The average luxury car contains more lines of code than the Boeing 787 Dreamliner, F-35 Joint Strike Fighter, and F-22 Raptor combined. This amount of code is the engine that pushes the automotive industry forward, but it also exposes it to new vulnerabilities and cyber risks.
Car hackers and thieves keep up with automotive software developments and create technologically advanced ways to steal vehicles. Therefore, manufacturers also have to innovate to protect their vehicles from cyber attacks.
The first step towards protecting automotive software is comprehensive security testing, which helps to detect vulnerabilities in a vehicle’s code at early stages of development. But conducting effective security testing requires knowledge of industry requirements, challenges, and best practices.
In this article, we discuss why automotive cybersecurity testing is so important and share valuable tips on how to secure your software. This text will be helpful for product managers and development leaders looking for ways to secure their automotive software with proper quality assurance activities.
Why pay attention to vehicle software security?
Modern cars are no longer standalone mechanical systems, but a variety of numerous electronic control units (ECUs). Cars use complex software to ensure the safety of vehicle occupants and other road users, enable autonomous driving, entertain passengers, perform diagnostics, and so on.
These capabilities are appreciated by car buyers, which is why demand for automotive software is constantly growing. McKinsey estimates that the market for automotive software and electronics will grow from $238 billion in 2020 to $469 billion in 2030.
However, the complexity of modern automotive software can lead to vulnerabilities, which developers may miss when deploying their products. And the popularity of such solutions may attract more hackers to try to break those systems to obtain valuable user data.
1. Comply with standards, regulations, and laws
To improve security and prevent hacks, many governments and international organizations are working on guidelines and requirements for developing secure automotive software. Aligning your software with cybersecurity standards for the automotive industry is one of the first steps towards ensuring proper security.
Consider exploring the following standards, regulations, and recommendations to implement security best practices while working on in-vehicle solutions:

- Cybersecurity Best Practices for the Safety of Modern Vehicles by the US National Highway Traffic Safety Administration. These practices are non-binding and may change over time.
- UN regulations numbers 155, 156, and 157 describe requirements for vehicle cybersecurity, security management, and software updates and became mandatory for UNECE Member States in July 2024.
- Draft Provisions on Management of Automotive Data Security by the Cyberspace Administration of China.
- ISO/SAE 21434. This ISO standard is currently under development and will be non-binding. It describes best practices for the development, production, operation, maintenance, and disposal of vehicles.
- SAE J3061. This guidebook by SAE International contains recommended practices for designing and developing vehicle systems to protect them from hacking attacks during a vehicle’s lifetime.
Need to secure your automotive systems?
Partner with Apriorit to protect your automotive innovations with top-tier security testing and stay ahead of potential threats.
2. Prevent and mitigate attacks
While innovative software pushes the automotive industry forward, it also makes cars more vulnerable to hacking attacks. Hackers may abuse poorly protected automotive software to steal or take control of:
- Vehicle owners’ personal data and finances
- Cargo shipped by compromised vehicles
- Vehicles themselves
In May 2021, two security researchers hacked a Tesla Model X in just 40 minutes using a drone equipped with a Wi-Fi dongle. The researchers could open and close the target car’s doors, change driving and acceleration settings, and so on. And that’s not the first Tesla hack, despite the fact that the company pays a lot of attention to cybersecurity.
In 2022, security researchers discovered lots of vulnerabilities in vehicles from 16 carmakers, including Honda, Hyundai, Kia, Infiniti, Nissan, and Porsche. Some of the discovered weaknesses allowed researchers to control car functions and start or stop the engine. Moreover, researchers managed to access the VIN numbers of several vehicles, which provided them with access to names, addresses, phone numbers, and email addresses of car owners.
Another widespread security breach allowed hackers to break into cars equipped with keyless entry systems. In Columbus, Ohio, hackers simulated signals from key fobs and stole 43 cars from the same neighborhood in two months. They did it without triggering the cars’ alarms or even touching key fobs.
To sum up, insufficient security measures during automotive software development may result in lots of potential risks, including:
- Fines and penalties for non-compliance
- Additional spending on urgent security updates
- Loss of customer trust
- Reputational losses for manufacturers
- Theft of vehicles and cargo
- Endangerment of riders and other road occupants
Going the extra mile when ensuring vehicle software security is crucial for automotive software developers. As vehicles become increasingly software-centric, the complexity of their systems grows, necessitating a robust approach to managing associated risks.
All these reasons prove that ensuring proper software security should be a top priority for car manufacturers, logistics companies, and automotive solutions engineers. One key step towards ensuring strong protection is adding security testing activities to the development process.
Why apply security testing to protect automotive software?
