Application programming interfaces (APIs) allow applications to seamlessly exchange data and share functionality. However, working with APIs is not without its challenges.
Limited access to source code, cybersecurity concerns, and lack of documentation can create significant hurdles for developers and businesses. In addition, you need to ensure that your APIs won’t be compromised.
API reverse engineering can help you streamline your API management. With reversing practices, you can gain a deeper understanding of API functionalities, uncover hidden features, and develop custom solutions that help you overcome the limitations of existing APIs.
This article explores major use cases and benefits of API reversing, providing valuable tips on ethical and secure reverse engineering of third-party APIs. It will be useful for tech leaders who want to integrate with undocumented systems, optimize existing APIs, and enhance their products’ cybersecurity posture.
API reverse engineering basics and use cases
Businesses often rely on APIs to connect their applications and services, as APIs function as a bridge between software programs and allow them to seamlessly exchange data and functionality. This, in turn, allows businesses to integrate features from external providers or offer their own data and services to others. For example, an e-commerce platform might leverage an API to connect with a payment gateway, simplifying the checkout process.
However, APIs don’t always come with comprehensive documentation, and this can pose significant challenges for developers who are trying to integrate with them. Here are some of the most common issues that your team might face:
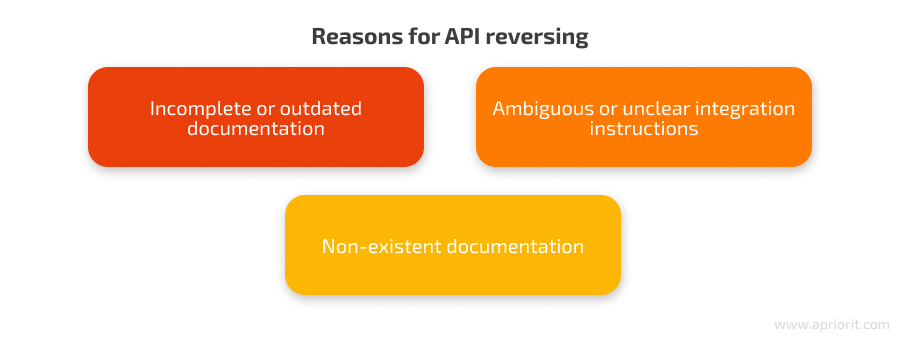
- Incomplete or outdated documentation. Even if documentation exists, features may have been added or modified since the last update, leaving developers guessing at how to interact with the API effectively.
- Ambiguous or unclear integration instructions. Sometimes, documentation is poorly written or lacks clear explanations. This can lead to confusion and misinterpretation, hindering the development process.
- Non-existent documentation. In some cases, APIs might have no official documentation at all. This leaves developers entirely on their own to figure out how the API works, significantly increasing the time and effort required for integration.
All of these issues can reduce your ability to leverage an API’s full potential and slow the speed of development.
This is where API reverse engineering comes in.
Reverse engineering an API is the process of deconstructing the API to understand its inner workings without relying on official documentation and wasting more resources. This practice often involves monitoring network traffic between the client and server to capture API calls and responses. By dissecting client–server interactions, developers can uncover details about available endpoints, data formats, and authentication methods.
This practice can also help developers understand undocumented or poorly documented APIs, allowing your team to expand or modify the existing functionality of third-party services.
When should you reverse engineer APIs?
Here are some common events where API reverse engineering proves invaluable:
- Migration to new platforms. Your team can easily migrate applications to new platforms when they understand the existing API interactions. By reverse engineering legacy systems and extracting data and functionality, you can ensure the continuity of your operations.
- Vulnerability analysis. By dissecting and analyzing an API, your developers can identify security vulnerabilities and potential attack vectors before an attack occurs. This helps you fortify your API against threats and implement robust cybersecurity measures.
- Data extraction and scraping. Your team can use API reversing to extract and scrape data from web services that do not provide direct access. This is particularly useful for gathering information for analysis or integrating data into other systems.
