Man-in-the-middle (MITM) attacks are a serious cybersecurity issue, especially in the IoT field where attackers use them to break into networks and intercept data. Both individual users and companies can be vulnerable to such attacks, since we all use lots of network-connected devices.
To mitigate MITM attacks and minimize the risk of their successful execution, we need to know what MITM attacks are and how malicious actors apply them. Also, penetration testers can leverage tools for man-in-the-middle attacks to check software and networks for vulnerabilities and report them to developers. Thus, developers can fix a product’s weak spots, preventing possible MITM attacks from real cybercriminals.
In this article, we discuss MITM basics: what these attacks are and what they are intended for. We’ll see what happens during each stage of an MITM attack and explore the functionality, pros, and cons of several popular utilities for executing MITM attacks.
This article isn’t a guide on how to perform an MITM attack, but it explains how using MITM tools can help pentesters detect vulnerabilities.
MITM attacks: definition and consequences
What is a man-in-the-middle attack?
A man-in-the-middle (MITM) attack is a cyberattack where malicious actors secretly relay and possibly alter the communications between two parties who believe they are directly communicating with each other.
For instance, attackers can switch a connection between a victim’s computer and a server (a website, service, or any other network resource) to a connection where an attacker is an intermediary between the service and the victim.
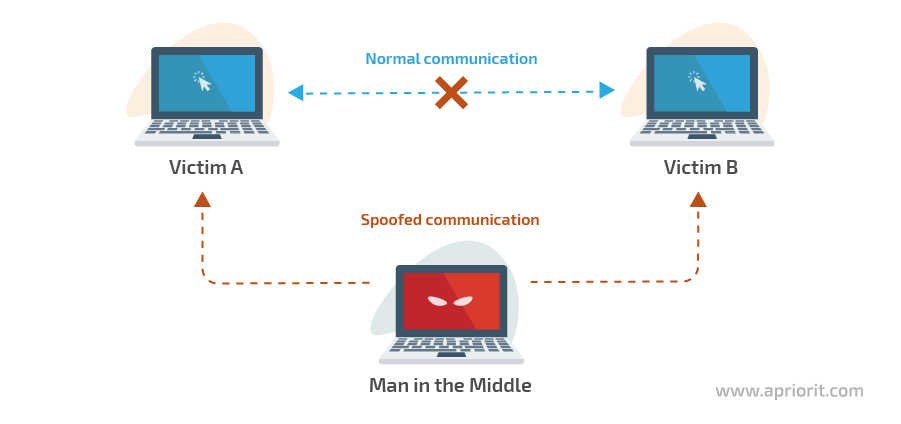
Image 1. Scheme of an MITM attack
The goal of an MITM attack is to gain access to a user’s personal data or the data of some resource a user accesses. If a user accesses an organization’s resources, an attacker can potentially access any data that’s stored and circulated within the organization’s network, such as banking data, user credentials, photos, documents, and messages.
The most common victims of MITM attacks are web resources that operate with large amounts of data: websites of financial organizations, SaaS resources, e-commerce sites, and other services that require online authorization.
The danger behind MITM attacks
What are the consequences of MITM attacks?
The consequences of a successful MITM attack can lead to both financial and reputational losses for a business.
Intercepted data provides malicious actors with an opportunity to blackmail people or purchase goods at somebody else’s expense. Also, attackers can use a victim’s credentials to harm a company: for instance, by installing malware to steal data from a corporate network.
A common intent behind MITM attacks is money theft. In 2015, 49 suspects were arrested in different European countries on suspicion of using MITM attacks to sniff out and intercept payment requests from emails. The investigation uncovered an international fraud scheme totaling €6 million, or about $6.8 million.
In 2019, hackers managed to rip off an Israeli startup by intercepting a $1 million wire transfer from a venture capital firm. Malicious actors performed an MITM attack, intercepting and editing each email from both sides and registering fake domains to fool both parties.
Cybercriminals used social engineering and managed to plant malware onto the targeted companies’ networks. Using this malware, they conducted numerous MITM attacks by intercepting e-payment transactions.
How knowing types of MITM attacks will help you enhance software testing
How can you prevent man-in-the-middle attacks?