Designing automotive software with cybersecurity in mind decreases the probability of car hacking and associated risks. One way to check if your solution meets key requirements of relevant security standards and guidelines is by running a thorough security test of your automotive software at different stages of its development.
Automotive security testing can help you achieve several cybersecurity goals:
- Identify potential software vulnerabilities
- Test the protection of your solutions against relevant attack vectors
- Check automotive software for unexpected behavior
- Ensure correct integration of multiple software components
Assessing cybersecurity in the automotive industry helps to check that all protection measures are working properly, detect vulnerabilities early, and reduce the risks we mentioned earlier.
To enhance your system’s protection, you can also apply penetration testing for automotive cybersecurity. Unlike security testing, penetration testing (or pentesting) simulates real-life attacks but in a way that doesn’t hurt the current software or endanger user data. Let’s take a quick look at what pentesting is and why we use it for automotive solutions.
Penetration testing in the automotive industry
Automotive penetration testing emulates an attack on automotive software in an attempt to find any vulnerabilities and assess the potential damage from an attack. Pentesting services can be provided by an in-house security testing team that knows the software well or by an outside team that can analyze your product from a new angle.
Conducting penetration testing can help your team:
- Detect even more vulnerabilities in vehicle systems and address them proactively before hackers can exploit them
- Identify weak spots within the software that are prone to break under attacks
- Assess the protection of user data and other sensitive and confidential information that’s processed by software or stored in its components
- Find out how systems behave during different attack scenarios to check whether built-in protection measures work as intended or need to be updated
- Ensure continuous improvement of the software security posture, as regular testing helps software to adapt to evolving threats and vulnerabilities
- Increase customer trust by showing that software passes regular penetration checks, ensuring that systems remain resilient against cyberattacks
When conducting pentesting and security testing of automotive systems, it’s important to ensure that software isn’t susceptible to common attack vectors. In the next section, we take a look at the eight most common vectors of attack against modern vehicles.
Read also
12 Common Attacks on Embedded Systems and How to Prevent Them
Discover vulnerabilities of embedded systems and effective strategies for protecting against them. Read on to find insights for securing your devices against common threats and enhancing your project’s resilience.

Common attack vectors for automotive software
The average car contains more than a hundred ECUs that run some sort of software, and hackers can attack any of these. However, cybercriminals are mostly interested in the parts of a vehicle that grant them access to valuable data or hand over full control of the entire vehicle.
Let’s look at the key attack vectors for automotive software:
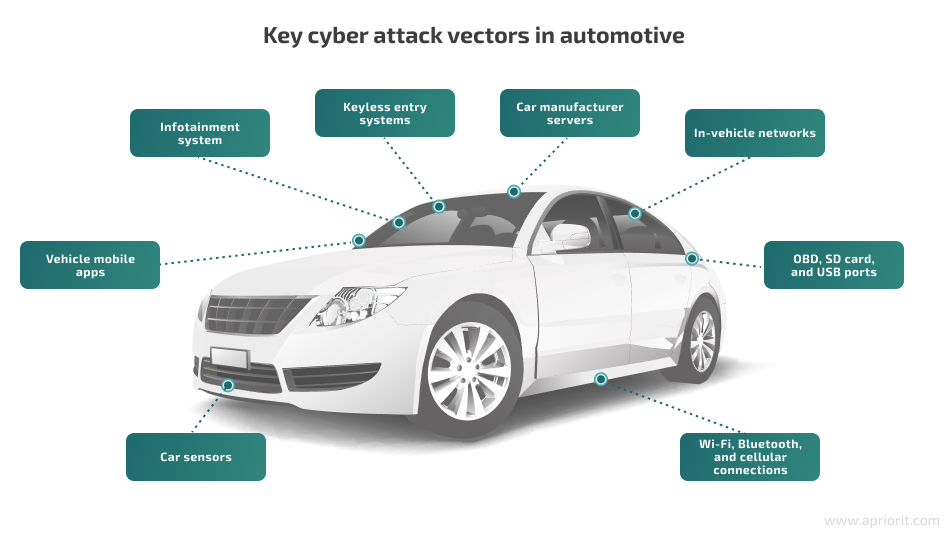
Keyless entry systems. Many modern vehicles use a keyless fob instead of a traditional key. This fob transmits a short-wave radio signal, and when the car’s receiver picks it up, it unlocks the doors, starts the engine, or initiates some other action. Key fobs are convenient for drivers, but they’re also easy for criminals to abuse. Car thieves can use a relay device to transmit a signal from the fob to the car, even if they are far apart. In the UK, 60 to 65 percent of the approximately 33,000 car thefts in 2023 were keyless.