- API redesign and optimization. API reversing can help you create more efficient and user-friendly APIs by analyzing existing API structures and performance to identify areas for improvement.
- Compatibility testing. Reverse engineering can help you make sure that new applications or updates remain compatible with existing APIs. This prevents integration issues and ensures smooth communication between different software components.
- Workflow automation. By analyzing API calls, businesses can automate repetitive tasks and streamline workflows. This will boost productivity and reduce the potential for human error, leading to more efficient business operations.
Note: While there are many scenarios where reverse engineering an API can be extremely helpful, your team should use this practice with caution and respect for legal and ethical considerations.
Now that we have explored different use cases where you can benefit from API reverse engineering, let’s see what advantages it can bring to your organization.
Ready to unlock the full potential of your APIs?
Leverage Apriorit’s reverse engineering expertise to optimize performance and uncover new possibilities for your business.
Top 6 benefits of API reverse engineering
When you have no access to official API documentation (or such documentation doesn’t exist), reverse engineering can be of great help. By reverse engineering an API, developers can create user-friendly interfaces, integrate new features, or improve existing applications without access to the original source code or documentation.
Let’s take a look at a few major benefits of API reverse engineering for your business.
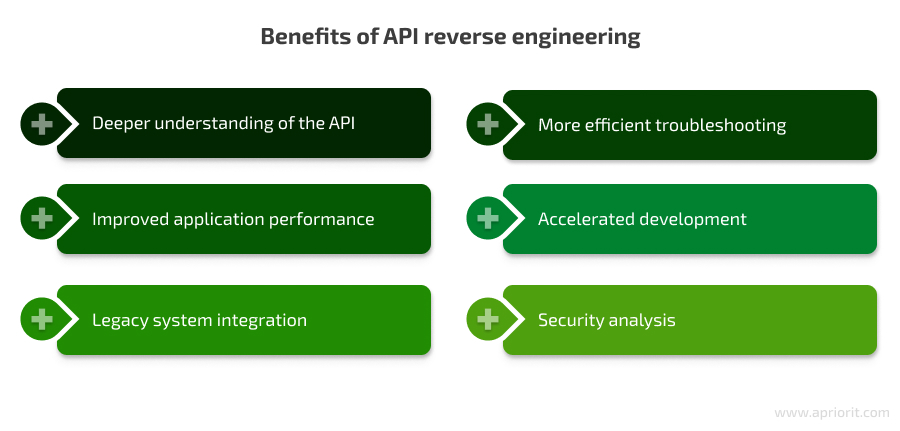
- Deeper understanding of the API. Reverse engineering goes beyond documented functionalities, allowing your team to gain a comprehensive understanding of an API’s capabilities. As a result, developers can reveal hidden features, uncover edge cases not mentioned in the documentation, and provide insights into how the API truly behaves.
- More efficient troubleshooting. Integration issues can be frustrating and time-consuming to resolve. By reverse engineering an API, developers can pinpoint the root causes of errors and bugs within the integration, leading to faster and more effective troubleshooting.
- Improved application performance. Through reverse engineering, developers can analyze the data flow and identify potential bottlenecks that reduce performance. Insights into these communication channels between apps allow your team to optimize communication and streamline integrations, resulting in a smoother user experience.
- Accelerated development. As your developers quickly grasp the necessary details of an API, they reduce the time spent on trial and error and speed up the integration of third-party services. Faster development cycles lead to a quicker time to market for new features and updates, giving your business a competitive edge.
- Legacy system integration. Since businesses often rely on a mix of old and new technologies, their legacy systems might lack documented APIs and create issues for integration with modern applications. Reverse engineering bridges this gap by allowing developers to understand how older systems function and establish connections without relying on official documentation.
- Security analysis. While not the primary focus, reverse engineering can also be used to identify potential security vulnerabilities within an API. By analyzing data exchange and authentication methods, developers can discover weaknesses that could be exploited by attackers. With these insights, you can take steps to improve API security and safeguard your sensitive data.
