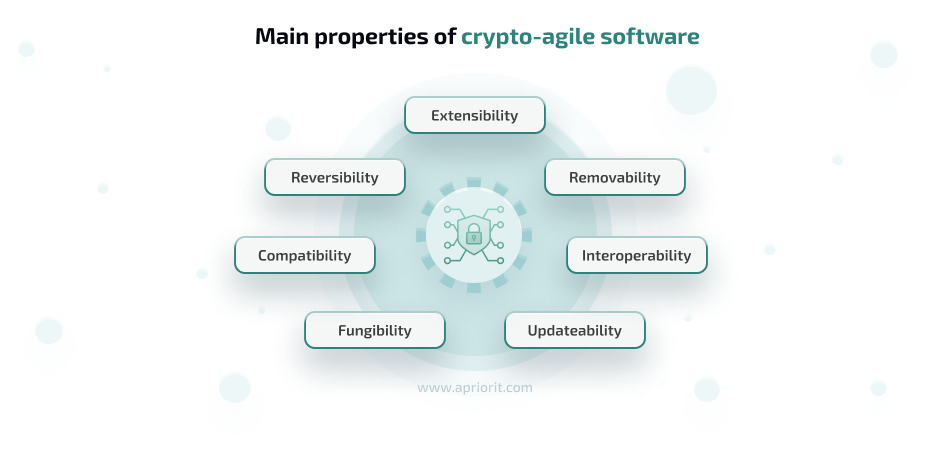
- Extensibility — the ability to add new cryptographic features or algorithms to existing systems so that your system is always updated with the latest security measures.
- Removability — the ability to easily remove outdated or compromised cryptographic algorithms. This maintains system security by eliminating vulnerabilities from obsolete cryptographic methods.
- Fungibility — the ability to smoothly change cryptographic components without affecting system functionality.
- Interoperability — the ability of different systems and components to work together using various cryptographic methods.
- Updateability — the ease with which cryptographic algorithms can be updated or patched. This enables quick responses to new threats and vulnerabilities, maintaining robust security.
- Compatibility — the ability of new cryptographic methods to work with existing systems and protocols, allowing you to integrate your systems with new technologies without major overhauls.
- Reversibility — the capacity to revert to previous cryptographic methods in case new algorithms introduce issues or vulnerabilities.
Ensuring the flexibility of a crypto-agile system will allow you to protect it from emerging threats in the future and better maintain it, implement new features, and adapt to market demands.
Read also
5 Emerging Cybersecurity Trends for Software Development in 2024 to Futureproof Your Product
Explore the latest cybersecurity strategies and technologies that will help you protect your digital products in 2024 and beyond in our expert guide.

When do you need to build a crypto-agile system?
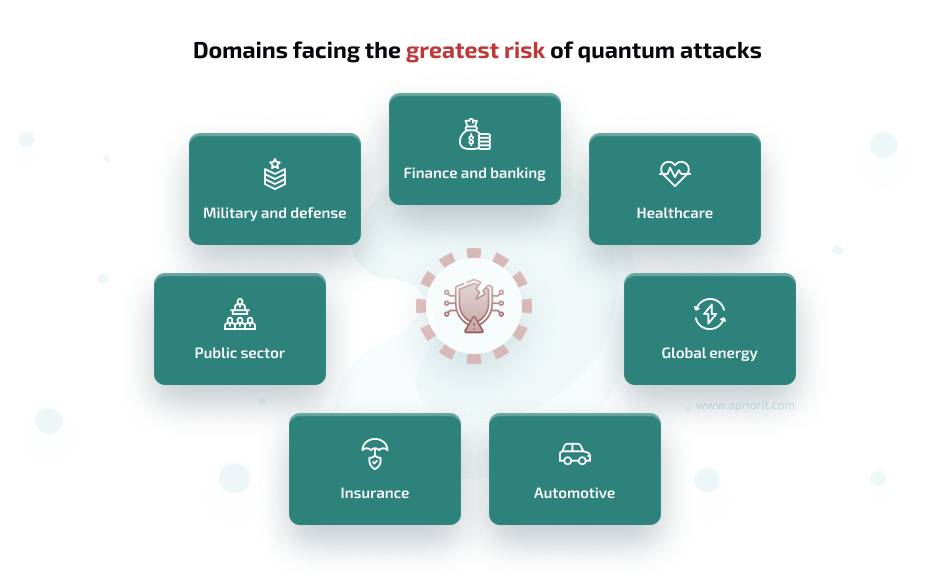
In the future, the threat of quantum attacks will be relevant for all businesses that handle user data. This means that every business will need to turn to crypto-agility sooner or later. However, some categories of businesses should adopt crypto-agility as soon as possible, as they will be targeted first.
