Healthcare organizations are among the most frequently breached by cyberattacks, and the number of cybersecurity incidents is growing by the year. The Verizon 2020 Data Breach Investigation Report records 512 healthcare breaches in 2019 compared to 304 in 2018.
To counter the growing cybersecurity threat, medical organizations search for software with more and more elaborate data protection measures. In the US, such software has to comply with the Health Insurance Portability and Accountability Act (HIPAA), which describes must-have security mechanisms to protect health information against theft and leaks. Developing a solution with all HIPAA requirements in mind is challenging, however, as HIPAA mandates the use of a variety of cybersecurity best practices.
At Apriorit, we’ve successfully delivered many medical and healthcare IT projects with HIPAA compliance. In this article, we’ll discuss the importance of HIPAA compliance in healthcare and how to check the compliance of your IT product.
HIPAA: definition and scope
HIPAA is a US federal law that helps healthcare organizations keep their security up to the best standards and prevent data breaches. There are four types of companies that have to treat healthcare information in compliance with HIPAA requirements:
- Healthcare providers — Organizations that provide medical services, including clinics, hospitals, pharmacies, labs, and psychiatric facilities
- Healthcare plans — Insurance and health maintenance companies, government and private medical programs
- Healthcare clearinghouses — Organizations that aren’t involved in healthcare services but work with protected health information (PHI) or electronic PHI (EPHI), such as aggregators and hubs for transmitting medical data
- Business associates — Subcontractors of healthcare organizations that process PHI and therefore share the same responsibilities as healthcare organizations
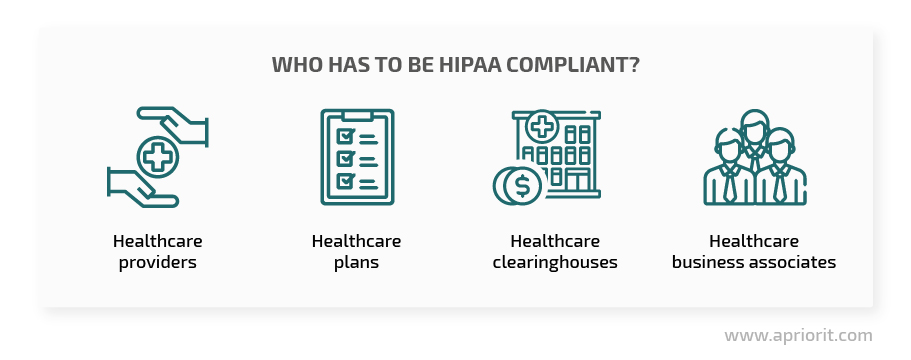
All IT solutions developed for an organization from the list above have to comply with HIPAA requirements in order to secure electronic protected health information (EPHI).
EPHI is any identifiable electronic data on a patient’s physical or psychological health, treatment plans, provided healthcare services, or payments for such services. EPHI also includes any personally identifiable information. HIPAA requires software developers to protect:
- Access to EPHI — Provide time-based access only to users with relevant rights and alert such users upon accessing sensitive data
- Data in storage — Encrypt stored data and secure storage with physical and digital protection measures
- Data in transit — Create secured transit channels and encrypt data in transit
Non-compliance with the demands of this act may lead to data disclosures and severe punishment for both the organization and individuals responsible for an incident. That’s why developers spend a lot of effort designing their software with HIPAA in mind and verifying compliance before a product is released.
Let’s take a closer look at possible penalties for breaking HIPAA rules.
Penalties for violating HIPAA requirements
Implementing cybersecurity requirements defined by HIPAA protects an organization from both data breaches and stiff fines from the US Department of Health and Human Services (HHS). For the most severe violations, HIPAA carries punishments of up to $1.5 million in fines or 10 years of imprisonment.
HIPAA penalties are adjusted each year. The last major adjustment happened in April 2019, when calendar year penalty caps for most HIPAA violations were significantly reduced.
