PCI DSS compliance is vital for any company that deals with banking data. This industry standard contains a set of 12 requirements for security controls to be implemented when developing software, processing financial data, and configuring networks. Non-compliance with this standard can cost up to $100,000 per month. In the case of repeated PCI DSS violations, a merchant may even lose the ability to accept credit cards.
In this article, an Apriorit expert discusses compliance levels and the validation process and shares a detailed guide to implementing security controls in accordance with PCI DSS. He also offers several tips on reducing the costs of compliance.
This article will be useful for banks and merchants who need to make their applications and networks PCI DSS compliant.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for financial organizations that protects branded credit cards (Visa, Mastercard, American Express, Discover, JCB) from banking fraud and data breaches. This standard was created to increase the security of cardholder data, decrease instances of data compromise, and reduce credit card fraud.
All merchants that store, process, or transmit cardholder data must be PCI DSS compliant. This is a strict requirement for working with global payment processing systems like Visa and Mastercard. Failure to comply with this standard can lead to harsh consequences. Let’s take a look at common PCI DSS fines.
Penalties for non-compliance
Fines for PCI DSS violations vary between $5,000 to $100,000 per month until the violation is resolved. The size of the penalty depends on several factors:
- The size and annual revenue of the merchant
- The severity of non-compliance and its possible consequences
- The length of time for which the merchant has been non-compliant
- Previous history of PCI DSS violations
Merchants who break this standard repeatedly may have their ability to accept credit cards revoked.
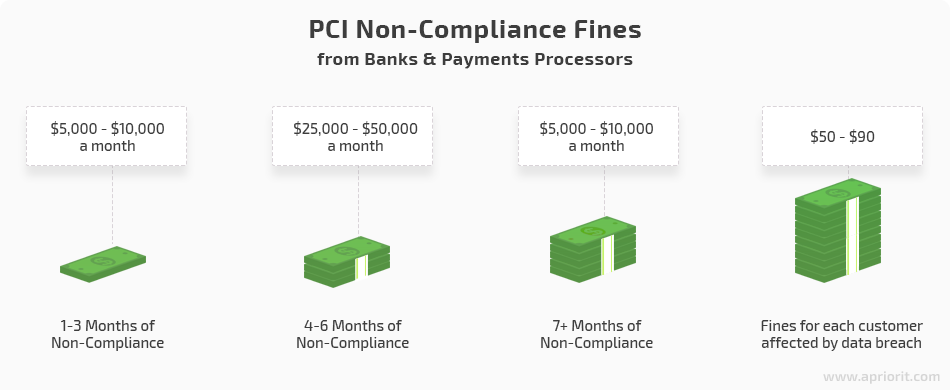
This penalty scheme also makes acquiring banks responsible for PCI DSS enforcement. That’s why banks have a right to determine how a merchant can validate compliance. There are two common ways of validating your compliance with PCI DSS:
- Filling out a self-assessment questionnaire (SAQ)
- Passing an audit performed by a Qualified Security Assessor
Unlike other security standards (e.g. GDPR), PCI DSS provides clear goals and steps for meeting the requirements. Let’s take a look at the key PCI DSS compliance levels and requirements.
Read also:
Tips on writing GDPR compliant applications
PCI DSS compliance levels
Each card brand has its own table of compliance levels, but most criteria are the same. Also, if you’ve been qualified as a merchant of a certain level by one card issuer, this qualification applies to other issuers as well.
There are 4 levels of PCI DSS compliance depending on the number of transactions you process per year.
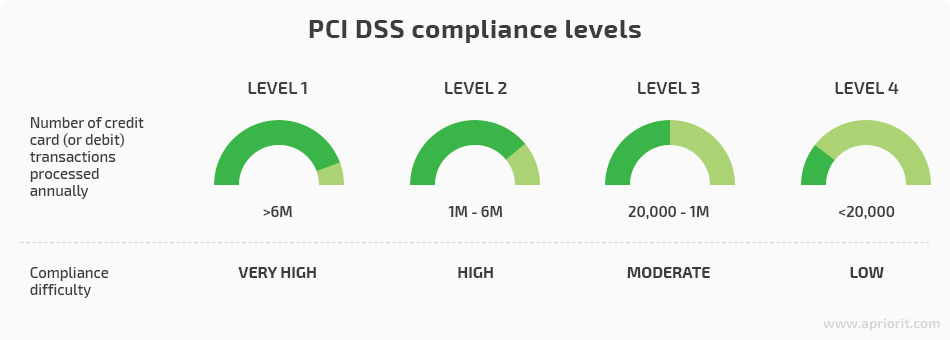
These levels determine methods of validating compliance. We’ll explain the key validation criteria for each level later in the article.