Let’s take a look at the best practices recommended by Apriorit specialists to ensure ethical and secure reverse engineering.
Read also
Third-Party API Integrations for Your Software: Benefits, Challenges, and Best Practices
Discover the advantages and challenges of incorporating third-party APIs into your software. Our experts share tips on optimizing your development process and enhancing your product’s functionality with third-party API integrations.

Best practices for responsible API reversing
API reverse engineering can be very effective but requires a responsible and ethical approach. Here are some best practices recommended by Apirorit experts to make sure you are using this technique effectively and appropriately:
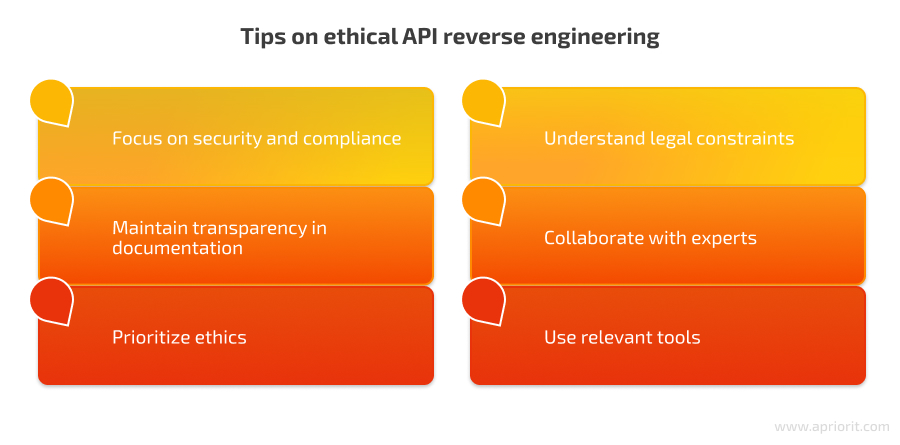
Focus on security and compliance. As you reverse engineer an API, you need to make sure that your efforts don’t compromise the integrity and security of the systems you are working with. Avoid any actions that could compromise data or violate security protocols, like brute-force attacks, scraping sensitive data, or denial-of-service attacks. You can also follow industry best practices, such as the OWASP API Security Top 10 and the GDPR, to maintain compliance.
Maintain transparency in documentation. Whenever you get new information or make a modification throughout the reverse engineering process, you need to keep detailed records. This helps you understand the API better and simplifies future maintenance or troubleshooting. However, be careful not to publish any confidential information that you uncover from the process unless explicitly permitted by the API provider.
Prioritize ethics. Always act ethically when reverse engineering APIs and respect the intellectual property rights of the original developers. Refrain from exploiting vulnerabilities or using your new knowledge to harm the API provider or its users. If you’re unsure about the legitimacy of a particular action, err on the side of caution and seek clarification from the provider.
Understand legal constraints. Copyright and intellectual property laws might restrict certain actions. Familiarize yourself with the terms of service associated with the target API, and don’t engage in any activities that could be considered a violation. Also, different countries have different laws and regulations regarding reverse engineering practices. Understanding these legal constraints helps you avoid potential legal repercussions and ensures that your project remains within legal boundaries.
Collaborate with experts. Use the expertise of professionals who have experience in reverse engineering, both in APIs and in general. This expertise will help you improve the overall quality of your project and reduce the time spent on development and maintenance. You can get support from Apriorit experts who will ensure that your reverse engineering efforts are effective and comply with industry standards.
Use relevant tools. Using the right tools for the job will help you streamline the reverse engineering process and improve the accuracy of your results. Depending on the chosen tech stack, you can analyze network traffic, decode data formats, and automate tasks.
Next, we discuss tools that have proved their efficiency in projects Apriorit engineers have taken care of.