Here’s an overview of the major types of violations and associated penalties:
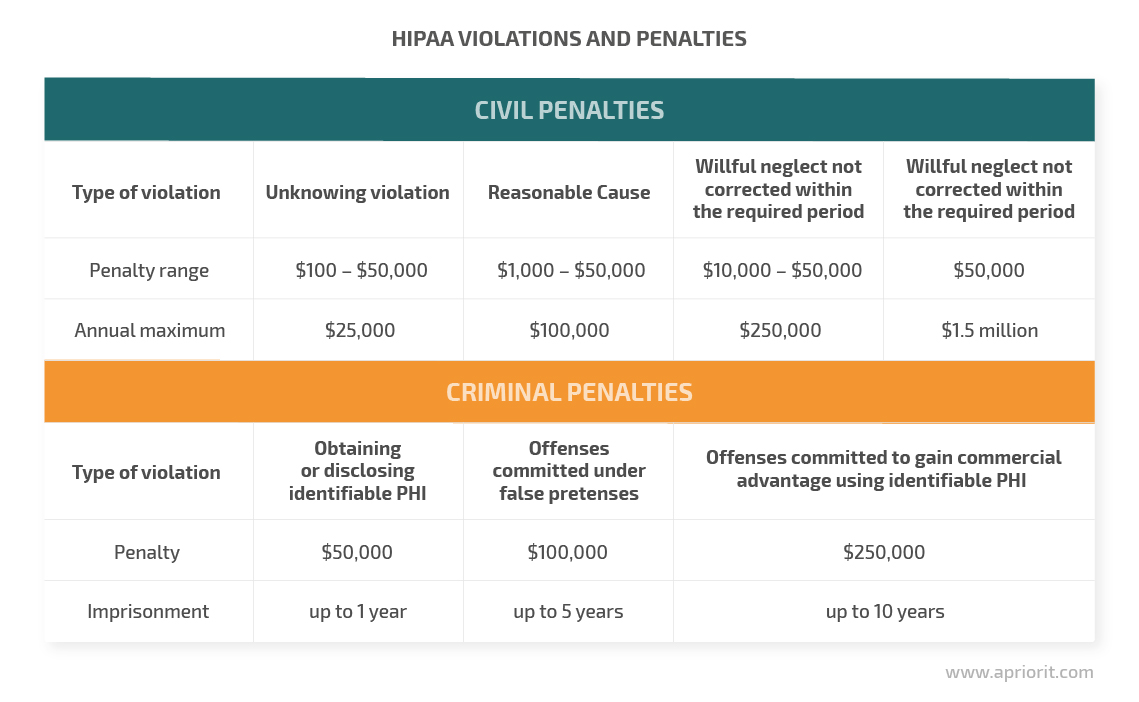
As you can see, violating HIPAA requirements can lead to severe losses and reputational damage. However, complying with this act is also challenging. Let’s take a look at its key rules and challenges of implementing HIPAA for protecting health information.
Challenges of developing a HIPAA-compliant solution
HIPAA requirements are laid out in five complex rules. They describe all security-related procedures that healthcare organizations should implement, from physical office security to the breach notification process.

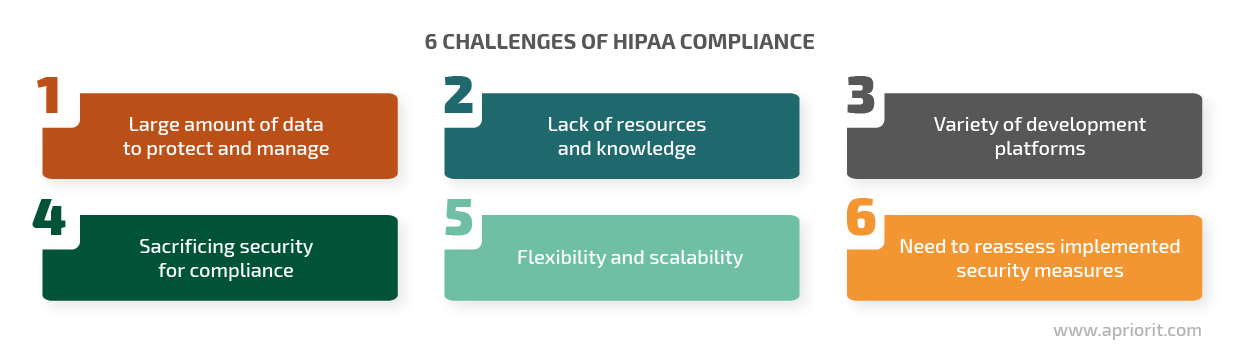
To verify compliance, many developers check their solutions for all needed security tools before release. However, a perfect development cycle is not always possible. Here are the key challenges developers encounter when creating a HIPAA-compliant application or system:
- Too much data to protect and manage. Before implementing any sort of data protection, developers have to get a clear understanding of the amount, nature, and layout of sensitive information. In healthcare organizations, evaluating such data is particularly complex, as it’s stored in numerous locations: electronic health record (EHR) systems, data centers, physical storage locations, mobile devices, supply chains, vendor environments, etc.
- Lack of resources and knowledge. Creating and deploying a HIPAA-compliant solution involves lawyers, cybersecurity experts, medical experts, and DevOps engineers. All of them need to contribute deep knowledge and lots of time to the project; otherwise, the solution won’t cover all the requirements. Budget cuts and acceleration of product development often result in insecure and non-compliant software.