Payment systems like Visa and Mastercard have additional criteria mapped to these PCI DSS compliance levels:
- Mastercard requires merchants to comply with level 1 PCI DSS certification in case they have been hacked or involved in an account compromise event.
If you work only with Visa, you can exclude prepaid, debit, and credit card transactions from independently-owned and operated merchant locations if those transactions aren’t processed by the corporate entity.
Validation criteria for PCI DSS levels
As we mentioned, PCI DSS validation criteria depend on the merchant level. The higher your level, the stricter the security audits you need to pass. You should confirm compliance every year. These are the validation methods and processes applicable to each level:
| Method | Validation process | Affected merchants |
| External vulnerability scan | Hire an Approved Scanning Vendor to search for vulnerabilities in your internet-facing system components that have access to the cardholder data environment | All levels |
| On-site or self-assessment | Pass a security assessment by a PCI DSS certified Qualified Security Assessor or a certified Internal Security Assessor | Levels 1 and 2 |
| Self-assessment questionnaire (SAQ) | Conduct an internal security assessment using a PCI DSS questionnaire | Levels 2, 3, and 4 |
Using a self-assessment questionnaire (SAQ) is the most popular method of ensuring PCI DSS compliance. It fits all Level 2–4 merchants and can be done by your employees.
A SAQ consists of two components:
- A set of questions based on PCI DSS requirements for a particular type of service provider and merchant
- An Attestation of Compliance or certification that confirms you have performed the appropriate self-assessment
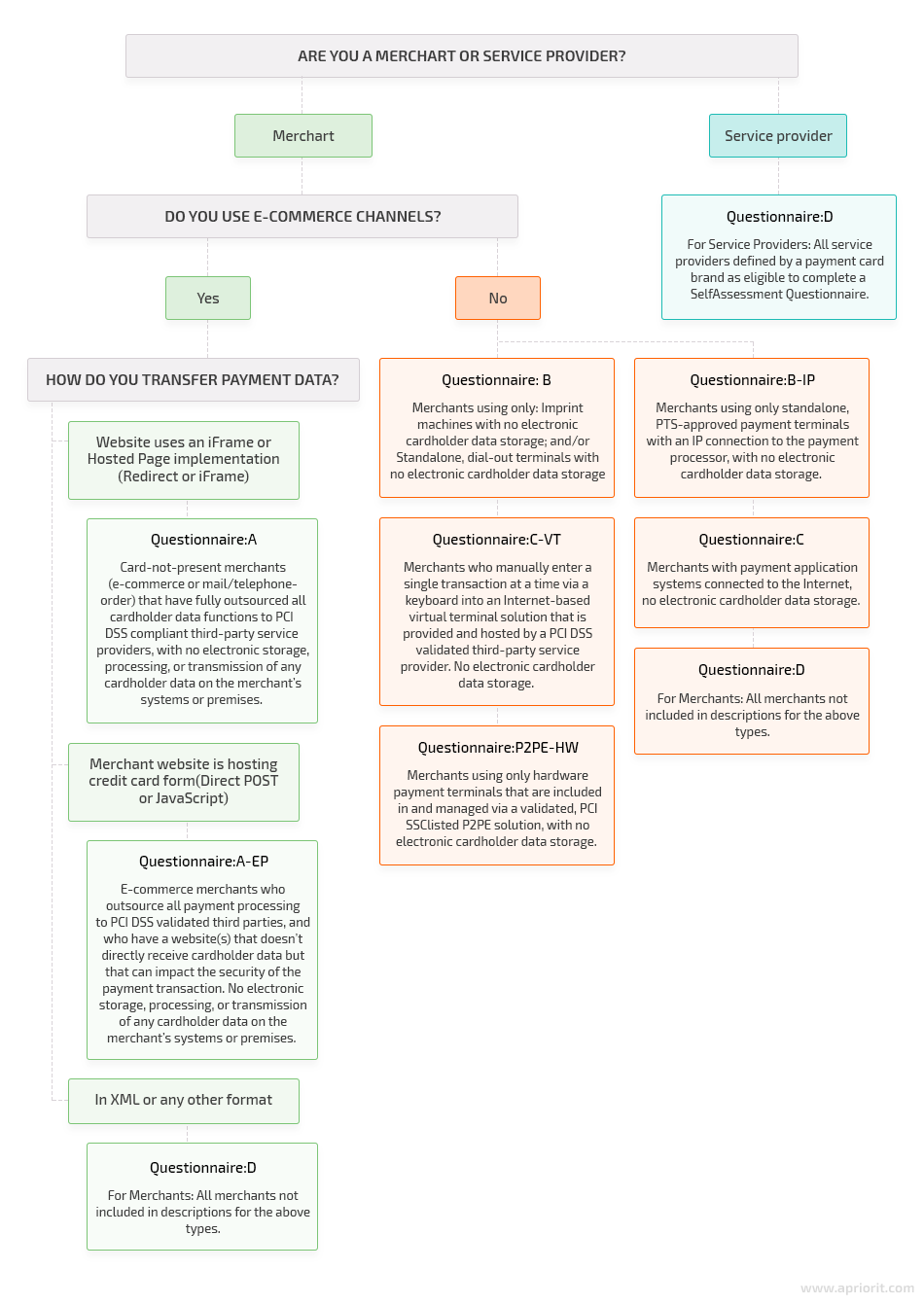
There are nine official questionnaires issued by the PCI Security Standards Council. Which you should use depends on the type of your company (merchant or service provider) and the way you transfer payment data. Take a look at our cheat sheet on choosing the right questionnaire:
PCI DSS goals and requirements
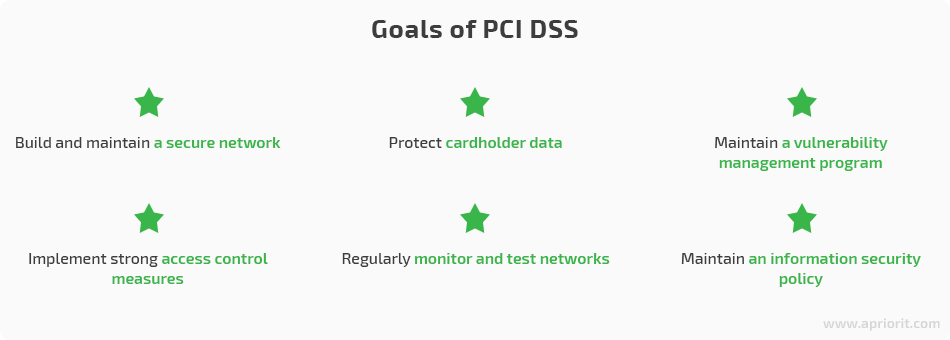