In risk assessment and penetration testing, the main goal of using man-in-the-middle attack tools is to find and fix vulnerabilities in software and networks. Quality assurance (QA) engineers use MTM utilities to test potentially vulnerable parts of software once they’re fully developed. Then developers can fix the discovered issues and enhance the product’s security, preventing potential MITM attacks performed by real attackers.
The utilities described in this article can be used not only for performing attacks but to test network and software security. Checking your product’s protection with MITM tools helps you find vulnerabilities that malicious actors can exploit to steal data and cause both financial and reputational losses.
Such MITM tools are especially useful for IoT device manufacturers, since they help them check how secure the connection is between various devices within one network as well as the security of connections between devices and servers. As a result of thorough penetration testing, manufacturers can produce quality devices that are protected from unauthorized access.
Imitating MITM attacks helps QA specialists better understand possible attack scenarios, analyze their causes, and come up with countermeasures.
Read also:
IoT Toys: A New Vector for Cyber Attacks
How an MITM attack works?
MITM attacks consist of two major steps: interception and decryption. Each has its own substeps. Let’s briefly explore the most common.
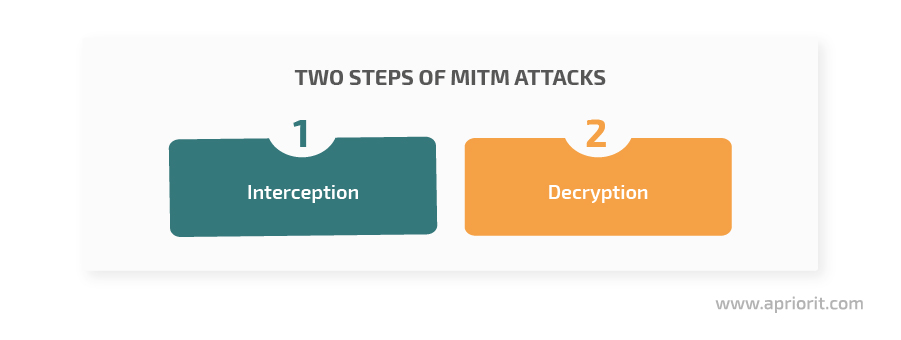
1. Interception can be accomplished using a passive or active attack:
1.1. Passive attack. Cybercriminals create an access point to a network that allows them to connect to the network via the internet. When a victim connects to the network, the cybercriminals receive full access to and control over the victim’s dataflow.
1.2. Active attack. This method includes various spoofing techniques:
- IP spoofing – Substituting a target IP address for an attacker’s address; sending a victim to a fake site instead of the original
- ARP spoofing – Substituting the MAC address to which the victim is sent for an attacker’s address in the victim’s APR table. Thus, when the victim sends data to a node, the data will be sent to the address of the attacker.
- DNS spoofing – Hacking a DNS server, DNS cache poisoning, and replacing specified addresses. In this case, the victim is directed to an attacker’s address.
2. Decryption
After intercepting data, attackers decrypt it in a way that neither the server nor the client notice an interruption. Here are a few of the methods malicious actors use for these purposes:
- HTTPS spoofing – Also known as a homograph attack, HTTPS spoofing is when the characters in the target domain are replaced with other non-ASCII characters that are very similar in appearance. This attack exploits Punycode — a standard that allows for registering domains in non-ASCII formats. To carry out such an attack, a cybercriminal registers a domain that looks just like a target site and registers an SSL certificate, making the fake website look legitimate and secure. Then, the attacker sends a link to the fake website to a victim, who thinks they are working with a protected site.
- SSL BEAST – This type of attack injects malicious JavaScript code into a session, which helps an attacker gain access to the site’s cookies. This compromises the encryption mode, so a cybercriminal receives decrypted cookies and authentication keys.
- SSL hijacking – With SSL hijacking, a valid computer session is exploited to gain unauthorized access to information or services in a computer system. The majority of web applications use a login mechanism that generates a session token to use later without the need to type in credentials on each page. With SSL hijacking, an attacker uses sniffer tools to intercept traffic and identifies the user’s token to send requests to the server instead of to the user.