Read also
How to Control Application Operations: Reverse Engineering an API Call and Creating Custom Hooks on Windows
Enhance your software’s cybersecurity and prevent data leaks by learning how to reverse engineer API calls and create custom hooks. Our specialists offer a step-by-step guide on using tools like Process Monitor, API Monitor, and MHook to control application operations.

Essential tools for API reverse engineering
API reverse engineering can be a complex process, but with the right instruments, it becomes more efficient and manageable. Here’s a breakdown of some essential tools Apriorit experts recommend using for your API reversing projects:
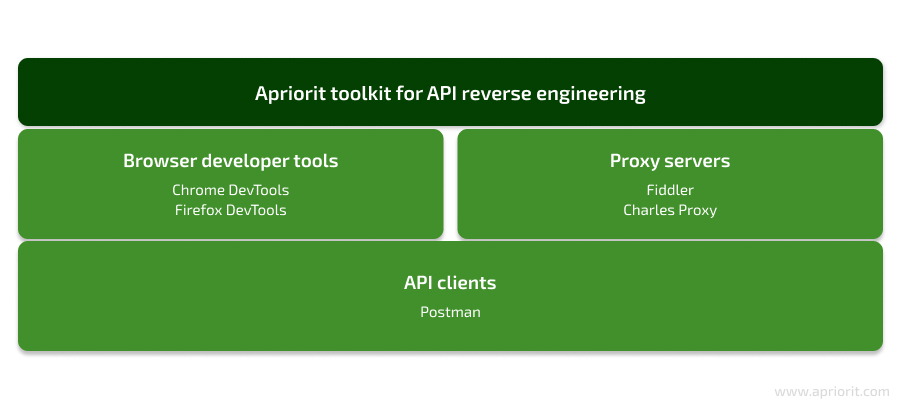
While not directly involved in core reverse engineering, there are also some instruments that can enhance the reverse engineering process:
- Swagger can be a lifesaver if you manage to unearth any existing API specifications. It helps you visualize an API’s structure, data models, and endpoints. This information can provide a solid foundation for understanding the API’s functionalities.
- SwaggerHub (an addition to Swagger) offers a collaborative platform for API design and management. For reverse engineering, its most valuable feature is the ability to generate mock servers, or stub APIs, based on API specifications. These stub APIs mimic a real API’s behavior, allowing you to test your understanding and build integrations in a safe, controlled environment.
While still under development, AI-powered tools are emerging to help you with API reverse engineering. These tools can analyze network traffic and API behavior, automatically generate documentation, and even identify potential security vulnerabilities. As AI technology matures, it has the potential to streamline the reverse engineering process even further.
The specific tools you’ll need depend on the complexity of the API and your desired outcome. A combination of these tools will allow you to reverse engineer most APIs in the most time- and cost-effective manner. Our experts can help you choose the most fitting tech stack for your project needs.
Now that you are equipped with the best instruments for the job, let’s discuss some practical examples to illustrate how API reverse engineering can be applied in real-world scenarios.
Related project
Enhancing the Security and Performance of a Virtual Application Delivery Platform
Discover how Apriorit helped Cameyo improve their platform’s performance and security and attract new users with several extra features.

Practical examples of API reverse engineering
API reverse engineering can be a valuable tool in various situations. Here, we explore how to reverse engineer an API based on two practical examples from Apriorit experts.
Scenario 1. Integrating with websites without a public API
Imagine a situation where an organization uses an extended detection and response (XDR) platform for its cybersecurity needs, but the platform lacks a public API. In such a case, reverse engineering APIs can bridge the gap and help the organization integrate XDR data with their internal systems or other security tools.
Problem: An organization wants to integrate data from a website (e.g., an XDR platform) that doesn’t offer a public API.
Solution: Using browser developer tools, you can capture and analyze network traffic between the website and the user’s browser, exposing the authentication process and data retrieval mechanisms. You can further use this information to develop a custom application that interacts with the website’s back end programmatically, essentially treating it as an API.
Here is how you can do it step by step:
- Record network traffic. Use browser developer tools to record all network traffic generated during user interactions with the website.