Vehicle mobile apps. Mobile apps offer drivers improved navigation, climate control, autonomous parking, remote unlocking, entertainment, and lots of other convenient features. They can also be used for car sharing and fleet management. However, hackers may compromise these features by bypassing the app’s signature verification system, installing their own signature, and providing an application with root access. And through a compromised vehicle mobile app, criminals can steal credentials saved in the app and further abuse both the vehicle and any devices synchronized with it.
Car manufacturer servers. Automakers’ servers process all communications both inside and outside a vehicle, including communications with drivers’ mobile devices as well as other vehicles. That’s a lucrative attack surface for malicious actors. Attackers can infect a target server with ransomware, intercept transmitted data, or perform a denial of service (DoS) attack. In this way, hackers can steal sensitive data or disrupt the work of automotive services. In 2022, Kojima – one of Toyota’s major suppliers – had one of their servers infected with a virus. As a result, Toyota shut down production lines at 14 factories for a day.
Car sensors. Sensors collect information on the environment around a car, such as the weather, road markings, tire pressure, engine RPMs, and oil temperature. Using sensor spoofing or signal jamming, hackers can change a vehicle’s behavior. They can also capture sensor signals and reverse engineer them to learn about a car’s internal systems.
Infotainment system. This system provides a driver and passengers with useful information and entertaining content. Infotainment systems accumulate tons of personal data: account credentials, browsing histories, travel itineraries, and personal preferences. Malicious actors can intercept traffic from an infotainment system and mess with its settings. In this way, they can steal a driver’s sensitive data.
Wi-Fi, Bluetooth, and cellular connections. Network connectivity systems can become entry points to the infotainment system for hackers. From there, hackers can access critical car components, influence vehicle behavior, or steal transmitted data. By compromising network connections, hackers can even attack several cars at once.
In-vehicle networks. These networks consist of ECUs and control area network (CAN) buses that work in real time. By design, ECUs and CAN buses first accept any data, then validate it and send it to other vehicle components. If software developers don’t implement data encryption at this point, hackers can take advantage of this data processing mechanism. They can abuse it and flood in-vehicle networks with packets of garbage data, creating a DoS attack, or sniff the traffic and extract sensitive data from it.
On-board diagnostics (OBD), SD card readers, and USB ports. Attacking in-vehicle OBD or USB ports is a less widespread type of attack, since it requires physical access to a port on the target vehicle. However, attackers can do a lot of damage via in-vehicle ports: inject devices with malware, take control of a vehicle, hijack network traffic, or get access to various vehicle components.
As you can see, these attacks often target specific weaknesses and vulnerabilities hidden in automotive software and embedded in-vehicle systems. To make sure that cybercriminals won’t be able to take advantage of your automotive software solutions, you need to make sure you detect and address these security issues before you release your product to the market. And this is where automotive security testing comes into play.
Read also
Artificial Intelligence in the Automotive Industry: 6 Key Applications for a Competitive Advantage
Explore how artificial intelligence is revolutionizing the automotive sector. Discover cutting-edge AI solutions that enhance vehicle performance, safety, and the driver and passenger experience.
7 best practices to test automotive cybersecurity
To verify the security of your automotive software, consider following these seven best practices:

1. Follow the latest cybersecurity requirements. By aligning your software with the industry’s strictest security standards, you can avoid legal issues and improve your software’s competitiveness. Make sure your team also pays attention to recommendations that are still under development or discussion. Since the vehicle production cycle lasts several years, you might need to take these requirements into account during pre-release security testing.
2. Synchronize production, development, and testing. Automotive security needs to be tested in parallel with software development and car production processes. This way, a security testing team can detect vulnerabilities during development and avoid major code rework. It’s also important to test security and software behavior on physical vehicle hardware. To synchronize these activities, you can implement flexible project management approaches like Agile and Scrum.
3. Apply fuzz testing. Injecting vehicle software components with random data and looking for glitches is an efficient security testing technique called fuzz testing, or fuzzing. Fuzz testing is a reliable way to find hackable bugs and code errors which, if left unaddressed, may lead to software crashes, behavior changes, and memory or data leaks, or that may even serve as potential backdoors.
4. Analyze software composition. Automotive software is often developed by several third-party vendors that use open-source code to deliver components in time. Some of those open-source components may contain known vulnerabilities and become an entryway for malicious actors. Manually discovering all open-source libraries and solutions used to build your automotive software is extremely time-consuming and subject to human error. Software composition analysis tools can do that automatically for your testing team.
5. Pay extra attention to integration testing. Considering how many automotive software components are developed by different teams or even organizations, there’s a high chance of unexpected interactions between them. These interactions can hide potential threats, such as establishing an unprotected connection or accepting data from unknown sources. That’s why automotive software requires careful integration testing of all components.