- SSL stripping – An SSL stripping attack takes advantage of the way most users come to SSL websites. Under regular circumstances, when a user connects to a secured website, the connection is established in the following way:
- Connect to the website’s HTTP version
- Redirect to the HTTPS version
- Connect to the HTTPS version
- Server shows a security certificate that proves the site is legit
- The connection is established
However, during an SSL stripping attack, a malicious actor replaces steps two and three, so all the client’s data is transferred through the attacker’s node.
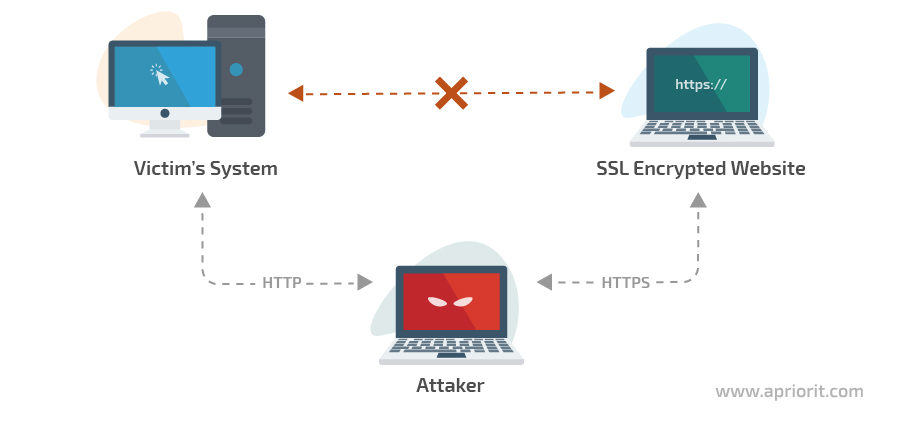
Image 2. Scheme of an SSL stripping attack
Now, let’s move to the types of tools used by attackers to perform man-in-the-middle attacks and explore several examples.
Classification of MITM tools
There are numerous tools for conducting man-in-the-middle attacks, so in this article, we’ll focus only on several of the most popular.
Let’s categorize these tools depending on the Open Systems Interconnection (OSI) model layers where they’re used.
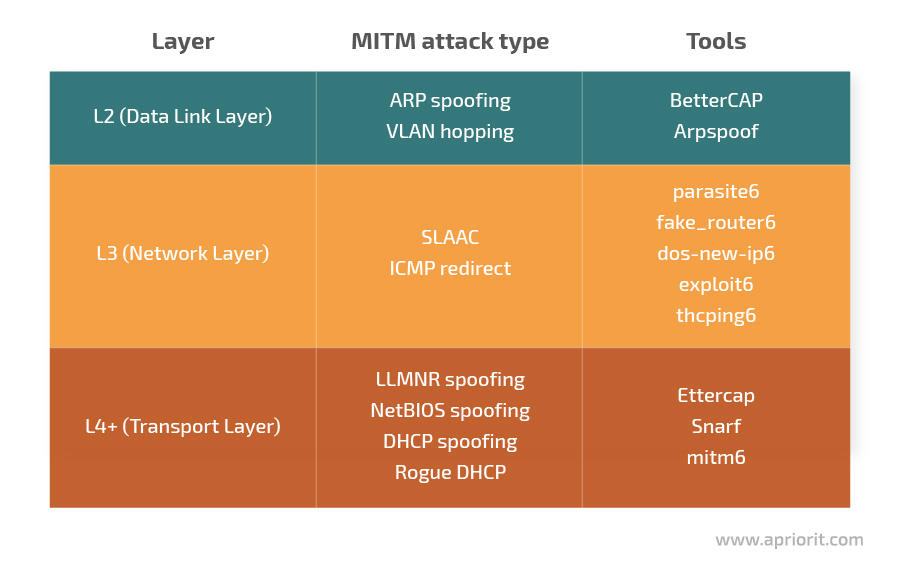
Image 3. MITM attack types and tools depending on the OSI model layer
1. L2 (Data Link Layer)
In this layer, the most common attacks are ARP spoofing and VLAN hopping. The first we’ve already explored above. Let’s briefly discuss the latter.