- Perform needed actions. Using the web interface, perform all actions you intend to program later.
- Find authentication requests. They would be among the recorded requests.
- Analyze traffic. Examine the recorded traffic to identify details like the authentication process and data retrieval requests.
- Replicate programmatically. Develop your application to replicate the authentication process and send other requests programmatically, allowing it to effectively interact with the website’s back end.
By following these steps, you can integrate with websites lacking a public API, unlocking valuable data and functionality for your own systems or applications.
Scenario 2: Replacing a real API with a stub API
Another common case where you can use API reverse engineering to your benefit is when your system is already integrated with a third-party API but there are limitations or challenges in using the real API. This could be because of frequent API changes, rate limiting, or the need to perform security audits without impacting the live system.
Problem: An organization faces difficulties using a real API due to frequent changes, rate limits, or the need for isolated testing environments.
Solution: Leverage reverse engineering to create a stub API that mimics the behavior of the real API. This stub API can then be used in place of the real one, providing necessary functionality for testing, security audits, or other purposes without affecting the live system.
Here is how you can do it step by step:
- Record API interactions. Use a proxy tool to capture all requests your application sends to the real API.
- Convert the recorded session to Open API format. Use tools like Swagger to convert recorded requests into this format.
- Generate a stub API. With the help of Swagger Hub, create a stub API based on the converted requests. After that, you can fix any minor issues in the generated code.
- Host and integrate. Host the stub API and configure your application to interact with it instead of the real API.
By following these steps, you can streamline the development process, avoid the need for frequent API updates, reduce the impact on live systems during testing or security audits, and maintain better control over the integration process.
Read also
API Management Essentials: Strategies and Tools
Empower your software with APIs that are thoughtfully built, integrated, and maintained. In this article, Apriorit experts offer insights into key strategies for auditing, updating, and securing APIs, as well as the best tools and platforms for effective API management.
How Apriorit can help you in developing secure APIs
At Apriorit, we understand the importance of developing secure and efficient APIs that meet your demands, as well as overcoming non-trivial API-related challenges. We offer a comprehensive suite of services that empower you to develop secure, efficient, and high-performance APIs.
We also know that API development needs vary depending on your specific projects and goals. Here’s how our range of services can help you throughout the API development lifecycle:
- API integration. Our team has the expertise needed to seamlessly integrate your APIs with existing systems or third-party applications. Apriorit experts work with a variety of protocols and standards to make sure that your APIs are integrated smoothly and efficiently, minimizing downtime and maximizing productivity.
- Reverse engineering. In cases where you need to work with undocumented or poorly documented APIs, Apriorit’s reverse engineering services can provide the insights you need. We can analyze existing APIs to understand their functionality and data structures, allowing you to integrate effectively or even create secure mock APIs for testing purposes.
- Web app development. APIs often power the functionality of modern web applications. Apriorit’s web development experts make sure that your web applications leverage APIs securely and efficiently, delivering a smooth experience to your users.
- Backend development. APIs rely on robust backend systems to process data and handle complex logic. Our backend development specialists create secure and scalable backend infrastructure to support your APIs effectively.
Our team prioritizes security best practices throughout the entire process, from initial design to deployment. We can also conduct thorough security testing to identify and address any potential vulnerabilities before your API goes live.
Conclusion
API reverse engineering is a powerful practice for developers who need to solve non-trivial challenges with third-party integrations. As you deconstruct APIs, you can gain a deeper understanding of their functionality, overcome challenges associated with limited documentation, and unlock valuable opportunities for integration and innovation. However, you must always follow ethical practices and prioritize security throughout the whole process.
Apriorit reverse engineering and API development and integration experts have all the knowledge and experience to help you achieve the best performance of your software. We are ready to be your trusted partner whether you need help understanding undocumented APIs, building efficient integrations, or developing secure APIs from scratch.
Don’t compromise between security and quality!
Let Apriorit experts develop secure and scalable APIs that meet the demands of your modern application.