6. Update your software regularly. Hackers will more likely target cars with outdated software because they already know everything about security vulnerabilities in that software. That’s why you need to periodically test your code against new types of attacks and roll out security updates.
7. Generate a software bill of materials (SBOM). An SBOM is a detailed list of the components and dependencies in software, helping development teams improve software management and mitigate vulnerability-related risks. In the automotive industry, SBOMs are vital as they show all details about each system’s components and allow the system to centralize vulnerability management. Security testing teams can also leverage SBOMs to see which system parts require testing in the first place and what vulnerabilities to look for, and to provide valuable insights to developers.
Following these best practices will help you optimize the security testing process, detect more vulnerabilities in code, and release secure software. However, there are several challenges with testing the security of automotive software that you need to be aware of. Let’s take a look at them.
Related project
Developing Software for a Drone Battery Charging and Data Management Unit
Discover how our team developed an advanced embedded and mobile solution for drone management. Learn how we helped our client streamline drone charging and effortlessly manage gathered data.
Challenges of security testing in automotive
With unique testing conditions and practices come unique challenges your QA team may face. Part of these challenges are related to integral characteristics of the automotive industry that you need to take into account while planning security testing. However, some can be mitigated or even avoided with the correct approach to testing.
Let’s take a look at the key challenges of conducting security testing on an automotive project and ways to deal with them.

1. Lack of specific testing expertise. Full-scale security testing of automotive software includes checking the protection of embedded, IoT, mobile, virtual, cloud-based, and client–server systems. Advanced automotive systems can also employ artificial intelligence (AI) algorithms for predictive maintenance and autopilot functionality. Using AI in the automotive industry helps carmakers speed up design, production, and manufacturing processes while improving vehicle and software quality. Security testers and testing teams with expert skills in all of these areas are extremely rare. That’s why it can be a challenge to create a full-stack team in-house or quickly hire an engineer with the required skills. One solution to this challenge is to look for outsourcing teams that possess the needed expertise.
2. Lack of physical hardware for testing. To avoid accidentally causing harm to vehicle-related software running on real-life devices, security testing specialists use virtual machines. However, virtual machines may not show all potential vulnerabilities when code is running on real-life hardware. Thus, to achieve comprehensive test coverage, they still need access to physical devices. The problem is that buying such hardware not only requires additional money but also time, as hardware is usually produced according to the car manufacturing schedule. Therefore, your team has to put lots of effort into flexible project management and synchronizing testing activities with car production to avoid waiting for hardware manufacturers.
3. Need to swiftly test over-the-air (OTA) updates. When a development team pushes a security update, the testing team has to put aside planned tasks and focus on it. They have to ensure that the update fixes discovered vulnerabilities and doesn’t create new ones when launched on real-life hardware. That’s a great amount of work that has to be done as quickly as possible. This is why security testing of OTA updates has to be done by a highly flexible team that can easily adapt to new tasks.
4. Poor development standardization in the supply chain. Car manufacturers work with hundreds of suppliers that develop vehicle hardware and software components. Maintaining consistent standards across the supply chain is almost impossible. Suppliers use languages, operating systems, open-source components, and hardware parts that allow them to deliver their products in time and at the lowest possible cost. This creates additional pressure on the security testing team, which has to conduct extensive integration and compatibility testing to search for vulnerabilities in third-party code.
5. High level of required test coverage. Test coverage metrics are essential for automotive software. The percentage of code covered with tests and the percentage of requirements that aren’t implemented in code can indicate potential security vulnerabilities. Quality assurance engineers also pay attention to test coverage to identify and learn from useless test cases. Unfortunately, achieving a high level of test coverage requires a lot of time-consuming manual work from the testing team, as there are few automated security testing tools to measure coverage of automotive software. Manually evaluating coverage also leaves room for human error.
Conclusion
Automotive software makes vehicles safer, more comfortable, and more manageable. Unfortunately, it also makes them targets for hacking. Malicious actors can abuse a car’s software to obtain personal data, steal or damage a vehicle, or harm the manufacturer’s servers.
Thorough automotive cybersecurity testing helps you detect vulnerabilities before hackers can. In the automotive industry, software security testing has to be conducted by a QA team with deep expertise and understanding of the industry, as there are many unique requirements, best practices, and challenges to take into account.
Security testing teams at Apriorit have vast experience working in many industries, applying different technologies, and working with unusual requirements. Our quality assurance engineering and security testing experts are ready to help you enhance the protection of your automotive software.
Need a team of cybersecurity experts?
Let’s make your software more secure, resilient, and reliable!