VLAN hopping. Data packets in VLAN networks have specific markings to make it clear which packet belongs to which subnetwork when they are passing through a switch. Cybercriminals perform VLAN hopping attacks using one of two methods:
- An attacker connects to a network and starts imitating a switch’s work so they can establish a connection with a network switch. Thanks to this connection, data packets will pass through the attacker’s computer before making it to the switch.
- An attacker adds additional markings to data packets. Switches inside the network remove their own markings and send the packets further. Meanwhile, an attacker intercepts packets with additional markings. This method will work if an attacker is connected to the main switch in the network.
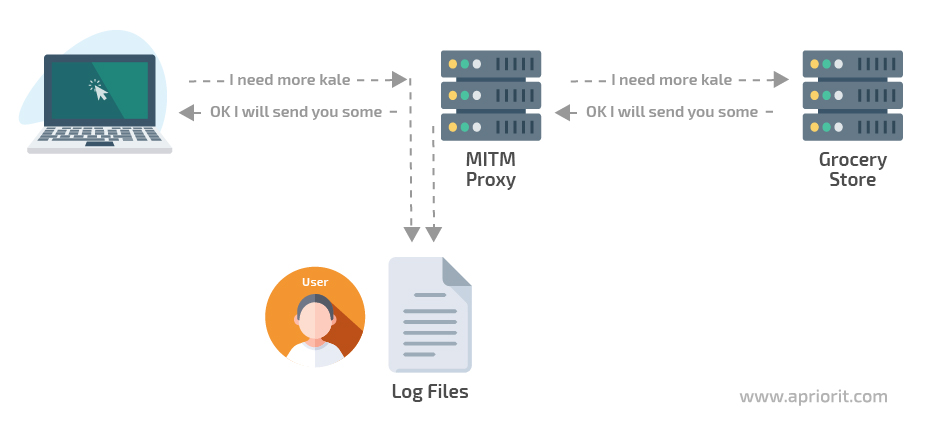
Image 4. Data extraction scheme in the majority of command-line tools
Now, let’s explore tools used for such attacks.
BetterCAP is a powerful tool with flexible settings that’s created for:
- Conducting various MITM attacks
- Manipulating HTTP, HTTPS, and TCP traffic in real time
- Sniffing a network to find data for authentication
- And more
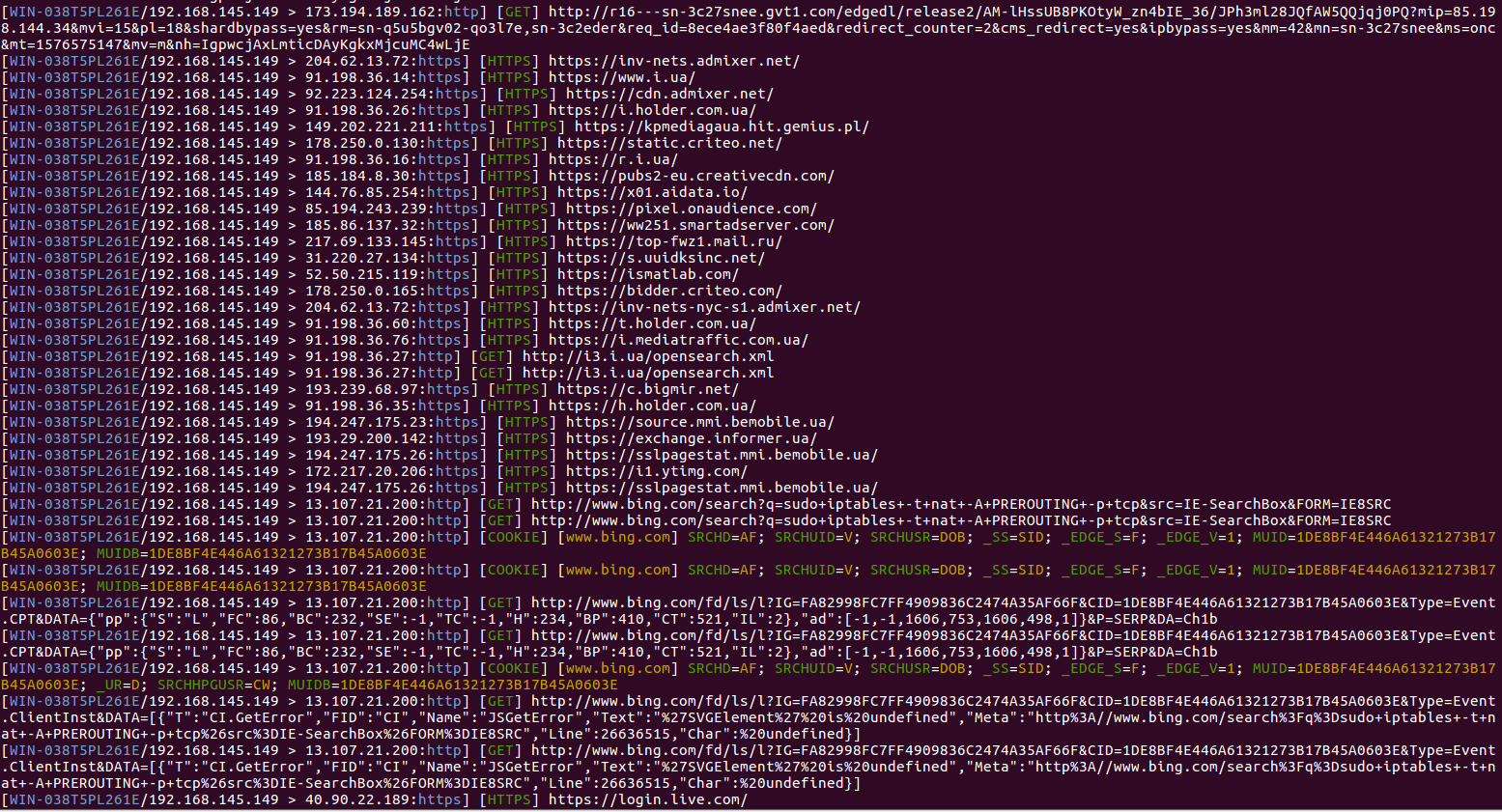
Image 5. Unfiltered data flow received through the BetterCAP utility
Professional pentesters have been choosing BetterCAP starting from its very first versions. Developers of mobile devices and software as well as researchers in the IoT field leverage the utility’s ability to test device security.
One of the most convenient features of BetterCAP is the ability to extract all gathered data into an external file. To do that, pentesters can configure the utility to listen to the entire network it’s currently in or to listen to one or multiple specified IP addresses.
BetterCAP can be configured by a MAC address and by a specific subnetwork, allowing QA specialists to search for vulnerabilities within a specified configuration.