PCI DSS outlines six cybersecurity goals and sets twelve requirements that help to achieve them and maintain the security of payment data processing.
Let’s find out more about the goals and requirements of PCI DSS and steps you can take to make your company comply with those requirements.
1. Build and maintain a secure network
Securing the network is one of the key data protection procedures. The first thing you need to do is install, configure, and maintain a firewall. The payment card data security standard recommends doing it this way:
- Create a formal process for approving and testing all changes to network connections and firewall rules
- Create a diagram of current network connections used to transfer cardholder data and keep this diagram up to date
- Create a diagram of cardholder data flows across systems and networks and keep it up to date
- Create a firewall configuration standard
- Review firewall and router rules every three months
- Create firewall deny rules for unused services and protocols
- Store cardholder data in an internal demilitarized zone, separated from untrusted networks
- Install firewall software on portable devices connected to the environment with cardholder data
While creating a network, it’s important that you don’t use vendor-supplied defaults for system passwords and other security parameters. Those credentials and settings are known to everyone, including hackers. While working on network security parameters, make sure you:
- Create your own configuration standard and use it for configuring new systems
- Change all vendor-supplied passwords in all software
- Remove all default accounts in all software
- Change encryption keys and credentials for critical services every time an employee that knows this information leaves the company or changes position
- Implement password and key rotation
- Update Simple Network Management Protocol community strings on access points
- Change passwords on access points after installation
- Use the latest versions of access point firmware
- Disable weak protocols on access points (e.g. WEP)
- Disable unused services, protocols, daemons, etc.