- Variety of development platforms. All platforms used in a healthcare organization have to be protected with the same security measures. Modern hospital infrastructure includes real and virtual user endpoints, servers, data centers, mobile devices, cloud resources, and more. An IT team needs knowledge of and experience with mobile device management architecture design and development for all of these platforms to secure sensitive data.
- Sacrificing security for compliance. While implementing HIPAA requirements surely improves software cybersecurity, it isn’t a silver bullet. Some development teams check the boxes and think they can skip a risk assessment. However, such an approach leads to data breaches and penalties. To protect a software product, developers have to critically evaluate possible threats and risks and implement as many security measures as they can, paying attention both to required and addressable measures.
- Flexibility and scalability. Systems developed with many security requirements in mind are usually quite rigid. At the same time, healthcare organizations need flexible software to be able to adapt to changes. During the design stage, developers have to take into account software scalability and flexibility to meet needs that may arise in the future.
- Need to reassess implemented security measures. Work on a healthcare system doesn’t stop when it’s deployed. HIPAA requirements, cybersecurity threats, and an organization’s IT environment are all constantly changing. To make sure your software remains HIPAA-compliant, developers have to conduct regular audits, carry out risk assessments, and update documentation and security policies.
At Apriorit, we’ve developed dozens of HIPAA-compliant solutions for healthcare, tackled many challenges, and accumulated unique experience on this subject. To speed up the verification of all required IT measures, we’ve created an internal security audit checklist that we’d like to share with you.
Checklist for verifying HIPAA compliance
Standards for IT systems and EPHI protection are laid out in the HIPAA Security Rule. It contains a set of administrative, physical, and technical safeguards. The list of measures mandated by the Security Rule includes:
- Access control and management
- User authentication
- Data integrity control
- Controls for conducting audits
- Management of patients’ complaints of security violations
- Encryption
- Security for data in transit
- Security policies for incident detection, response, and contingencies
- Security awareness training
To verify that your solution or security system corresponds with all HIPAA requirements, use this HIPAA compliance checklist for healthcare:
| Requirement | Type of requirement | Desired outcome |
| Data backup
§164.308(a)(7) | Required | The software creates backups of all protected medical information it processes. It’s possible to restore all data in case it’s lost or corrupted in the main storage. |
| Unique user identification
§164.312(a)(2)(i) | Required | All users with access to EPHI have unique identifiers. |
| Access restriction
§164.308(a)(4) | Required | Users have the minimum access level necessary to perform their duties. There are several levels of access to sensitive data. |
| Protection against deletion
§164.308(a)(7)(ii) | Required | Data is protected from unauthorized deletion. The system that protects data is audited regularly. |
| Data disposal
§164.310(d)(2)(i) | Required | Software is equipped with a data disposal mechanism that makes restoring deleted data impossible, both on usable and non-usable devices. |
| Patients’ right of access
§164.524 (a) (1) | Required | A mechanism or procedure allows patients to access their personal EPHI. |
| Encryption
§164.312(e)(1) | Addressable | All stored medical records are encrypted with a reliable cipher. |
| Person or entity
authentication §164.312(d) | Addressable | The software forces users to authenticate to access EPHI. |
| Data transmission
§164.312(e)(1) | Addressable | Encrypted EPHI is transmitted only via secure encrypted connections. |
| Access control for terminated users
§164.308(a)(3) | Addressable | The software allows security officers to deactivate user profiles for inactive users. |
| Access control for inactive users
§164.312(a)(2)(iii) | Addressable | The software logs inactive users off automatically. |
| Log-in monitoring
§164.308(a)(5)(ii) | Addressable | A system records all log-in attempts, both successful and failed. |
| Data storage
§164.310(d)(2)(iv) | Addressable | Unauthorized access to EPHI stored inside the organization is impossible. |
| Assigned security responsibility
§164.308(a)(2) | Addressable | The organization has a document that clearly explains the responsibility for unauthorized use or disclosure of EPHI. |
Note: The requirements discussed above describe only IT controls for data protection. To achieve full HIPAA compliance of healthcare products, you also need to comply with administrative and physical controls.
Conclusion
Implementing all the cybersecurity mechanisms required by HIPAA is time-consuming and challenging, but those requirements protect healthcare companies from data breaches and thus help them avoid severe penalties.
At Apriorit, we have vast experience developing and testing software that meets HIPAA requirements. We also have audit checklists for software development of various products. In this article, we’ve shared a small part of our experience on how to protect and secure protected health information. Our experts can do much more than that. We can develop a HIPAA-compliant solution from scratch, test an existing solution, and analyze and verify the compliance of your system.
If you need software that meets all HIPAA requirements, contact our team!