The utility supports APR and DNS spoofing as well as traffic sniffing with further data extraction into a console or log. The extracted set of data includes:
- Visited URLs and HTTPS hosts
- HTTP POSTed data
- HTTP Basic and Digest authentications
- HTTP Cookies
- FTP, IRC, POP, IMAP, and SMTP credentials
- And more
BetterCAP works with HTTP/HTTPS (SSL Stripping and HSTS Bypass) and TCP proxy, which can be used for manipulating HTTP/HTTPS and low-level TCP traffic in real life. With standard settings, proxies only log requests. But you can configure their settings using a set of modules, or you can add your own custom modules and manipulate traffic in the way you want.
Arpspoof is a utility designed for ARP spoofing in a local network. It sends two requests — one to a server and one to a chosen computer or computers — to receive their MAC addresses, replace the ARP response from the server to the client with itself, and replace the default gateway of the victim with itself or with another IP address. Arpspoof’s main task is traffic sniffing.
Arpspoof supports the launch of third-party scripts. This utility should be considered more as a training program for getting familiar with ARP spoofing rather than a working tool, since Arpspoof has limited functionality, no decrypter, and a narrow field of application.
2. L3 (Network Layer)
At the network layer, the most common MITM attacks are Stateless Address AutoConfiguration attacks and ICMP redirects. Let’s explore how they work.
A Stateless Address AutoConfiguration (SLAAC) attack reconfigures IPv6-enabled networks. Organizational networks that allow for IPv6 but don’t have any settings for it are a common vulnerability. In a SLAAC attack, an attacker provides a prefix to IPv6 hosts, the prefix length, and a default gateway address that doesn’t have a DHCPv6 server. If attackers create their own Router Advertisements (RAs), they can, for instance, become the main router within the network and the entire data flow will go through their computer.