- Use only one primary function for each server (one server should host only one critical application)
2. Protect cardholder data
Cardholder data is a pot of gold for a lot of hackers. That’s why it’s vital to ensure the protection of this information both inside a corporate network and within any applications with internet access.
PCI DSS contains a strict set of actions for protecting stored cardholder data:
- Create a data retention and disposal policy
- Remove the customer’s magnetic card strip data after authorization
- Remove CVV and PIN codes from temporary storage after authorization
- Allow only authorized employees to view full payment card numbers
- Store payment card numbers in an encrypted format
- Store cardholder data on encrypted disks
It’s also important to encrypt cardholder data transferred across public networks. You can do this by using the latest version of the Transport Layer Security protocol for cardholder data transmission and by disabling weak cipher suites.
3. Maintain a vulnerability management program
A vulnerability management program is part of the cybersecurity system that scans a network for security issues and helps to prioritize and plan their mitigation. The first critical step of vulnerability management is to use and regularly update antivirus software:
- Install and regularly update antivirus software
- Enable periodic software scans
- Enable automatic software updates
- Make sure that only authorized personnel can uninstall or disable antivirus software
The second step of vulnerability management is to develop and maintain secure systems and applications:
- Install the latest security patches and firmware
- Perform code security reviews
- Implement change review procedures
- Implement a rollback mechanism
- Perform security impact analysis
- Remove all test data from your applications before release
- Don’t use real cardholder data for testing purposes
- Conduct trainings on secure coding for developers
- Add static code analysis tools to the CI/CD pipeline
- Perform regular security assessments of your applications
- Install and properly configure web application firewalls
4. Implement strong access control measures
Access control is a set of security practices aimed at granting access to sensitive data only to employees with relevant access permissions. The following are ways to restrict access to cardholder data:
- Develop an access control policy and implement the principle of least privilege
- Implement role-based access control for all critical services and data storages
- Document all access requests
- Use the “deny-all” access level as the default for all systems
Secondly, identify and authenticate access to system components:
- Assign a unique ID to each person with computer access
- Check that all actions with users IDs and permissions can be performed only by authorized persons
- Deactivate all accounts of terminated employees
- Deactivate all accounts that have been inactive for the last 90 days
- Monitor accounts of third-party vendors
- Implement account lockouts after five failed login attempts with a cooldown period of at least 30 minutes
- Configure the session timeout for all services according to their priority
- Implement multi-factor authentication for all high-priority and critical services
- Use a strong password policy
- Enforce password rotation every 90 days
Alongside digital protection measures, don’t forget to restrict physical access to cardholder data. You can ensure reliable protection with this set of actions:
- Implement access control and/or audio and video surveillance for physical areas where cardholder data is stored
- Check that physical access to hardware, data storages, and network devices is restricted
- Use additional identification methods (badges, electronic access cards) for granting access to controlled physical areas
- Restrict the use of flash drives and portable storage devices within environments with cardholder data
- Create a list of all devices in use or connected to devices for cardholder data processing, storage, or transmission and keep this list up to date
- Periodically inspect devices for tampering or substitution
- Document all approved tampering or substitution for each device
- Destroy media drives that are no longer in use
Read also:
How to Make Accounting Software: Core Characteristics, Architectural Components, and Features
5. Regularly monitor and test your network
After you’ve configured network security and established procedures for access control, data protection, and vulnerability management, it’s important to maintain this level of security. Here’s a list of activities that will help you track and monitor all access to network resources and cardholder data:
- Enable audit trails for system components
- Log all events involving access to cardholder data, actions with audit trails, and actions taken by users with administrative privileges
- Check that each audit trail event has at least the following entries: user ID, type, date and time, name of the affected component, event origin, and result (success or failure)
- Check that the clock on all critical systems is synchronized and can’t be changed by employees without root permissions
- Log all changes in the time settings
- Check that audit trails are secured from alteration by employees or malware
- Implement regular monitoring with defined response time objectives for anomalies in audit trails
- Create written procedures for processing and analysis of security anomalies
- Store audit trails with all events for the last year and enable immediate access to data from the last three months
Furthermore, you need to regularly test security systems and processes. PCI DSS recommends that you:
- Create a detection and identification procedure for wireless access points and repeat this procedure each quarter
- Create an incident response plan for situations when unauthorized access points are detected
- Perform internal and external network vulnerability scans every 3 months and after significant changes to the network infrastructure
- Perform internal and external application vulnerability scans every 3 months and after significant changes are made to the application
- Perform regular external and internal penetration testing of the network infrastructure and applications
- Mitigate all found vulnerabilities ranked higher than 4.0 on the Common Vulnerability Scoring System
- Use intrusion detection and intrusion prevention solutions for traffic monitoring
- Use change detection solutions for critical systems and network devices
- Configure alerts for security events from IDS, IPS, or change detection solutions
Read also:
What is Impact Analysis in Software Testing?