If your software solutions handle highly sensitive data, you should consider adopting crypto-agile principles for your system right now. Such data includes classified government information, personal health records, financial data, and intellectual property.
Data shelf life is another criterion that may indicate that you urgently need to adopt crypto-agility. Data that is expected to remain sensitive for many years is vulnerable to harvest now, decrypt later attacks. This strategy enables hackers to collect encrypted data today (such as insurance contracts, trade secrets, and proprietary research), store it, and decrypt it once quantum computers are available.
Businesses and organizations in these domains face the greatest risk of quantum attacks due to the sensitivity of the data they deal with:
Now that we’ve identified the sectors that need to prepare for post-quantum cryptography the most, let’s look at what challenges to be aware of when starting your journey towards software crypto-agility.
Challenges of implementing software crypto-agility
Making your system flexible and advanced enough to handle the latest cryptographic algorithms is challenging from both technical and business standpoints. Let’s look at the main challenges to be aware of when planning your software’s shift to crypto-agility.
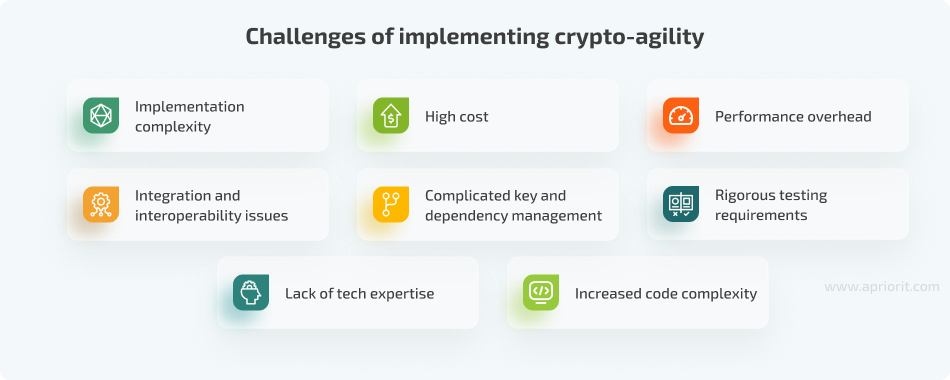
- Implementation complexity. Designing and creating a system that can dynamically switch between cryptographic algorithms is challenging from a technical standpoint.
- High cost. The cost of initial implementation, ongoing maintenance, and new integrations can be too high for smaller projects with limited budgets.
- Performance overhead. Implementing flexible cryptographic solutions often introduces additional computational overhead, which can harm system performance.
- Integration and interoperability issues. Achieving interoperability and the ability to integrate systems using different cryptographic algorithms requires careful coordination and standardization. This is especially true for legacy systems that require even more resources to become compatible with modern cryptographic technologies.
- Complicated key and dependency management. You need to establish efficient and secure management and storage of multiple cryptographic keys and certificates. In addition, your engineers will need to regularly update dependencies on cryptographic libraries so they are up to date with the latest security patches and algorithm updates.
- Rigorous testing requirements. Your team needs to regularly test and validate new cryptographic algorithms to ensure they don’t introduce new vulnerabilities or break existing functionality.
- Increased code complexity. Adding support for multiple cryptographic algorithms complicates your software’s code and can introduce new bugs and vulnerabilities, so performing regular code reviews, refactoring, and various kinds of testing is important.
- Lack of tech expertise. Cryptography and cybersecurity are niche fields, so hiring and retaining skilled professionals in this domain can be hard. Scarcity of talent can hinder the development and maintenance of crypto-agile systems.
Most of these challenges are solvable with an expert team by your side to implement, test, and integrate innovative cryptographic solutions into your software or build a brand-new system with crypto-agility at its core. We will gladly provide you with such a team.
Let’s now examine specific technical steps your project team can take to make your software more crypto-agile today.
Read also
Building a Transparent Encryption Framework to Secure Android Applications: A Step-by-Step Guide
Protect your users’ sensitive data in your application. Learn how to make the encryption process reliable and convenient and safeguard data on an Android device even if it’s rooted.