ICMP redirect. One of the reasons to use ICMP is to dynamically change routing tables within a target network. Initially, ICMP was designed to prevent messages from being sent in non-optimal ways as well as to improve network stability. A certain part of a network (that’s connected to the internet) can have several routers. In case one of them is disconnected, the main router sends ICMP requests to all network devices, and the routing tables are rewritten to work under the new conditions.
In an ICMP redirect attack, an attacker either waits for one of the routers to be down or disables it themselves. Then, the attacker starts sending ICMP requests from all routers. As a result, a new network forms in which the attacker becomes one of the network nodes. During an ICMP redirect attack, an attacker can specify that targeted websites should only be accessed through the attacker’s router.
Let’s take a look at several tools used for ICMP redirect attacks.
parasite6. This utility is an ARP spoofer that’s similar to BetterCAP but with limited functionality and minimal settings. It connects to a local gateway and transmits all network traffic. It outputs a message to the console specifying to whom a packet is sent and who must receive it. The parasite6 tool is best used together with utilities that can read packets that go through it.
fake_router6. When launched, this utility sends a signal to the network that specifies that an attacker’s router has the highest priority within the network. The network then reconfigures itself in a way that the final step of entering an external network from the specified subnetwork passes through the attacker’s computer. As a result, all data that initially was sent to the router will pass through the attacker’s computer, on which fake_router6 is installed.
dos-new-ip6. The main task of this utility is to provide fake data to the duplicate address detection (DAD) process during repeated ip6 requests. This gives an attacker an opportunity to create a node inside the network. The node address will be the same as for another network node, still making a controller think there’s only one client with such an address. As a result, data will be sent to both nodes, including the attacker’s.
exploit6. This tool is a vulnerability scanner that sends multiple requests to the targeted computer. It receives responses and outputs data to the console, specifying which known vulnerabilities the target computer has.
thcping6. This utility allows for creating a custom packet for a ping6 request. It allows you to modify the packet size, data type, and other parameters. First, an attacker specifies the set of options for the packet and the target computer. Then, they send a packet and receive a response. By fitting certain packets, malicious actors can make the target system deny to respond to a particular request (sending a response error message). Then, knowing the packet’s characteristics, they can use other utilities to create the same packet but send more than one. This will overload the system, leading to the system’s failure or the failure of one of its nodes.
3. L4+ (Transport Layer)
At the transport layer, attackers can apply Link-Local Multicast Name Resolution spoofing, NetBIOS spoofing, DHCP spoofing, and rogue DHCP spoofing.
Link-Local Multicast Name Resolution (LLMNR) spoofing. If for some reason a Windows client can’t get the host name using DNS, it will try to do so using the LLMNR protocol, sending requests to the closest computers. This technique works through IPv4 and IPv6 addresses.
NetBIOS spoofing. If LLMNR spoofing doesn’t work, attackers can use the NetBios Name Service. It’s similar to LLMNR and is used for the same goal, but it only works for IPv4 addresses. The idea is that if some computer nearby can respond even with false information, the response will be received as valid.
DHCP spoofing. The goal of this attack is to force clients to use the attacker’s host as a default gateway as well as to use DNS and WINdows Internet Name (WINS) servers configured by the attacker. The attacker’s task is to configure a fake DHCP server in the network for sending DHCP addresses to clients and to exhaust the address pool of legitimate DHCP servers.
There are two conditions for a successful DHCP spoofing attack:
- A client receives an IP from an illegitimate server faster than from a legitimate server
- The legitimate server has an exhausted address pool
Rogue DHCP. The main goal of a rogue DHCP attack is to use a fake DHCPv6 server for resending traffic from a victim’s computer to an attacker’s computer. A malicious actor intercepts a DHCP message-request and responds to it, simulating an actual DHCPv6 server.
Here are several tools that can be applied for such L4+ attacks:
Ettercap. This utility is built into Kali Linux. It’s easy to configure and has a graphical user interface, which makes it simple and fast to get familiar with it. Ettercap allows you to execute ARP poisoning, ICMP redirects, port stealing, DHCP spoofing, and NDP poisoning.