6. Maintain an information security policy
An information security policy is a compilation of other policies, technologies, and procedures that define an organization’s cybersecurity system. It’s important to maintain a policy that addresses information security for employees and contractors to ensure that everyone understands why it’s important to follow the outlined procedures. Here’s a to-do list that will help you achieve this:
- Create a set of security policies and share them with all employees
- Review security policies annually
- Create an annual risk assessment process
- Create, distribute, and maintain an information usage policy
- Establish a security awareness program
- Check that your security policy covers interactions with service providers
- Create incident response and business continuity plans
- Set procedures for security breach mitigation
- Assign personnel responsible for reacting to alerts
Reduce the cost of PCI DSS compliance
Complying with PCI DSS standards requires implementing a lot of cybersecurity solutions and procedures. Passing an audit, even if it’s a self-audit with a questionnaire, can be quite costly. Though cutting expenses on security can lead to harsh consequences, there are several ways to lower the cost of PCI DSS compliance without risks:
- Cut down the PCI DSS scope. The easiest way to cut costs is to change the way your application processes payment data, which will result in changing the required questionnaire. Say you have an application that receives payment data from the customer, stores it, and then sends it to a third-party payment processing company. In this case, you will be required to satisfy SAQ D, which contains PCI DSS requirements for service providers. However, if you redirect your customers to a PCI DSS validated payment processing system and customers don’t enter payment data on your website, you will be required to complete SAQ A, which is easier to comply with.
- Use infrastructure from a PCI DSS managed service provider. One of the most complex PCI DSS requirements is building a protected network and ensuring the security of data in transit. You can avoid responsibility for this by employing a PCI DSS compliant cloud infrastructure like AWS or Microsoft Azure. These are the three most common types of PCI DSS compliant hosting setups:
- Co-location. Host your hardware at the data center provider. This way, the provider is responsible for hardware security and you’re responsible for network security.
- Basic IaaS. You’re responsible for the security of application cardholder data and the IaaS provider restricts physical access to that data.
- Advanced IaaS. The provider is completely responsible for secure data handling and PCI DSS compliance.
- Perform an internal audit before certification. SAQs contain lists of clear requirements with which you should comply. You can save time and money by running a preliminary internal audit and checking whether you meet these requirements before you actually contact a Qualified Security Assessor.
Apriorit can help you run such an audit quickly and efficiently. We have vast experience in:
- Building secure network infrastructure for many types of applications
- Developing PCI DSS compliant applications
- Conducting preliminary audits of existing infrastructure
- Consulting on how to improve infrastructure to meet PCI DSS requirements
Conclusion
Becoming PCI DSS compliant is an obligatory but complex procedure for any organization that processes credit card data. The PCI DSS standard verifies that a company uses the best cybersecurity practices and can be trusted by customers and business partners.
PCI DSS offers a set of cybersecurity requirements, compliance levels, and validation procedures. Though all requirements are well-defined, the first PCI DSS assessment can be tricky even for an experienced security team. Also, annual recertification is a time-consuming process.
At Apriorit, we have vast experience in cybersecurity and data processing. Contact us to discuss how to make your applications and networks PCI DSS compliant in the fastest and most efficient manner!