4 steps to prepare for post-quantum cryptography with crypto-agility
Achieving crypto-agility is a long process that includes operational and technical changes to your organization, business processes, and software. Let’s look at the software side of things and determine how to prepare for post-quantum cryptography by making your system more crypto-agile.
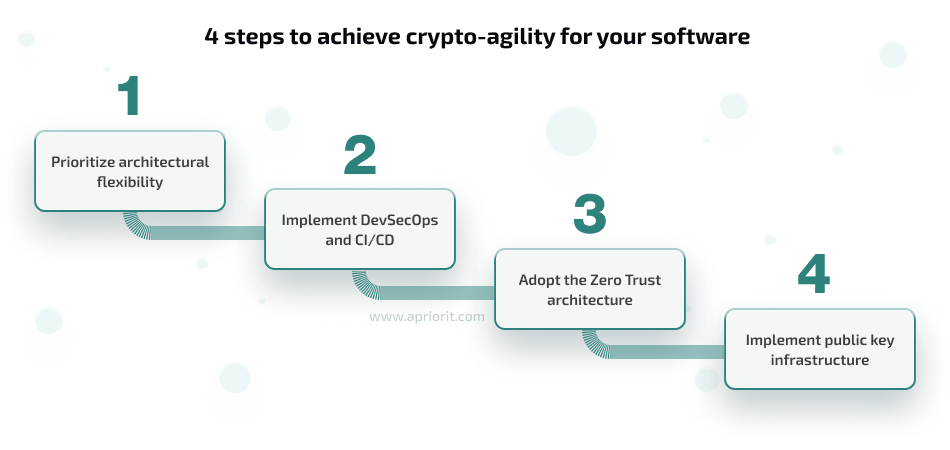
Step 1. Prioritize architectural flexibility
The architecture of your software system should be flexible enough that you can quickly add, replace, and manage cryptographic components without disturbing the overall functionality. Traditional monolithic architectures aren’t flexible enough, so your team needs to consider progressive and distributed types of software architectures such as:
- Microservices architecture
- API-centric architecture
- Service-oriented architecture
- Plugin architecture
These architectures commonly consist of loosely connected parts like modules, services, layers, or components that communicate through APIs and networks. They share common characteristics that include:
- Modularity. The architecture consists of small, self-contained units or modules. Each module handles a specific function, such as user authentication, data encryption, inventory management, or payment processing.
- Independence. Components operate independently, reducing dependencies between them. This independence allows each component to be modified, replaced, or scaled without impacting others, facilitating rapid adaptation to new cryptographic methods and other changes.
- Abstraction. Components expose only the necessary interfaces and functionalities, which simplifies interactions between them and allows developers to focus on the high-level design without worrying about the intricate details of each part.
These properties allow developers to separate the cryptography code into independent modules outside of the core application code and decouple the crypto logic from the business logic in your application. This allows your team to modify, replace, and update such modules without re-implementing the whole system or disrupting ongoing operations.
Related project
Building a Microservices SaaS Solution for Property Management
Our client attracted new customers and optimized maintenance costs for their SaaS platform thanks to the Apriorit team’s assistance with migrating from a monolithic to a microservices architecture.
Step 2. Implement DevSecOps and CI/CD
In order to make your product crypto-agile, your team needs to not only be able to integrate cryptographic algorithms into your software but also to do it rapidly, securely, and reliably. This is where DevSecOps comes into play.
DevSecOps is a methodology that integrates security practices into every stage of the software development lifecycle (SDLC), from planning and coding to testing, deployment, and operations. Unlike traditional software development approaches, where security is often considered a separate phase or added as an afterthought, DevSecOps promotes a culture of shared responsibility among development, operations, and security teams.
In the context of crypto-agility, DevSecOps allows your team to integrate, test, and validate new cryptographic algorithms rapidly and securely. Couple it with the CI/CD pipeline and eliminate errors by automating the deployment and updating of cryptographic solutions across development, testing, and production environments.
In NIST SP 800-204C, you can explore more recommendations for implementing DevSecOps for a microservices architecture.
Step 3. Adopt a zero trust architecture
You can enhance your security against quantum threats right now by adopting a zero trust architecture in your software.
Zero trust is a security model that enforces strict identity verification for every user and device trying to access resources on a network rather than assuming trust based on network location or user credentials alone. Even if a quantum computer breaks your system’s traditional encryption, a zero trust architecture can help you minimize the damage by limiting access and continuously verifying trust.