When working with Ettercap, you can view, analyze, and even perform some actions with traffic on the fly. It shows you the connection state and allows you to view all data gathered from a chosen connection in text format.
The main drawback of Ettercap is the absence of a data decryption tool. So if a network is secured with encryption, you’ll need to use additional utilities. Ettercap has much weaker functionality than BetterCap, but it can be used for informational and educational purposes.
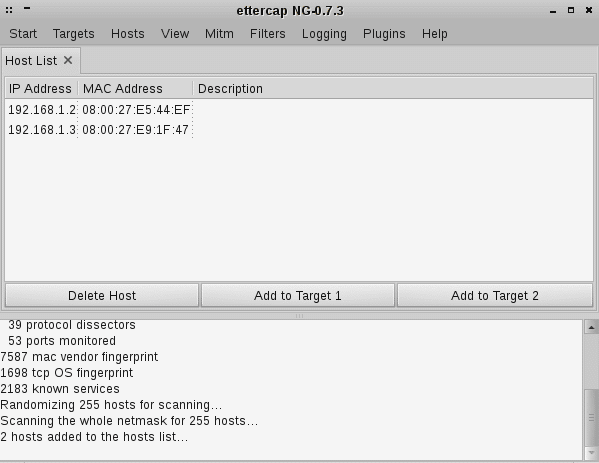
Image 6. Ettercap user interface
Snarf. This utility was designed for working with smb, ftp, and similar traffic types. To work with it, you’ll first need to have a working spoofer (we used BetterCAP). All traffic that goes through the spoofer is resent to Snarf, which picks out traffic responsible for remote connections like smb and ftp. Any other traffic that passes through Snarf isn’t shown on the console or service page.
Snarf outputs information to the console about data destinations, data sizes, hashes, addresses, ports, connection types, and errors. It also shows errors of potential memory leaks. A summary of gathered data is output on the service page in the form of a table with major information about the connection, computer, and system. Also, Snarf provides an opportunity to expire or block connections.
This utility only works for Linux, however, and configuring it can be quite unobvious.
mitm6. This tool listens to the main network interface from the attacker’s computer to intercept requests for IPv6 addresses (by applying DHCPv6 requests) from other computers within the network.
With standard settings, a system (a network of devices connected to a main router) sends DHCPv6 requests on a regular basis. The mitm6 utility responds to these requests with a new address of a victim. In a real-life network, the client’s address would be assigned by the client’s computer in the network, but in the case of mitm6 request interception, the victim’s address will be assigned by mitm6. This gives a malicious actor an opportunity to assign their own computer to be a server. Thus, all the victim’s connections will go through the attacker’s computer.
This only works for Windows, since Mac and Linux don’t use DHCPv6 requests for determining IP and DNS servers. The mitm6 tool doesn’t claim to be a central node, so it doesn’t intercept signals from all computers in the network. Instead, it selectively spoofs specific hosts.
Once a victim receives a new DNS server address, the victim connects to this server, where Web Proxy Auto Discovery Protocol (WPAD) Exploits take place. As soon as the victim’s computer receives the IPv6 attacker’s address as a DNS server, it starts sending requests for WPAD network configuration. For IPv4 or IPv6 requests, an attacker sends their address to the victim.
Then, the attacker has to exchange authentication data with the victim’s computer. Since this can’t be done directly on the victim’s computer, the attacker will simulate a proxy server. As a result, all data typed in for authentication will be sent to both the final server and the attacker. But the victim won’t notice it.
All the tools described above can be used for penetration testing to check network security, detect vulnerabilities, and fix them. In this way, businesses can prevent possible attacks conducted by real cybercriminals and secure their network connections and sensitive data.
Conclusion
In this article, we explored several types of man-in-the-middle attacks and described how cybercriminals use MITM tools to intercept data. During such attacks, victims notice nothing and have a false sense of security. Whether an organization is a small startup or a large corporation, it should establish robust network security.
To prevent MITM attacks and secure both your data and your network connections, you can simulate attacks using specialized utilities, identify weak spots, and fix them. At Apriorit, we have a dedicated team of pentesters who are ready to help you establish robust security for your networks and IT products. Contact us now to start discussing how to enhance your cybersecurity.



