
Using Kali Linux for Penetration Testing
Learn from Apriorit experts how to use Kali Linux for penetration testing and what tools work best with this Linux distribution.


Learn from Apriorit experts how to use Kali Linux for penetration testing and what tools work best with this Linux distribution.

In this article, we explain how you can debug your Linux kernel and its modules during runtime.

Read this post to learn what web debugging proxies developers and testers at Apriorit prefer and how to work with these tools.

Learn about the recently discovered bug in EOS smart contracts that allows hackers to allocate RAM and how to get your RAM back.

Shield your company’s application with our expert security testing services. Uncover vulnerabilities, fix issues, and fortify your defenses before a...

Meet the second part of our series on hooking Linux kernel functions with ftrace.

Meet the first part of our series dedicated to hooking Linux kernel functions using ftrace. Explore four helpful approaches to use for your solutions...

This article describes the ways ransomware can infect the cloud and how can you protect your cloud-based systems from such a devastating threat.

This article covers the implementation of forensic features in SIEM solutions and the key requirements to ensure admissibility of data in court.

How we have increased mhook’s performance, enhanced its capabilities and eliminated certain bugs.
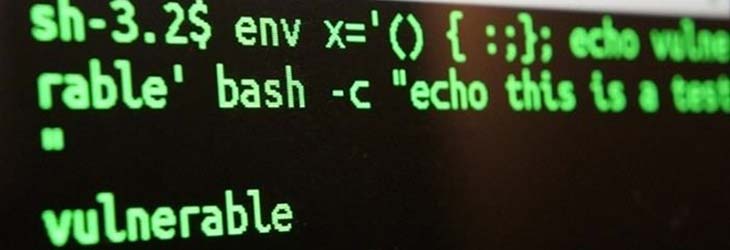
Learn how to protect your application from ever popular stack overflow exploits

An overview of main mobile information security issues, with some suggestions on how to deal with them
Tell us about
your project
...And our team will:
Do not have any specific task for us in mind but our skills seem interesting? Get a quick Apriorit intro to better understand our team capabilities.