To implement zero trust into your product’s architecture, you need to:
- Implement identity and access management (IAM) solutions to ensure that only authorized users and devices can access cryptographic resources and functions.
- Segment cryptographic functions and data. This involves separating cryptographic operations (the control plane) from data processing operations (the data plane), ensuring that sensitive cryptographic keys and processes are isolated and protected.
- Encrypt data at rest, in transit, and in use. Upgrade your encryption libraries to support strong, quantum-resistant algorithms so your data stays protected even if it gets intercepted.
- Implement real-time monitoring and logging of all cryptographic operations so you can rapidly detect and respond to suspicious activities related to your cryptographic systems.
- Implement security control automation by automating code reviews for security policies, integrating encryption policies into continuous integration/continuous deployment (CI/CD) pipelines, and utilizing automated threat detection mechanisms to manage your cryptographic operations more efficiently.
Step 4. Automate cryptographic keys and digital certificate management
Effective management of cryptographic keys and digital certificates is crucial for maintaining crypto-agility, as it allows you to quickly update protocols as new threats and standards emerge. Cryptographic keys and certificates ensure secure communications, and their mismanagement can lead to severe vulnerabilities.
Implementing a public key infrastructure (PKI) is a great way to structure the lifecycle management of your keys and certificates. PKI automates key generation, distribution, storage, and rotation. By using PKI, your development teams can eliminate human error and enhance the visibility of the cryptographic algorithms used in your software systems.
PKI enhances crypto-agility by allowing you to quickly adopt new cryptographic standards and algorithms, as it updates certificates and configurations centrally.
To implement PKI, your development team needs to integrate PKI software such as Microsoft Active Directory Certificate Services, OpenSSL, or commercial PKI solutions.
You can also integrate PKI with your IAM solution to enhance zero trust and your overall cybersecurity posture by confirming user or device identities based on digital certificates.
How Apriorit can help you prepare for the post-quantum future
Making your product crypto-agile and adaptable to new cybersecurity requirements is a complex process. However, it can become easier if you partner with an expert team.
Apriorit has over 20 years of experience building agile solutions for businesses of any scale and domain using a security-first approach. Our experts can help you achieve crypto-agility and prepare for post-quantum cryptography in many ways depending on your current situation and needs. We can:
- Evaluate your current cybersecurity posture. Our security testing experts, reverse engineers, and penetration testers can help you get a full picture of your product’s current security state. Our auditors can also inventory cryptographic algorithms currently in use and identify cryptography that may be vulnerable to quantum attacks. As a result, you can get a list of recommendations for enhancing your product’s protection measures.
- Develop a crypto-agility strategy. We can create a holistic concept for implementing crypto-agility for your product and create a comprehensive technical specification with clear requirements based on your needs. Our team can also help you select suitable cryptographic algorithms for strengthening your product’s protection.
- Enhance your current encryption methods. Our cybersecurity and software development specialists can also update and enhance existing or integrate new encryption, threat detection, and other protection methods into your software to make it harder for cybercriminals to harvest your data today.
- Migrate your legacy software to a crypto-agile architecture. Apriorit has helped many businesses shift from outdated or rigid architectures to more flexible environments with continued support for current clients. We can help your product expand its possibilities for better functionality and security and prepare it for future cryptographic developments.
- Build a crypto-agile system from scratch. Our engineers have experience creating products based on flexible architectures. With our help, you can get a system that can easily manage and update its cryptographic abilities without having to reimagine the core functionality. This will help you adopt PQC in the future with minimal overhead.
With our niche expertise and an extensive pool of software development experts, you can cover any cybersecurity needs and protect your product for years to come.
Read also
Internal Security Audit Checklist for Increasing Product Quality
Discover how our comprehensive internal security audit checklist can enhance your product’s quality and ensure robust security measures to gain customer trust!
Conclusion
Although the quantum threat isn’t quite here yet, it’s vital for businesses that handle sensitive data to start preparing for post-quantum cryptography applications right now.
Your software needs to be flexible enough to integrate with the newest cryptographic algorithms and methods to become quantum-resistant in the future. If you implement crypto-agility, you will be able to promptly integrate PQC algorithms as soon as they become widely available. This way, you can protect your software’s sensitive data from quantum attacks.
At Apriorit, we understand the critical importance of pre-emptive measures. By partnering with our cybersecurity team, you can be sure your solution is protected from current threats and prepared for future ones.
Need a reliable cybersecurity partner?
Benefit from our security-first approach to software development and build future-proof products!




